Hey !
Thanks for your input, nice blog post (although there are some typos left), and the Dockerfile is a good idea for people not wanting to deploy the whole Go environment on their machine.
There's still one thing left before I can merge this: the current Makefile generates a random self-signed certificate (with the depends target), but in the end someone could want to use a trusted one (let's say via Let's Encrypt). It would be nice if you could support this somehow.
One way you could do this is to mount a Docker volume with the generated files. Is this something doable from your point of view?
Thanks !
Coucou o/,
Added a Alpine-based Dockerfile. It launches a lightweight golang HTTP server so it's easy to retrieve the generated content.
The Dockerfile fetchs the latest release using a
go get.I wrote a quick article about the Dockerfile.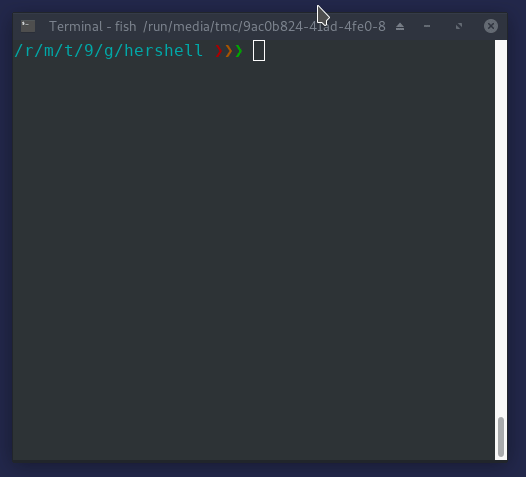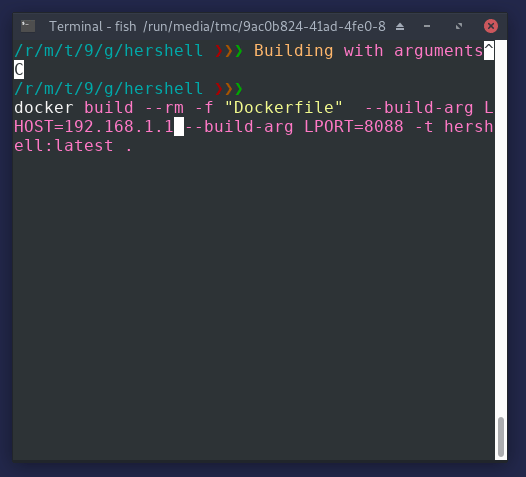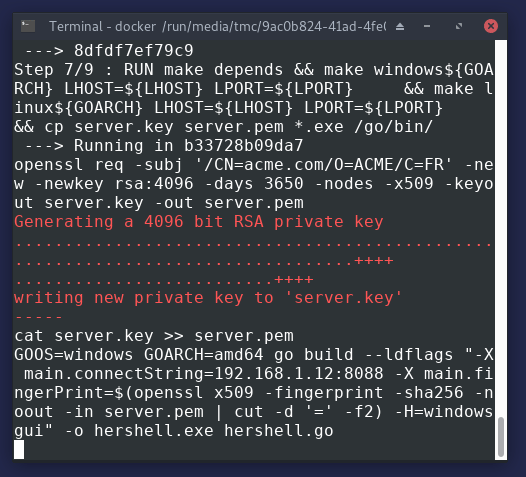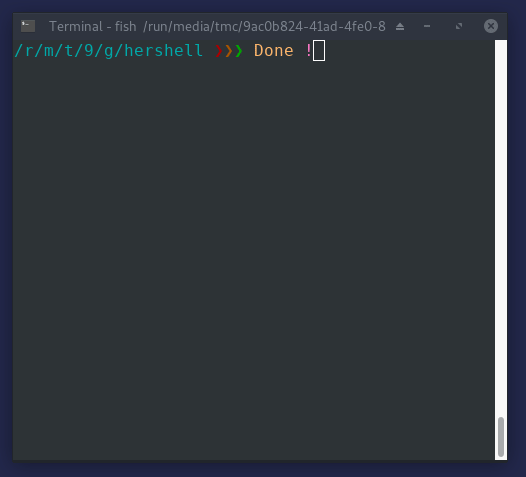
I hope you find it useful :smile_cat: Best regards,