@JoeyC-Dev : Thanks for your contribution! The author(s) have been notified to review your proposed change.
Open JoeyC-Dev opened 2 weeks ago
@JoeyC-Dev : Thanks for your contribution! The author(s) have been notified to review your proposed change.
Learn Build status updates of commit e140920:
| File | Status | Preview URL | Details |
|---|---|---|---|
| articles/aks/limit-egress-traffic.md | :white_check_mark:Succeeded |
For more details, please refer to the build report.
For any questions, please:
Learn Build status updates of commit c08ec44:
| File | Status | Preview URL | Details |
|---|---|---|---|
| articles/aks/limit-egress-traffic.md | :white_check_mark:Succeeded |
For more details, please refer to the build report.
For any questions, please:
@asudbring
Can you review the proposed changes?
When the changes are ready for publication, add a #sign-off comment to signal that the PR is ready for the review team to merge.
@MicrosoftDocs/public-repo-pr-review-team
Proposed change:
\in the original command, which will split the command into two parts.Context: Using user-assigned managed identity for AKS.
Basis: Part 2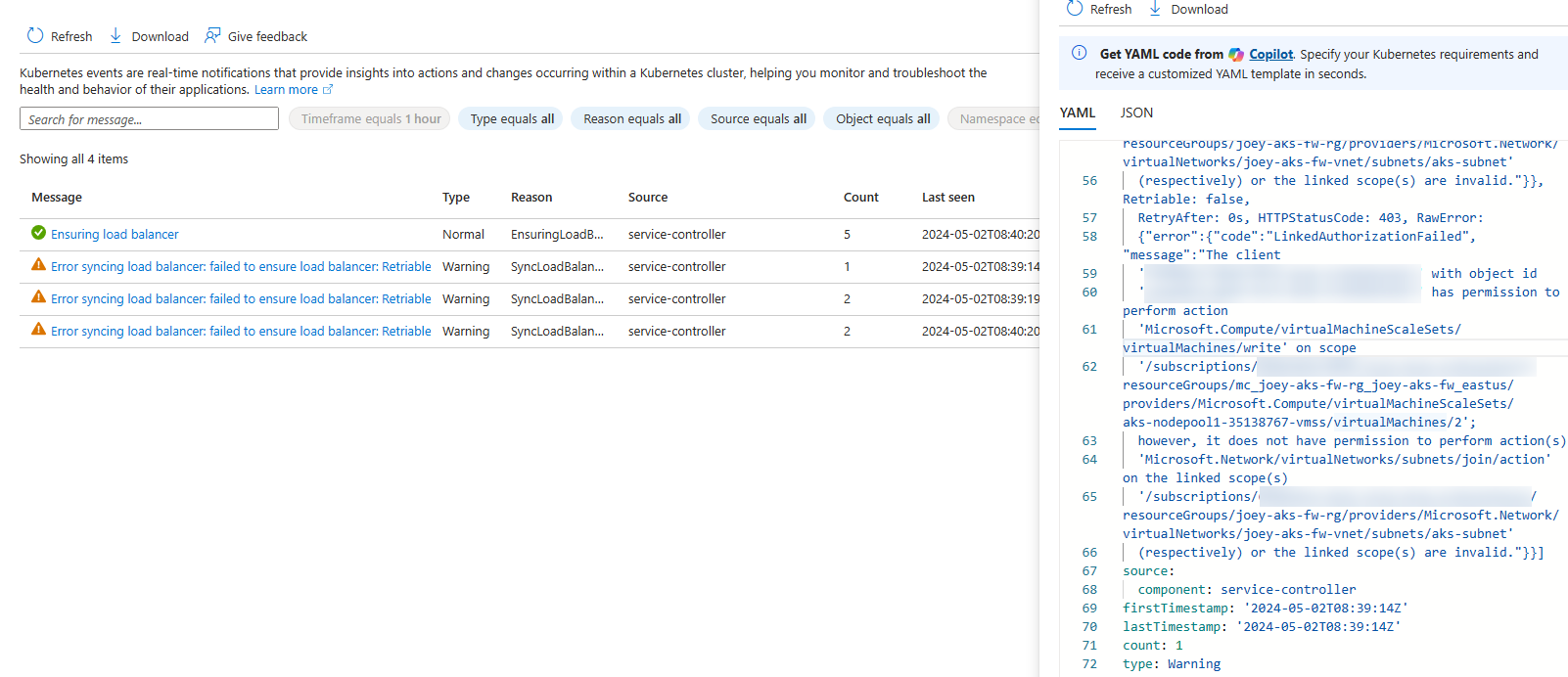 Part 3
Environment: Cloud Shell
Part 3
Environment: Cloud Shell
Issue occurred if following current document:
Result after changes: Environment: Cloud Shell Change 1
Change 2&3
Role assignment can be successfully found: Route table: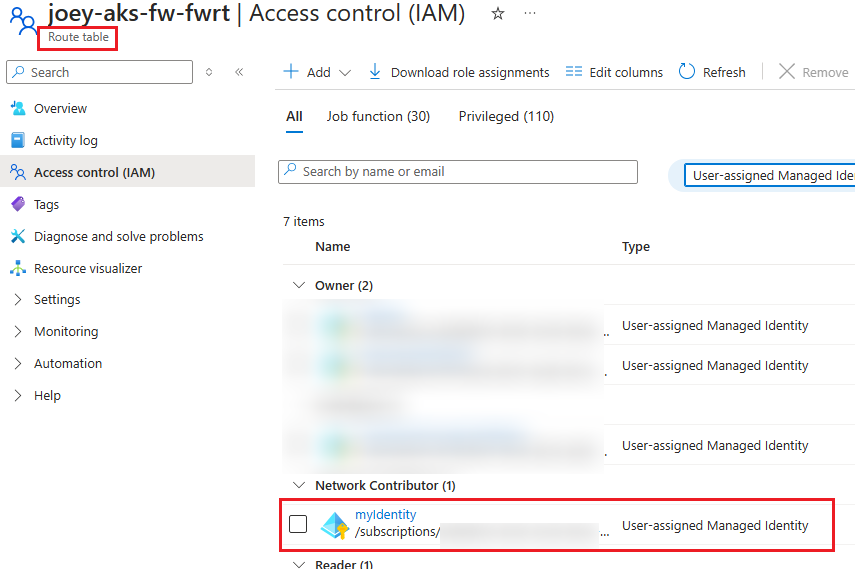 Subnet:
Subnet:
Wait 5 mins then deploy service:
No issue at all:
I also test system-assigned managed identity, it does auto-assign the role. Only user-assigned managed identity will not auto assign the role.