Thanks for filing this interesting issue! I've just solved this (e64d9d93a40c7), the important lines are here. All it does is detect when a message has reached the buffer size and allocates a new, larger buffer. It also throws a warning because if it is constantly doing this silently, there is probably a larger issue. It's not a perfect solution, but it works well.
This will grow forever, which is a pretty big security concern actually. Just spam the server huge messages and it will gobble up all it's memory. I've just addressed that here: 8947e773d
Now, a client can send a large message. If it is larger than the clients current buffer, their buffer will grow by 1024 bytes. If there is still not enough room, it will continue to grow in increments of 1024 bytes. If the buffer grows to be over maximumBufferSize then the server will disconnect the client, because it could be an attack. By default, maximumBufferSize is 10240 bytes. This process can be shown in the log below: 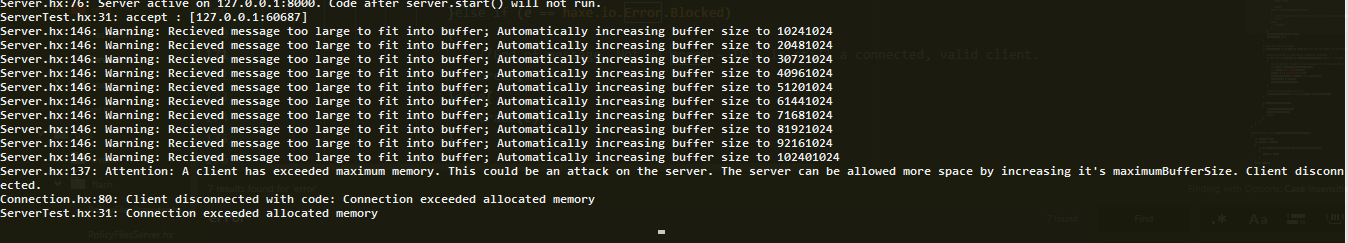
Let me know if that fixes things!
Hi there!
I have problem with reading the socket on the server side.
The problem occurs when the socket reads all the byte data into the socket and stores it in a buffer (array) limited by 1024 bytes (for example). However, if the client send a 720 byte message and then a 1024 byte message, the server would not have had time to read the first 720 byte message, this it will cut the second message because it cannot store 1024 bytes and after the 720 bytes.
It is a rare problem that occurs in situations such as spamming log data.
soft example : first message "foofoofoo" second message "randrandrandrandrand" the server read :
1 / "foofoofoorandrand" 2 /"randrandrand"
So, the deserializer don't understand these messages, and we lose it
I suggest 2 solutions :
soft example with start byte 888 and end byte 999: 1 - "888foofoofoo999" 2 - "888randrandrandrandrand999"