This is very helpful information, thanks! The ultimate goal is indeed to use a loader similar to what TobEx has; the alpha uses a hardcoded loader simply because it was faster to implement.
IWDEE can most certainly be supported as it is running the same fork of the engine as BGEE and BG2EE, (finding equivalent code shouldn't be too hard). PSTEE's engine, on the other hard, is so different from the others that it might not be possible to translate modifications over.
I'll see what I can do.





I've been looking at EEex and the hardcoded patches to the bg2ee baldur.exe.
Using this pattern:
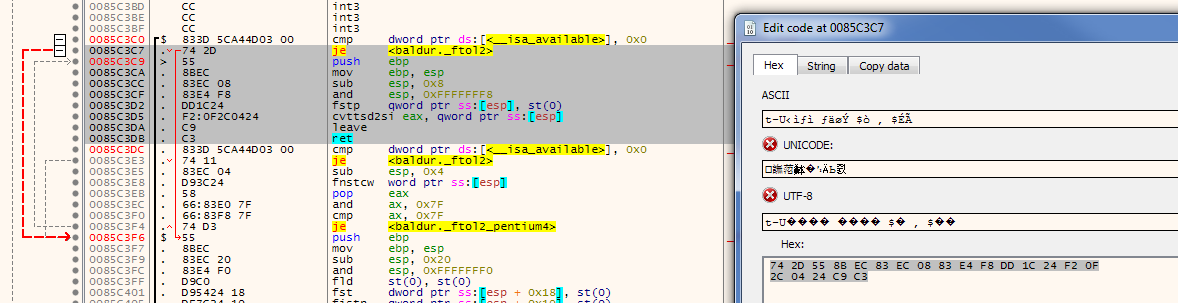
FF35????????E8????????83C43085C075145050506AFF50FF35????????E8????????83C4186A00And searching with that pattern in x64dbg: Right click menu->Search For->Current Module-Pattern. Paste pattern. Double click on the single reference found will bring you to the correct location for
luaL_loadstring, which is replaced in the EEex patches to jmp to the codecave.I think it might be possible to support the other enhanced games and possibly other versions. I tried the pattern matching with some older versions of bg2ee and bgee, some have the pdb to verify its the luaL_loadstring location. Only one really old version didnt locate the pattern - it did have the pdb but there was no luaL_loadstring reference in that build.
Here are some attached screenshots to show the pattern matched location:
BG2EE: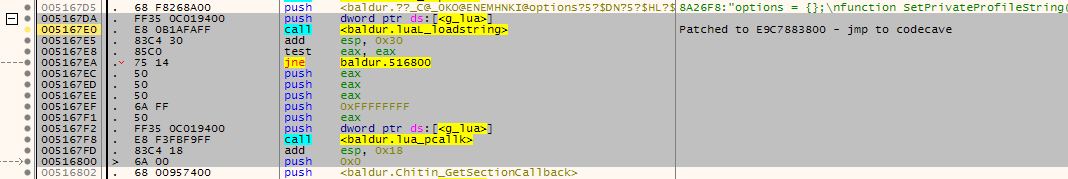
BGEE: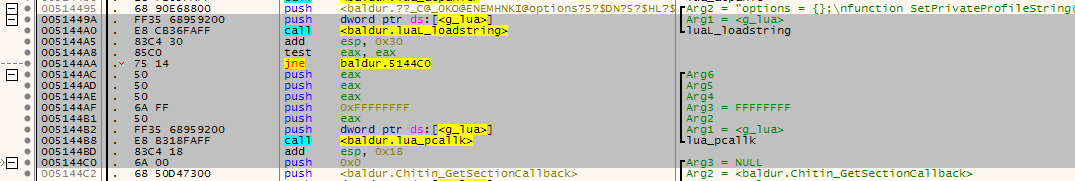
IWDEE: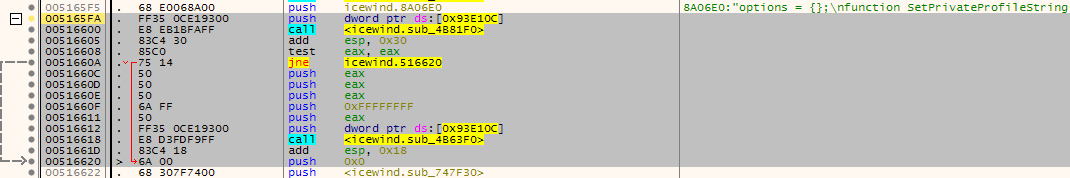
PSTEE: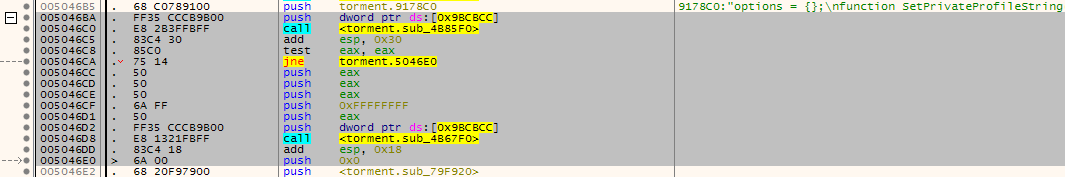
The ones without the pdb (IWDEE and PSTEE) do show similar calls to the api call
SetPrivateProfileStringbeforehand.I might be possible to build a loader - similar to the TobEx loader - that can apply the basic patches on the exe in memory instead of the exe file. Or the pattern might be useful to match with weidu (if it supports this) to support the other EE games if you prefer the hardcoded patches.
The codecave location and other asm code would need to adjusted for each EE game. A search for a codecave in memory with the reasonable size should be possible to code. The only other issue would be to locate the
lua_pushnumber,lua_setglobal,lua_pushclosure,lua_tonumberx,lua_tolstringand_ftol2_ssecalls so that they can be properly coded in and the additional asm instructions adjusted according to their location and the codecave code location.Just thought it might be worth mentioning. Hope that info helps.