I found two information leakage vulnerabilities in MiniCMS, you need to login the backstage first.
The first one reveals the web root files on the web server:
Steps to reproduce:
1、Login in to the backstage http://192.168.232.181/MiniCMS-master/mc-admin/
2、Post an article
3、Checked the page and see
4、The url will direct to the following...
We can see all the files locate in web root the the server.
The second reveals the real path of the MiniCMS files
Steps to reproduce
1、Login in to the backstage http://192.168.232.181/MiniCMS-master/mc-admin/
2、Post an article
3、Try to re-edit this page, actually this page is save as iabl13.dat
we can see :
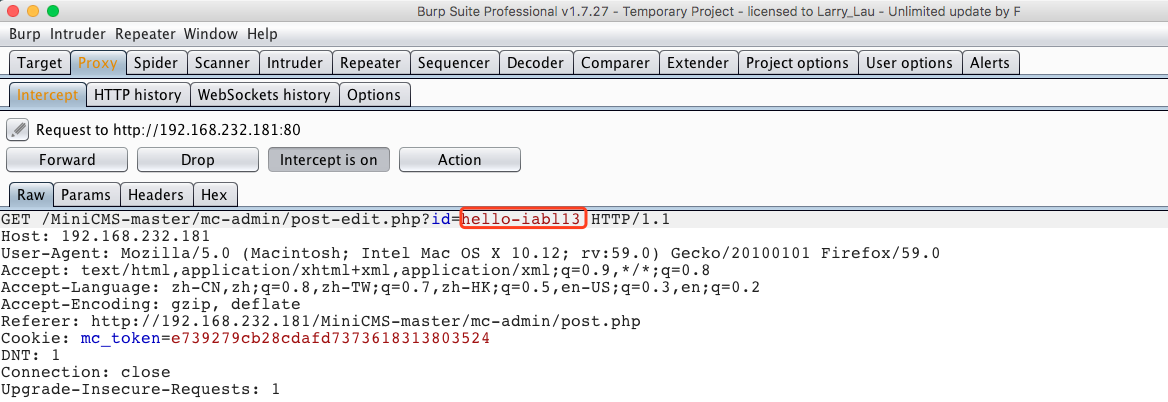
4、Using burp to intercept this request
the original id is iabl13, and we change to hello-iabl13
5、Actually hello-iabl13 is not really exists, error occurs
This vulnerability reveals the full path of MiniCMS
I found two information leakage vulnerabilities in MiniCMS, you need to login the backstage first.
The first one reveals the web root files on the web server:
Steps to reproduce:
1、Login in to the backstage http://192.168.232.181/MiniCMS-master/mc-admin/ 2、Post an article 3、Checked the page and see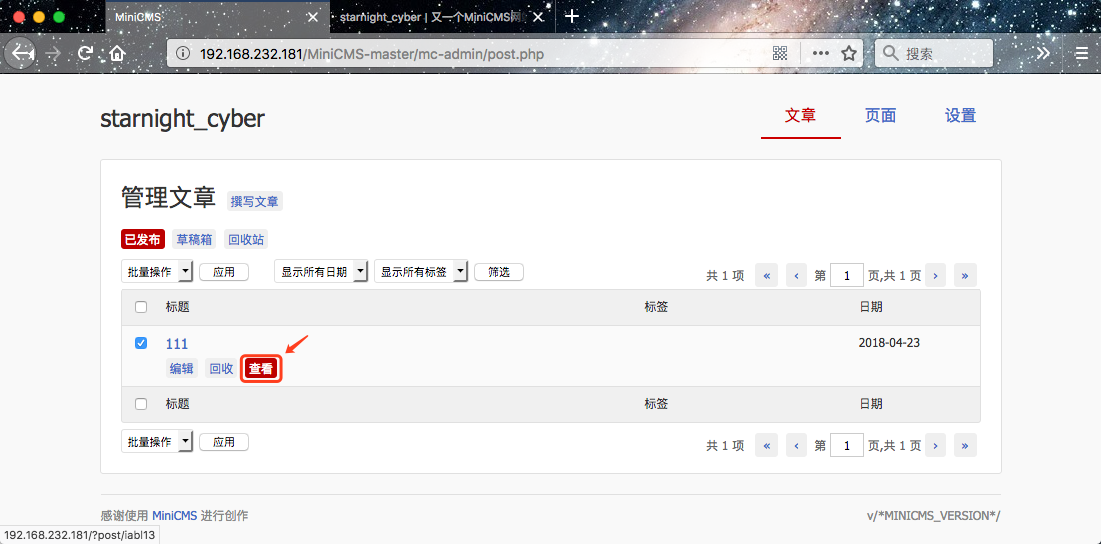 4、The url will direct to the following...
