I am unable to reproduce this, but I did experience this some time ago (maybe a year), but found a workaround, using -DefaultProfile, (I turned off some of the debug output, and changed it so that I only get an error back (if any)
This was mostly in Azure Function App that uses runspaces, so your mileage may vary.
I actually just yesterday wanted to write a blogpost on this and found that I did not need to use -DefaultProfile anymore. I did a loop of 50 iterations queuing 5 jobs in each, and got this error 2-5 times each.
I worked with runspaces the entire day and did not see this error once.
Try below out and see if that makes a difference.
$Global:ErrorActionPreference = 'Stop'
$DebugPreference = 'SilentlyContinue'
$AzContext = Get-AzContext
$Jobs = @()
$Jobs += Start-Job -ArgumentList $AzContext -ScriptBlock {
param($AzContext)
# $DebugPreference = 'Continue'
try {
$null = Get-AzVm -DefaultProfile $AzContext
}
catch {
$_
}
}
$Jobs += Start-Job -ArgumentList $AzContext -ScriptBlock {
param($AzContext)
# $DebugPreference = 'Continue'
try {
$null = Get-AzVm -DefaultProfile $AzContext
}
catch {
$_
}
}
$Jobs | Wait-Job | Receive-Job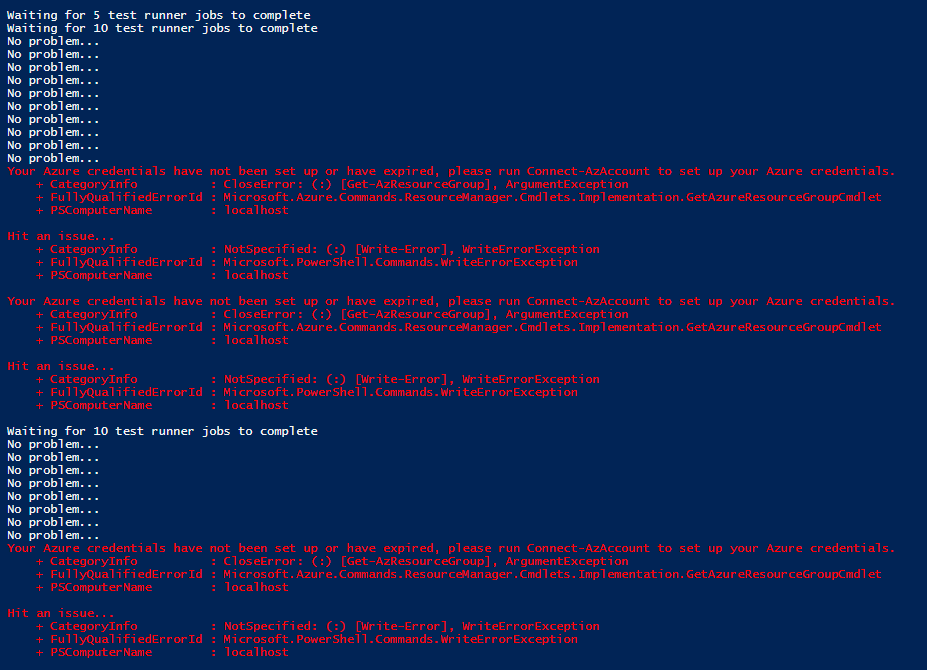



Description
This issue is very similar to several previous issues here, here, and here. When passing the current Azure context to the Start-Job command, the first job that completes will often fail with the error message, "Your Azure credentials have not been set up or have expired, please run Connect-AzAccount to set up your Azure credentials". Subsequent commands complete successfully.
Steps to reproduce
Finding a way to consistently reproduce this has nearly drove me mad. I fully realize the steps below may seem oddly specific, but what I've outlined is the only way I've been able to reliably and consistently reproduce the issue. There may very well be a better way to reproduce it (or a way with fewer steps), but this method will work for me every time.
Environment data
Module versions
Debug output
NOTE Any potentially private information has been blanked out with 'xxx'. If any thing that was blanked out is needed, please contact me privately.
Error output