The GFW has acquired the means to precisely detect the shadowsocks server for a while.You should try some new protocols like VMESS and shadowsocks with AEAD. But once you cost too much bandwidth on single IP, your IP will be banned for sure. So the best way is try use CDN to transfer data to your server(shadowsocks in websocket, V2ray support this feature), I don't think they will ban all these IP using by some major CDN provider.
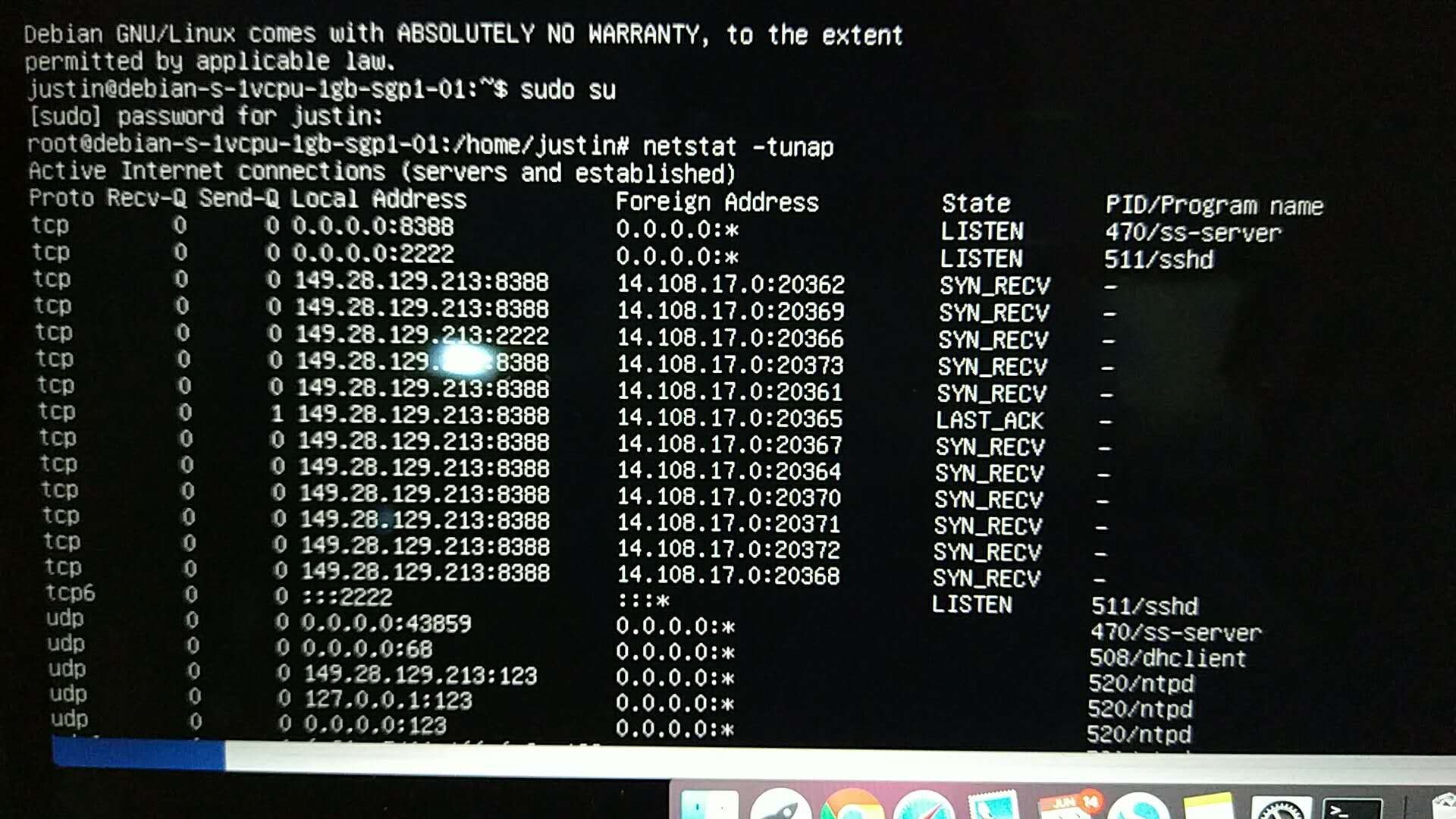
Recently, Iran and China's firewalls detect Outline VPN protocol then IP address of the server will be blocked after a while ( it depends on volume of traffic between Clients and server ).
Unfortunately, after blocking I cannot connect to the server even with SSH protocol and I have to delete the VPS and create a new VPS with new IP address ! I created and deleted 4 VPSs in a week !
Is it possible to obfuscate Outline VPN protocol ?