4、The url will direct to the following...
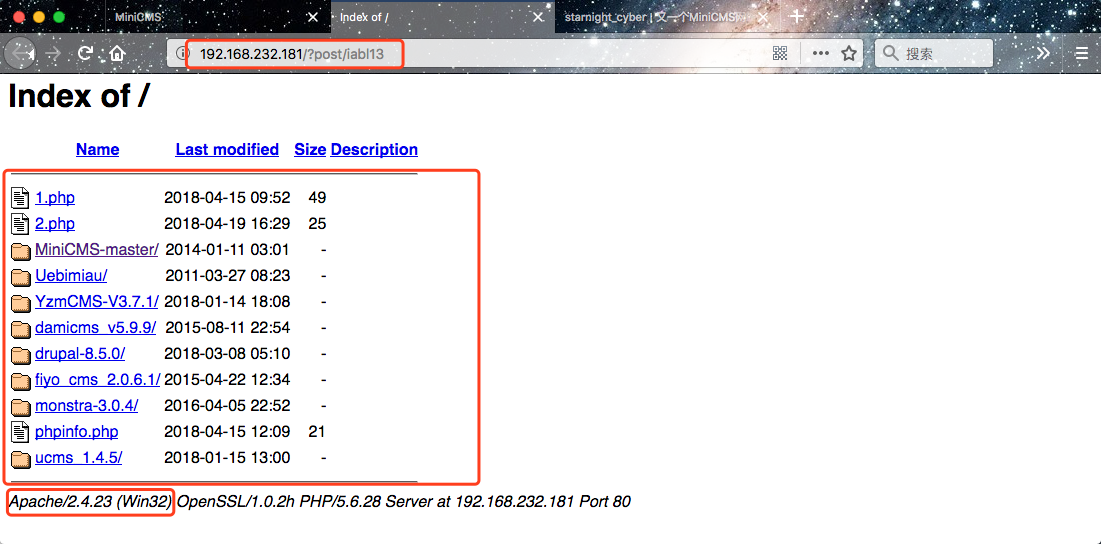 We can see all the files locate in web root the the server.
We can see all the files locate in web root the the server.
