The difficulty could be configured such that a user must solve a proof-of-work problem that would take an average mobile phone on-average ~60 seconds to submit an account creation form.
As mentioned elsewhere, this is not all that different from the rate at which some bot accounts are being created as-is.
On my instance I was seeing 2-3 signups per minute from bot accounts, but they were doing this over the span of multiple hours which let them create a lot of accounts. On an instance like mine where there was ~5 legit users this was immediately noticeable when the amount of registered users jumped to >669 accounts from one day to the next.
And further, as mentioned, due to the distributed nature of Lemmy, spammers can leverage concurrency across instances to create even more accounts. Even if every individual server receives a relatively low number of sign-ups, the fact that the spammers can sign up on muliple servers at the same time means that they are effectively creating a lot more accounts that that even so.
However, the idea of PoW as anti-spam measure is interesting for sure.
I was thinking about how else we might leverage PoW, and I have a suggestion:
-
Harsh rules that will make new users unable to post cross-instance until they have been accepted by admin of local instance. (As someone else suggested in another issue.) In this world an admin should typically review multiple local posts and comments before they allow the user to post cross-instance.
-
Manually hand out bans to suspicious accounts for even the tiniest sign of spamminess when their accounts are new.
-
Create an appeal process for bans that uses PoW, but where the PoW difficulty is hours not minutes. A legitimate user can afford to spend say 6 hours of CPU time to submit the PoW to appeal the ban of his account if he really cares about having an account on the instance. For spammers this will significantly reduce the number of usable accounts that they can have.
PS: Use a PoW algo that is resistant to GPU and ASIC mining. The algorithm used by Monero comes to mind.
Requirements
Is your proposal related to a problem?
The spam-prevention methods available on Lemmy are lacking, and I'm afraid that instance admins may resort to anti-privacy solutions (eg cloudflare anti-bot fronting), which would be horrible for the privacy of users.
It's important that Lemmy provides admins with built-in anti-spam protections that don't prevent at-risk users who need to use privacy tools (eg firefox privacy addons or Tor Browser) from being able to participate in discussions.
Describe the solution you'd like.
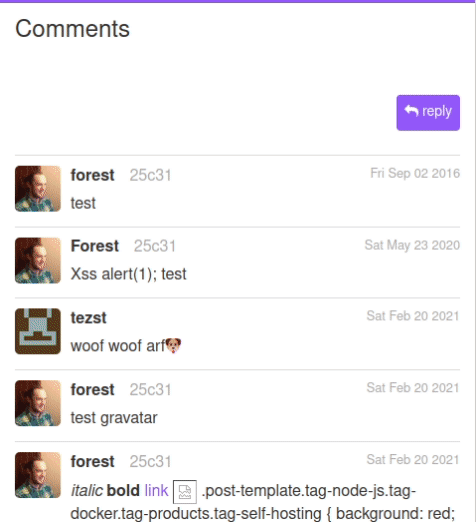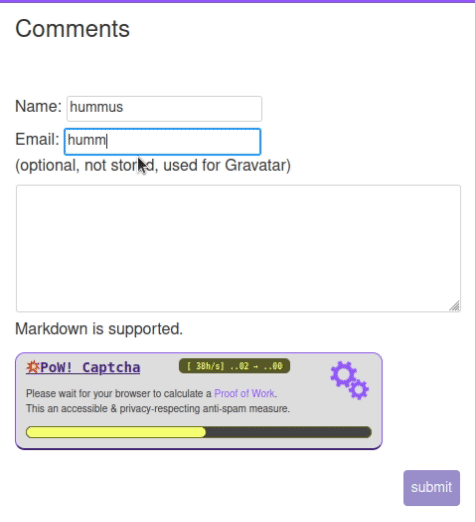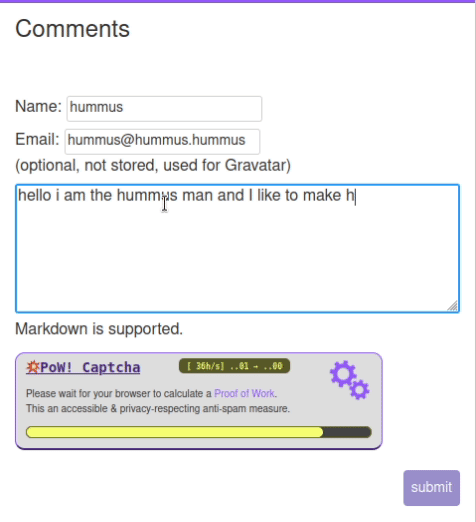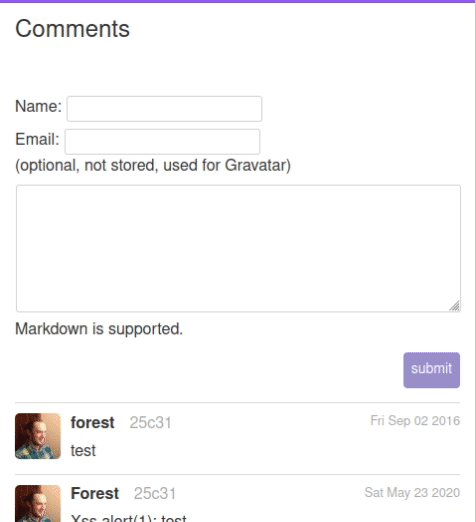
This issue is a feature request to allow instance admins to enable hashcash to rate-limit new accounts (as a means to minimize spam).
Hashash is a proven cryptographic system to rate-limit using a proof-of-work algorithm. The whitepaper was published in 2002, and there are already some typescript implementations available on GitHub
Describe alternatives you've considered.
Many sites will just auto-ban user accounts if their fingerprint cannot be uniquely identified (eg prolific Akamai "Access Denied" error messages across the Internet). This is bad for marginalized folks who need anonymity.
Graphical CAPTCHAs are an option, but they often harm user privacy (eg Google ReCAPTCHA) and sophisticated actors are still able to bypass them.
There is no way to bypass hashcash other than solve the proof-of-work problem, which is a cryptographcially well-proven system of probability, with adjustable difficulty.
Additional context
The suggested implementation would allow lemmy instance admins to turn on hashcash for users signing-up for a new account. The difficulty could be configured such that a user must solve a proof-of-work problem that would take an average mobile phone on-average ~60 seconds to submit an account creation form.
This feature could also be added for any other writes to Lemmy, including submitting links and comments. The instance admin could require new accounts to solve a proof-of-work with every write-operation if they have less than some amount of positive karma and/or until their account is > X days old.