@DandelionSprout is there other info I need to add? Also, if I want to report other domains, should I add them to this issue or open a new one?
Closed iam-py-test closed 3 years ago
@DandelionSprout is there other info I need to add? Also, if I want to report other domains, should I add them to this issue or open a new one?
The first two are fine, the 3rd is a p0rn site, not malware, as uBlock-user explained to you.
The first two are fine, the 3rd is a p0rn site, not malware, as uBlock-user explained to you.
@llacb47, What do you mean the first two are fine?

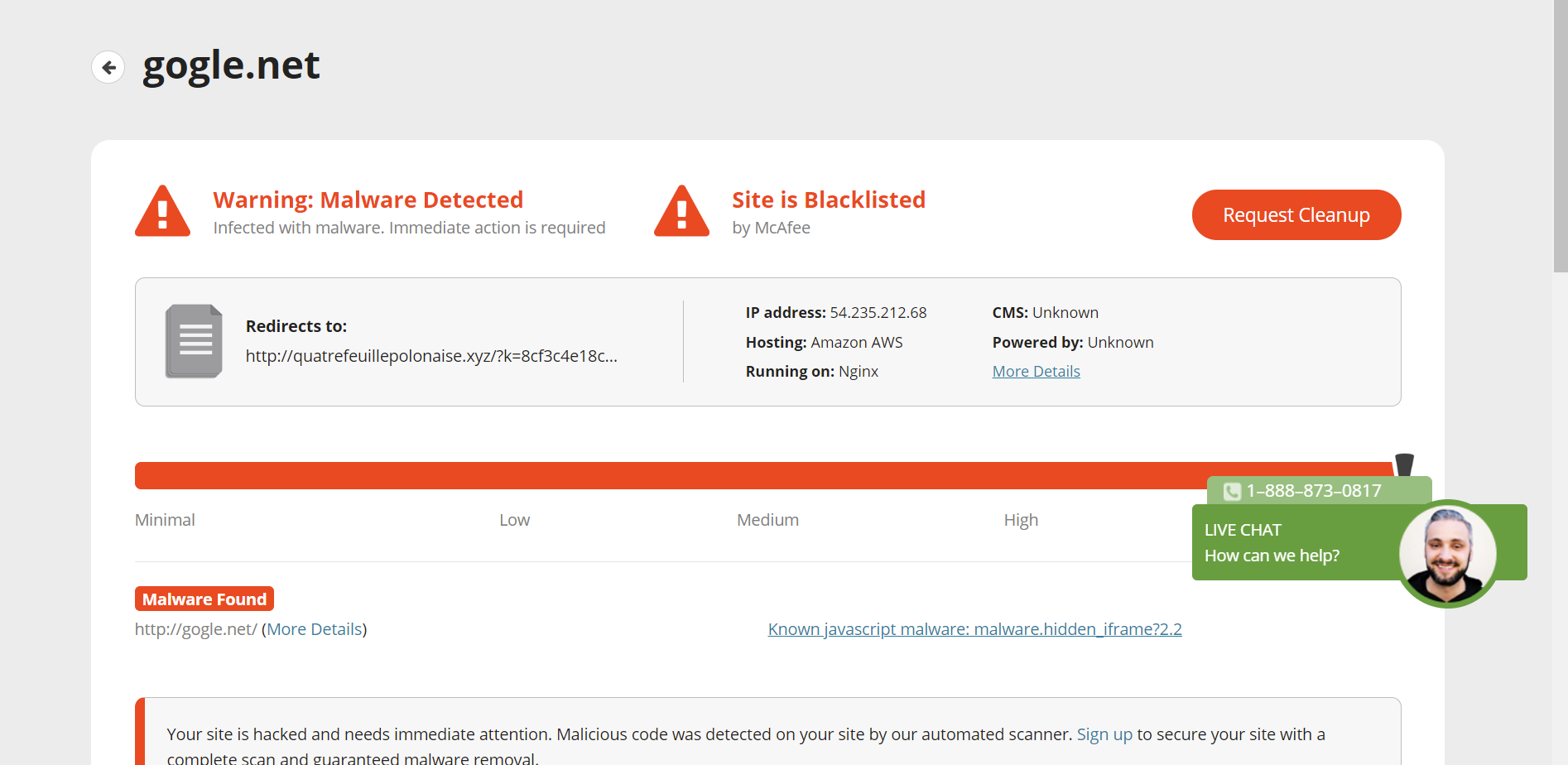
https://safeweb.norton.com/report/show?url=gogle.net https://sitecheck.sucuri.net/results/gogle.net I will remove the porn one. Sorry for wasting your time with bad entries
Strangely, it now shows quatrefeuillepolonaise.xyz is offline.
