If I'm looking at the code correctly, there is no protection against setting protected HTTP characters in the request and should be added to this line of code https://github.com/Glimesh/broadcast-box/blob/main/main.go#L81 this should include both characters needing https://datatracker.ietf.org/doc/html/rfc3986#section-2.1 and the following characters https://datatracker.ietf.org/doc/html/rfc3986#section-2.2 on a blacklist
When putting a token into the web browser, all spaces are converted over to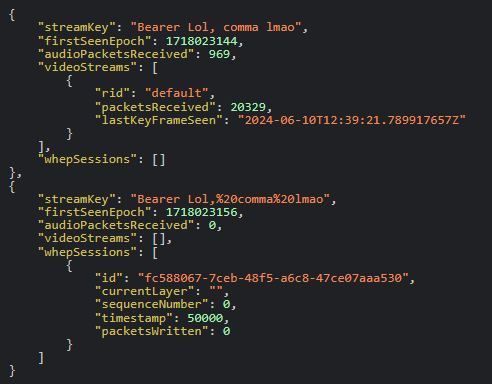
%20while what is received from OBS doesn't contain this sanitization. This causes a flow break when trying to load the stream, as you aren't allowed to send non-sanitized spaces in a web browser.