I’m aware of the situation and I’m trying to get to the bottom of what’s going on here. I’m going to submit the application to Microsoft’s Security Intelligence team with context to what the application is doing and see what further steps I can take from there.



 Even firefox thinks it's a PUP now.
Even firefox thinks it's a PUP now. .
.
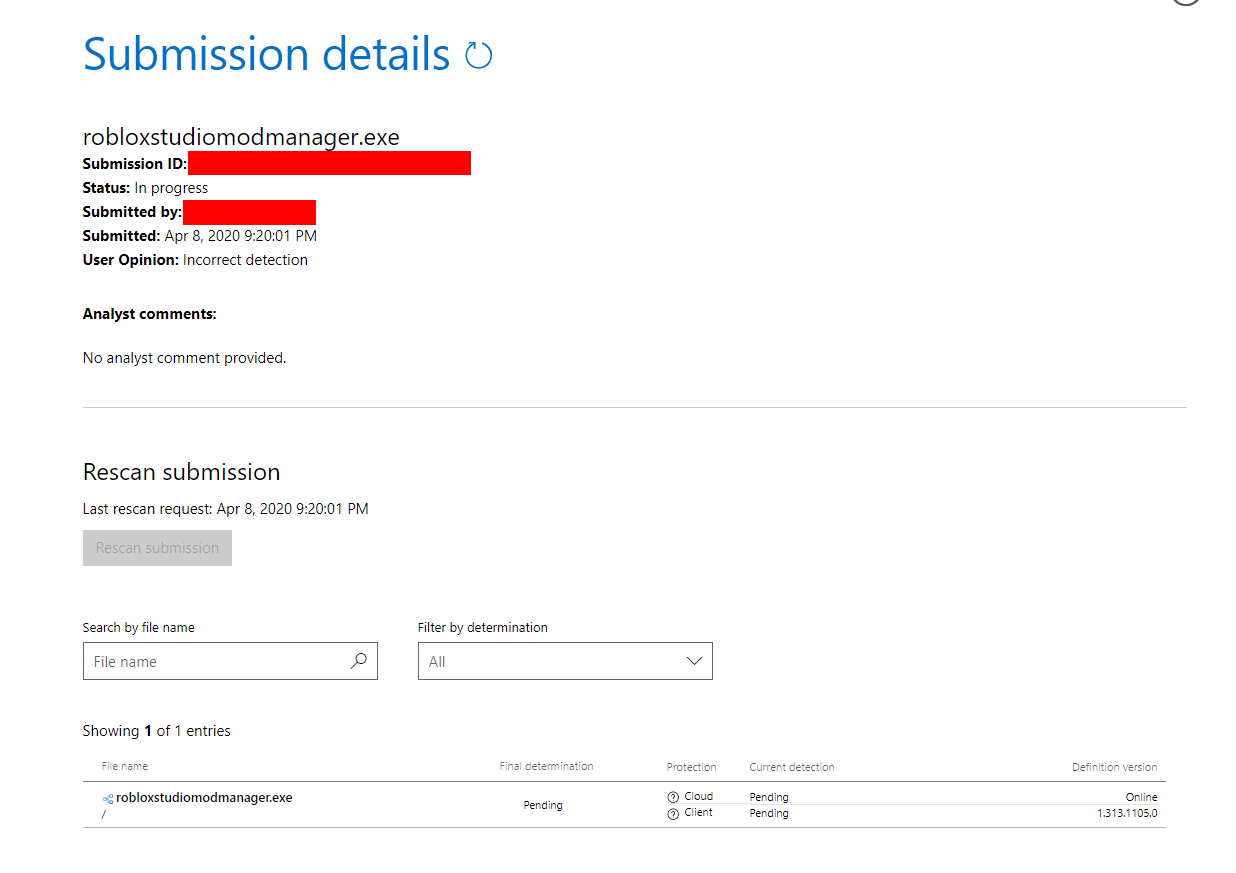
Windows defender now falsely detects RobloxStudioModManager as a trojan virus, as shown below. Additionally, as you can see in the following VT scan, a lot of anti virus softwares are flagging this.
https://www.virustotal.com/gui/file/e0b3bce3d68eaf6d049c724d95c03788ba11e062868c3a4761f08fd6caa9fd01/details
Additionally, as you can see in the following VT scan, a lot of anti virus softwares are flagging this.
https://www.virustotal.com/gui/file/e0b3bce3d68eaf6d049c724d95c03788ba11e062868c3a4761f08fd6caa9fd01/details
I am not sure what would or could have triggered a false flag. This serves as both a heads up to users visiting, as well as a notification to the developer of this tool. Thankfully, since RobloxStudioModManager is a .NET executable, manual analysis is fairly easy to do. From what I've looked at, I don't see anything malicious doing a fairly thorough search of the compiled file.
For some reason, despite showing up in decompiled code, there is a marked inclusion of the string "C:\Windows\system32\cmd.exe" within the program may have potentially flagged antivirus software. VirusTotal marks this as a "highlighted" item, and interestingly it does not seem this is present in the code. A potential fix could simply be to use "cmd" if it is present and I simply missed it since System32 is part of the path by default on all Windows machines (and removing it from path will cause mass issues for any program using the command line).
Additionally, it seems that false flagging of RobloxStudioModManager has been an issue previously unfortunately. Hopefully this isn't a large problem.