Closing issue.
Sorry for wasting your time
Fine to report as malware I meant, sorry for being confusing
Fine to report as malware I meant, sorry for being confusing
Oh. Sorry I misinterpreted what you meant.
Using https://redirectdetective.com I found that gogle[.]net redirects to hxxp[:]//quatrefeuillepolonaise[.]xyz/?k=51ca53e382eb9fb4091c78523a668bed.1621979609.91.0.1.d3cuZ29nbGUubmV0&r= which redirects to hxxps://extragifis[.]site/?u=9618mwc&o=rcbkvzh&t=rp134
https://safeweb.norton.com/report/show_mobile?name=https://extragifis.site/?u=9618mwc&o=rcbkvzh&t=rp134 https://www.virustotal.com/gui/url/e8957ef3e4f7c40c9c0443749a45701ccfe1748121f1d4c64c682fd0a7193267/detection https://www.urlvoid.com/scan/extragifis.site/ Does not look malicious so maybe it is parked? Does not seem to support HTTPS either.
@DandelionSprout Do you have a Virtual Env you can use to investigate?

Tried again - no redirect to extragifis.site:

Maybe it detected the redirect detective and blocked it?
Do you have a Virtual Env you can use to investigate?
I do have «Windows Sandbox», which is a whole lot easier to set up than a regular VM. Overall, I am currently on the case of looking into extragifis, which is more than a little malicious from what I can see. Please be patient and calm in the meantime.
Do you have a Virtual Env you can use to investigate?
I do have «Windows Sandbox», which is a whole lot easier to set up than a regular VM. Overall, I am currently on the case of looking into
extragifis, which is more than a little malicious from what I can see. Please be patient and calm in the meantime.
Ok! Thank you. I should have known you had Windows Sandbox set up by reading past issues
@DandelionSprout Thank you!
All the stuff earlier in this thread was a very big mouthful for me to get a grasp of, so I hope it's understandable that I simply added some entries and declared this issue closed now. I also took care of #185 in light of new evidence there.
Ok! Thanks
What are the other domains you added?
The last two were ones that the extragifis link redirected me to. The IP addresses were ones used to host extragifis and captcharesolve-universe.
Ok! Thanks for answering my question. Is it ok if I add those domains to my personal antimalware list? https://github.com/iam-py-test/my_filters_001/blob/main/antimalware.txt
It is of course OK to do so.
Thank you!
@DandelionSprout
Maybe should add captcharesolver.com too.
https://www.virustotal.com/gui/ip-address/5.8.34.26/relations
Looks suspicious with a lot of subdomains in simpler pattern to captcharesolving-universe.com
@DandelionSprout Maybe also chatroom33.com which resolves to the same IP
https://www.virustotal.com/gui/domain/chatroom33.com/detection shows two AVs flagged it
https://www.urlvoid.com/scan/chatroom33.com/
https://www.siteadvisor.com/sitereport.html?url=chatroom33.com
https://safeweb.norton.com/report/show?url=chatroom33.com says it is unsafe
I exclusively use https://securitytrails.com for this kind of analysis. It confirms captcharesolver.com, but not chatroom33.com
I exclusively use https://securitytrails.com for this kind of analysis. It confirms
captcharesolver.com, but notchatroom33.com
https://www.virustotal.com/gui/domain/chatroom33.com/detection

@DandelionSprout, Do you think I should report these domains to Google Safe Browsing too so they are blocked for more users
What about 204.11.56.48?
https://www.virustotal.com/gui/ip-address/204.11.56.48/community
https://www.ipvoid.com/ip-blacklist-check/ shows BLACKLISTED 3/115
http://www.justspam.org/check-an-ip?ip=204.11.56.48
Question: Why is this use $all vs $document vs just a hostname?https://github.com/DandelionSprout/adfilt/blob/3b3c6a90981f428f55174c60cdfd97721efc285a/Dandelion%20Sprout's%20Anti-Malware%20List.txt#L517
https://www.virustotal.com/gui/domain/chatroom33.com/detection
My immediate concern is with the domains at https://securitytrails.com/list/ip/5.8.47.3, rather than ones at 5.8.34.26, to be honest.
What are your pronouns? (…)
Generally he/him, but I'm not like all those people on social media who treat misgendering like a matter of life and death.
What about
204.11.56.48?
https://securitytrails.com/list/ip/204.11.56.48 gives too many results for a broad block to be feasible.
Question: Why is this use $all vs $document vs just a hostname?
