I've rewritten the first sections before going into the trust network architecture.
- Decentralized Trust Network
- Digital Identities & Identity Providers
- Reputation Systems and Trust Networks
- Trust Network Architecture
- ...
So now I've moved most of your content underneath the "Trust Network Architecture".
Those sections afterwards still require a review as the explanations get more technical.
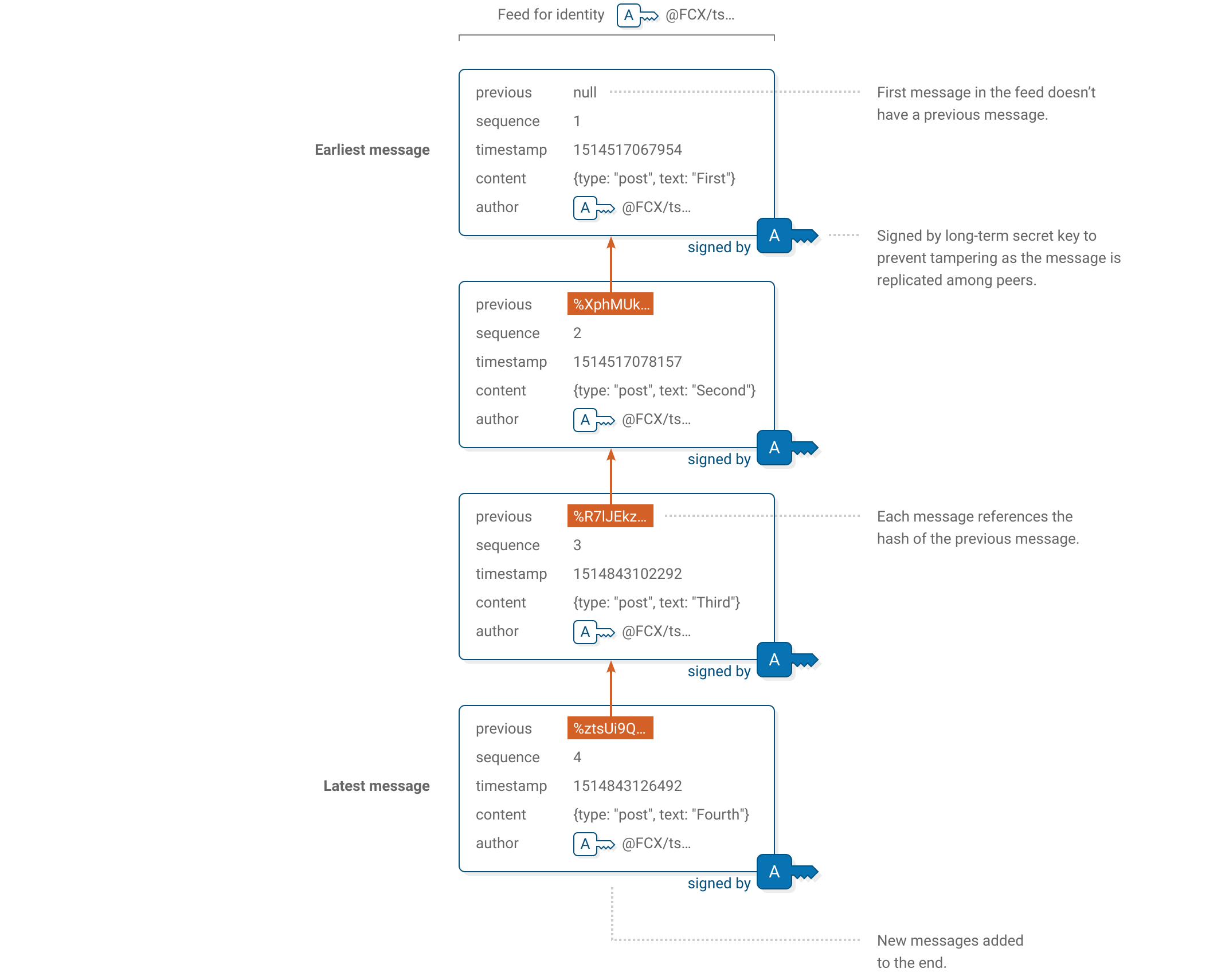
Specification
Our polykey-design repo has lots of information on how DIs and Gestalts and Social Discovery works.
All of this information should be synthesized into the Polykey wiki, the js-polykey wiki should be focused on the CLI-side of the situation.
Additional context
The wiki page can be found here: https://github.com/MatrixAI/Polykey/wiki/Decentralized-Trust-Network
Tasks