Any other idea how to get the RTSP to work?
@EliasKotlyar have you tried opening the camera? I've seen some pictures of tuya based cameras that had a serial port at 57600 baud. Maybe thats your way in. Then you can browse on the filesystem and probably find something usefull.
 Yeah, if you power the write enable pin you can flash using this programmer, it is called a ch341a programmer. That is how I got the dump file. The hard part is editing the hash and re-compiling the bin file to be the exact size and page size with the boot instructions put in the right place. I don't know how to do that due to aligning partitions and other things that can go wrong super easily. The flash chip is designed for multiple writes, but it wears out after about 30 full flashes so I want to do it sparingly. I will give it a whack though. Set the password to something like 123 and flash it back. It is probably similar to the ddwrt custom firmware stuff. I will check it out.
Thanks for helping with the hash cracking by the way! Let us know if you make a breakthrough?
Also, I am a bit busy this week, but I still plan on working on this. I want to be able to play with facial recognition from a WiFi camera as a senior project.
Yeah, if you power the write enable pin you can flash using this programmer, it is called a ch341a programmer. That is how I got the dump file. The hard part is editing the hash and re-compiling the bin file to be the exact size and page size with the boot instructions put in the right place. I don't know how to do that due to aligning partitions and other things that can go wrong super easily. The flash chip is designed for multiple writes, but it wears out after about 30 full flashes so I want to do it sparingly. I will give it a whack though. Set the password to something like 123 and flash it back. It is probably similar to the ddwrt custom firmware stuff. I will check it out.
Thanks for helping with the hash cracking by the way! Let us know if you make a breakthrough?
Also, I am a bit busy this week, but I still plan on working on this. I want to be able to play with facial recognition from a WiFi camera as a senior project.

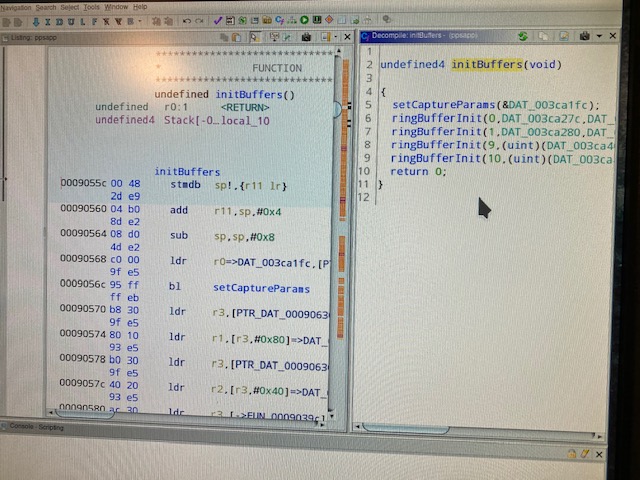


I was wondering if the Tuya Security Camera's may be possible. They work within the same app and I am able to get id and key in the normal manner. I tried to get the signature but don't see it in my logs. I bought the Mercury Security Camera from Walmart. It adds to the Tuya App like everything else. Would it be possible? What can I provide to help if it would be possible.