It depends on the severity of the domain:
$all: For sites that should not be visited under any circumstances.$doc: For sites where users need to be asked "Are you really sure you want to visit this site?"Ok! Thanks
I was able to get the content of gogle.net
Posted to GitHub here:
https://github.com/iam-py-test/Assets-001/blob/main/goglenet%20malware
Posted Python file here:
https://github.com/iam-py-test/Assets-001/blob/main/page_content.py
@DandelionSprout cpmstatsart.com looks malware to me:
https://www.virustotal.com/gui/url/c7d15fdbb73c179e13c3354a7183e2227034d6a95e9ebe2e312d6dd7ece51ec5/detection
https://www.fortiguard.com/webfilter?q=cpmstatsart.com
https://quttera.com/detailed_report/cpmstatsart.com
@DandelionSprout Requested the cpmstatsart.com url and uploaded response
https://github.com/iam-py-test/Assets-001/blob/main/moremalwarefromgoglenet_related
Looks like a spammy ad/ malvertising.
Update: Using redirect detective it seems like one of those old domains that got taken over; it redirects to a ww17. subdomain when requested
Final response url: http://cpmstatsart.com/
No redirects
whois domain name: cpmstatsart.com
whois registrar: Above.com Pty Ltd.
whois creation date: 2017-08-21 08:41:22
Host ip: 103.224.182.251
WHOIS on the other two:
gogle.net:
whois domain name: gogle.net
whois registrar: Gransy, s.r.o.
whois creation date: 2010-06-13 18:14:33
Host ip: 54.235.212.68
quatrefeuillepolonaise.xyz:
Search Ranking: 144400
whois domain name: quatrefeuillepolonaise.xyz
whois registrar: Namecheap
whois creation date: 2020-04-03 11:09:05
Host ip: 34.196.13.28
Can you edit your comment instead of making 10 different comments? And only post important/relevant stuff. This is not a chatroom.
Another malware domain instantfwding.com from the IP 103.224.182.251
https://www.virustotal.com/gui/url/ad0c37cbc87adfb19706855150eefc0dcacff563d50cbf653ae46f48906e1dc7/detection
https://safeweb.norton.com/report/show?url=instantfwding.com
https://www.fortiguard.com/webfilter?q=instantfwding.com
https://www.siteadvisor.com/sitereport.html?url=instantfwding.com
https://www.urlvoid.com/scan/instantfwding.com/
https://sitecheck.sucuri.net/results/instantfwding.com
https://quttera.com/detailed_report/instantfwding.com
Community reports go back to 4 years ago and also mention these domains; catnip.de, notavailable.goneo.de and trafcenter.us
Clickable links are just to their VirusTotal reports
This one was also mentioned but unlike the others has av detection: fwdservice.com ( https://www.virustotal.com/gui/url/7a140b6dc73a303b290555e3b5ad208266f6105949bbf4b936642475be18a83f/detection)
https://safeweb.norton.com/report/show?url=fwdservice.com
https://www.siteadvisor.com/sitereport.html?url=fwdservice.com
Community reports on https://www.mywot.com/scorecard/fwdservice.com are from 9 years ago but say its phishing
@DandelionSprout Thanks!
@DandelionSprout gamesex.funand goldprize.xyz from https://securitytrails.com/list/ip/5.8.47.3 also look malware.
https://www.virustotal.com/gui/domain/goldprize.xyz/detection
https://safeweb.norton.com/report/show?url=goldprize.xyz
gamesex.fun:
https://safeweb.norton.com/report/show?url=gamesex.fun
https://www.virustotal.com/gui/url/7bedfdd70bd23869a3598186270bcca9e64870842fb95df46da9ed5519e0b41c/detection
Domain from https://www.virustotal.com/gui/ip-address/103.224.182.251/relations: kmip.net
https://www.virustotal.com/gui/url/828b7eda3563b29c05c274af7fd9767669a723fe5f2aba782ce7b1464dd0650b/detection
https://www.virustotal.com/gui/domain/ceyy1.kmip.net/detection
https://www.virustotal.com/gui/domain/kmip.net/detection
I am not 100% sure when I'll be able to go through this backlog, because I've also got a somewhat big backlog over at https://github.com/DandelionSprout/adfilt/discussions/163 to take care of sometime later today.
I am not 100% sure when I'll be able to go through this backlog, because I've also got a somewhat big backlog over at #163 to take care of sometime later today.
