Something I rediscovered while looking at this is #1148, which causes init to fail if you have a default subscription set that is inaccessible (this can happen if you used you work account and then switch to a personal account as we that that id). You can remove the saved value with azd config unset defaults.subscription
Output from
azd versionazd version 0.5.0-beta.3 (commit 1c23678aade587d5b9685a256a3c1d2d7f4b42e0)
Output from
az versionDescribe the bug
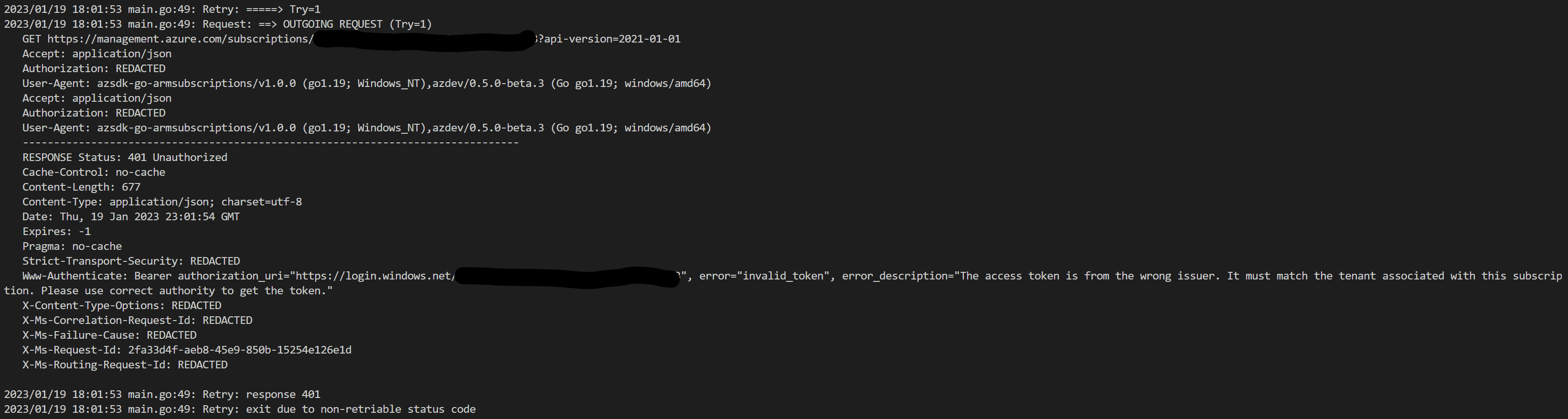
This is a follow up issue to #1366. Although the login is now possible (flow works personal account), the
azddoes not fetch the subscription:I just have the option "other" to enter the data manually.
Switching back to the old behavior via
azd config set auth.useAzCliAuth true, I get the list:To Reproduce
azdi.e., 0.5.0-beta.3azd loginagainst a personal accountExpected behavior
azd initafterazd loginshould show the available subscriptions of the account as in previous versions ofazdEnvironment
Additional context
n.a.