@bassoy need your suggestion here.
In PR, clang-tidy can upload a clang-tidy-report.txt file as a comment. So people can view it and check what clang-tidy has reported. In push what should be the behaviour to report those clang-tidy warnings? Should CI fail if clang-tidy reports some warning or error? Should clang-tidy check be extended to test/tensor as well or example/tensor and include/boost/numeric/ublas/tensor is enough?
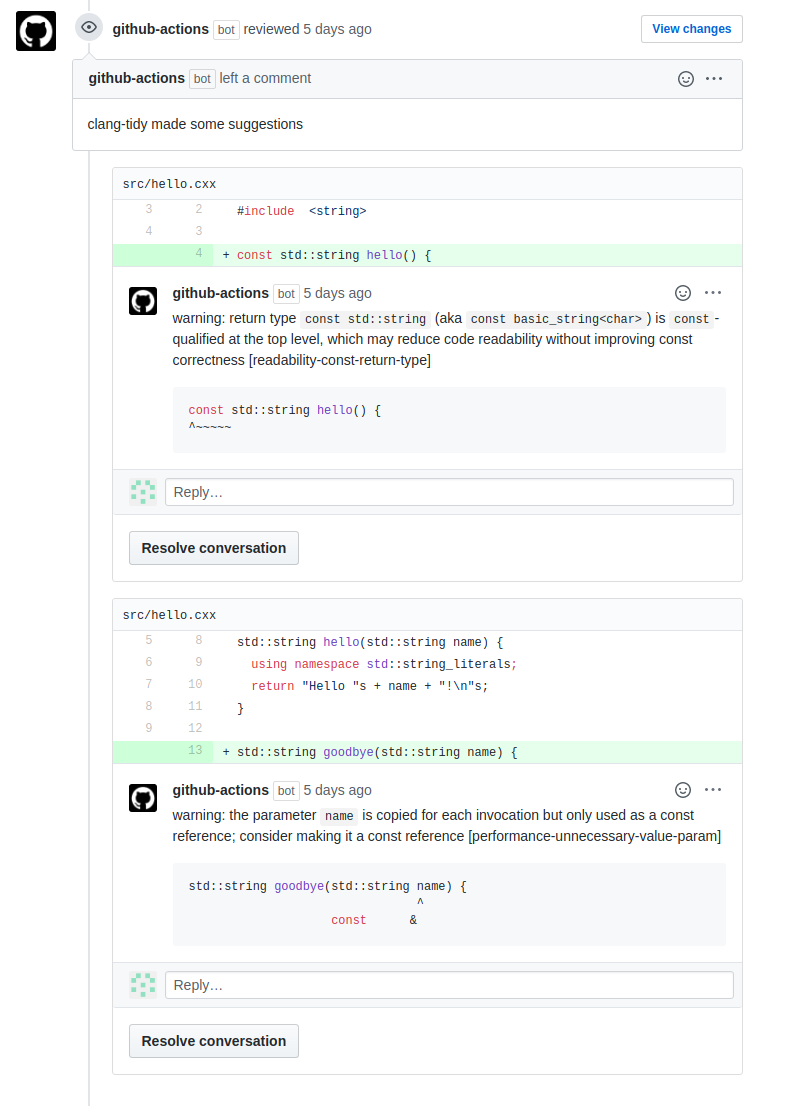
Clang Tidy is a great static analysis tool for checking the quality of the code and to check if a code follows some standards like BOOST Standards.
This issue talks about adding to Github Actions CI clang-tidy checker. After this, the CI will report the clang-tidy results in a PR and in push events.
This will vastly ease up the review process in PR as the reviewer only have to care the logical correctness of the code instead of the standard conference with standards.