Sorry for posting so many comments. I have deleted the ones that just redirect to another domain
Found in community reports on https://www.virustotal.com/gui/ip-address/103.224.182.251/community:
www.iuqerfsodp9ifjaposdfjhgosurijfaewrwergwff.com
https://www.virustotal.com/gui/url/d6b49bc9d8b59af67edcac2f87ef4a63bc0d6760d03076decb79e413dbf61ae5/detection
https://www.virustotal.com/gui/domain/www.iuqerfsodp9ifjaposdfjhgosurijfaewrwergwff.com/detection
https://www.joesandbox.com/analysis/368427/0/html
https://www.virustotal.com/gui/domain/www.iuqerfsodp9ifjaposdfjhgosurijfaewrwergwff.com/detection
https://www.virustotal.com/gui/domain/iuqerfsodp9ifjaposdfjhgosurijfaewrwergwff.com/detection
The community reports on this domain go back for years. According to the community reports, this site spreads the WANNACRY ransomware.
https://www.siteadvisor.com/sitereport.html?url=www.iuqerfsodp9ifjaposdfjhgosurijfaewrwergwff.com https://www.fortiguard.com/webfilter?q=www.iuqerfsodp9ifjaposdfjhgosurijfaewrwergwff.com https://www.urlvoid.com/scan/iuqerfsodp9ifjaposdfjhgosurijfaewrwergwff.com/ https://www.mywot.com/en/scorecard/www.iuqerfsodp9ifjaposdfjhgosurijfaewrwergwff.com https://safeweb.norton.com/report/show?url=www.iuqerfsodp9ifjaposdfjhgosurijfaewrwergwff.com https://sitecheck.sucuri.net/results/www.iuqerfsodp9ifjaposdfjhgosurijfaewrwergwff.com
Reported these domains to Google Safe Browsing
@DandelionSprout It looks like someone registered a variant on captcharesolver.com - top-captcharesolver.com - 3 days ago.
Do you have a Virtual Env you can use to investigate?
I do have «Windows Sandbox», which is a whole lot easier to set up than a regular VM. Overall, I am currently on the case of looking into
extragifis, which is more than a little malicious from what I can see. Please be patient and calm in the meantime.
I would really like to know what you might have found about extragifis.site. As for todays searches the only indication I have found is a html page with site under construction
Do you have a Virtual Env you can use to investigate?
I do have «Windows Sandbox», which is a whole lot easier to set up than a regular VM. Overall, I am currently on the case of looking into
extragifis, which is more than a little malicious from what I can see. Please be patient and calm in the meantime.I would really like to know what you might have found about
extragifis.site. As for todays searches the only indication I have found is a html page withsite under construction
You will have to ask @DandelionSprout as I think he added that filter (I just copypasted it) Also, there could be other pages on that site that are malware
I am very certain it was a redirection domain on the day I tested it.
And as long as it's parked or "under construction", there's a high chance that it still is a redirection domain under some circumstances.
That's true @DandelionSprout
However, I'll think I'll leave the domain at this, as there are no current traces of it being used

@DandelionSprout some new domains which I found when visiting gogle[.]net in a VM:
retailproductsusa.com
cloud-repos.store
! already blocked by .top
nextarrangewent.top
smartcaptchasolve.top
Which entry/entries are you submitting?
gogle.netquatrefeuillepolonaise.xyzWhich things do they block, hide, or unbreak?
These entries block malware domains.
Verification: https://www.siteadvisor.com/sitereport.html?url=gogle.net https://www.mywot.com/scorecard/gogle.net https://www.urlvoid.com/scan/gogle.net/ https://www.fortiguard.com/webfilter?q=gogle.net https://www.virustotal.com/gui/domain/gogle.net/detection https://github.com/iam-py-test/my_filters_001/blob/66213bbc1c0cac88356917f30eb07ac569cf8588/antimalware.txt#L33 Found in curl response of
gogle.nethttps://www.siteadvisor.com/sitereport.html?url=quatrefeuillepolonaise.xyz https://www.virustotal.com/gui/url/7319b37aff351dc0f0e71dba194b5f21972be9ad072b955a35d27d5af359d5fa/community https://www.virustotal.com/gui/domain/quatrefeuillepolonaise.xyz/detection https://safeweb.norton.com/report/show?url=quatrefeuillepolonaise.xyz https://www.fortiguard.com/webfilter?q=quatrefeuillepolonaise.xyz https://quttera.com/detailed_report/quatrefeuillepolonaise.xyz https://www.urlvoid.com/scan/quatrefeuillepolonaise.xyz/ https://www.mywot.com/en/scorecard/quatrefeuillepolonaise.xyzWhich of my lists are you submitting it to?
Antimalware
Which adblocker(s) and version did you use when writing and testing the entries?
Other(s):
Adblocker version(s): uBlock Origin development build v1.35.3b5
Which filterlists did you use? Failing to tell this will temporarily close the report until it has been told.
(Optional) Which browser(s) and version did you use?
Edge Version 90.0.818.66 (Official build) (64-bit)