The second reveals the real path of the MiniCMS files
Steps to reproduce
1、Login in to the backstage http://192.168.232.181/MiniCMS-master/mc-admin/ 2、Post an article 3、Try to re-edit this page, actually this page is save as iabl13.dat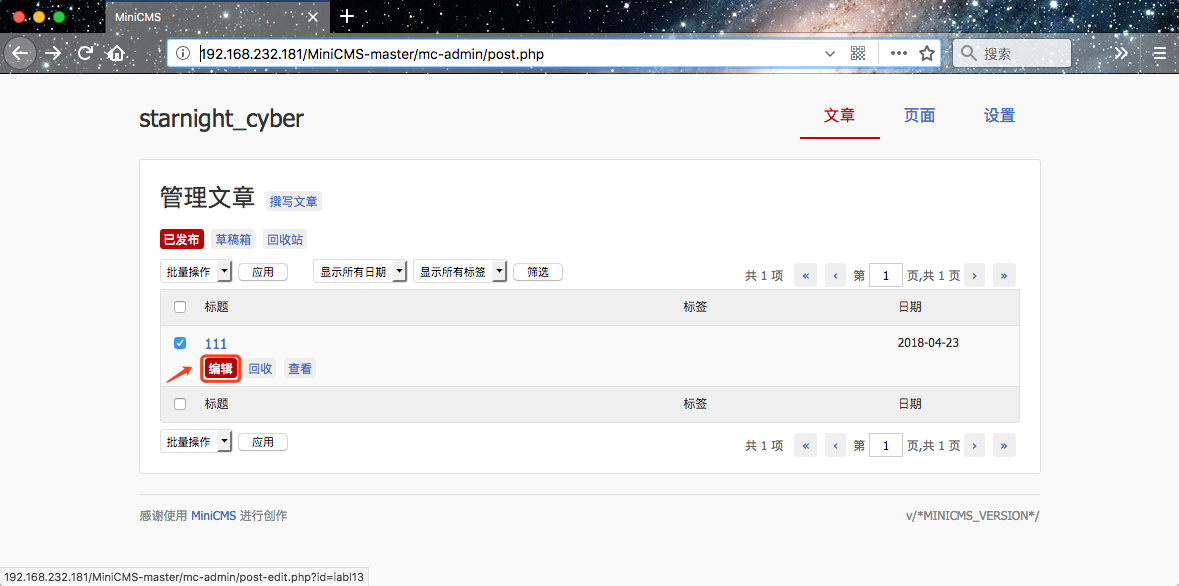 we can see :
we can see :
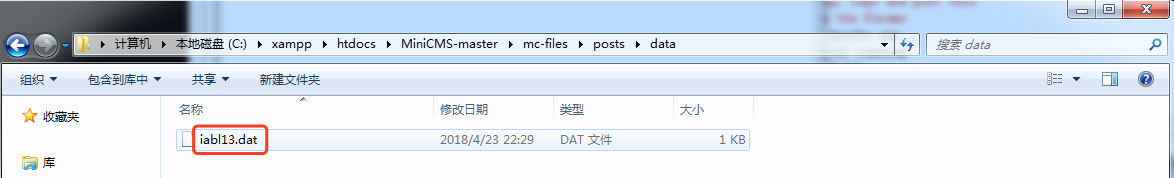 4、Using burp to intercept this request
the original id is iabl13, and we change to hello-iabl13
4、Using burp to intercept this request
the original id is iabl13, and we change to hello-iabl13
 5、Actually hello-iabl13 is not really exists, error occurs
5、Actually hello-iabl13 is not really exists, error occurs
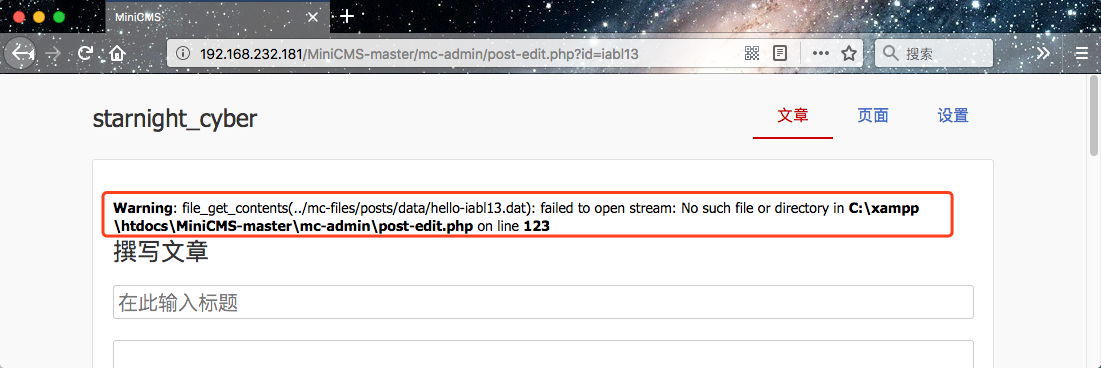 This vulnerability reveals the full path of MiniCMS
This vulnerability reveals the full path of MiniCMS