Hi
Thanks for your submission. We have tested the issue you mentioned and did reproduce it. This is a valid vulnerability. After evaluation, this vulnerability has been graded as P2. Please pay attention to the announcement to get your rewards. Thanks for your attention and contribution. Please keep trying and help us improve our chain.
Regards KuChain Team
Describe The Bug There exists no negative check for
Amountfield inKuMsgwhen handlingTransfer(). The attacker can send a transaction which contains a negativeAmount. This transaction will be executed successfully, after which theToaccount coin will be transferred toFrom. By exploiting this vulnerability, the attacker could transfer all others' coins to the account of himself, which disasterly destroy the whole ecosystem.Code Snippets (Optional) /x/chain/type/types.pb.go:L103-111
The
Amountfiled of theKuMsgstruct can be set as a negative value.To reproduce the vulnerability, we need to modify the source code a little bit. Add some coins to
testacc2inscripts/boot-testnet.sh.Modify the client code to make the amount set as negative when constructing the transfer transction. /x/asset/client/cli/tx.go:L41-76
Input/Output
To Reproduce Steps to reproduce the behavior:
Code Snippets.Expected Behavior Return an error "The amount of coin cannot be negative."
Screenshots Before the transaction: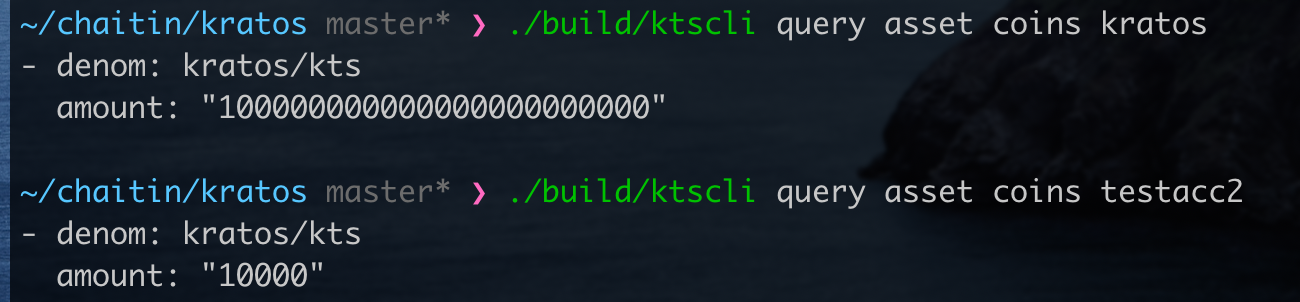
After the transaction: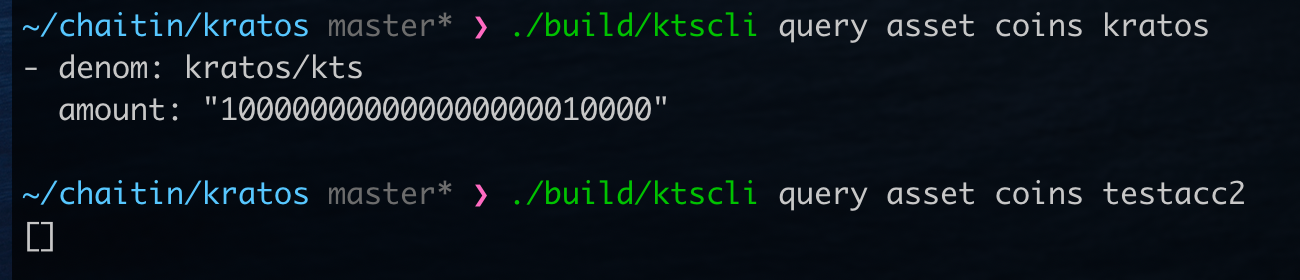
Desktop (please complete the following information):
Additional Context (Optional) Note: This problem not only exists in
Transfer(), many other places also have this problem.Contact Information
xiang.yin@chaitin.comblockchain@chaitin.com