A thought on this feature: I think if we go through the stride threats and add something (2), mentally we've already done 3. It's why we know how to do 2. I do think it's a good idea for early threat modelers and will help teach.
My request (as with the pulldown for STRIDE vs other methods) is to default to whatever choice we make, and that it's not a mandatory step. So if we by default not to select the att&ck tactic, we don't get blocked if it's not selected. That will allow the "power users" to continue to move quickly through the model.
If you've used the later iteration of the MS SDL threat modeler, you know it's hardwired to windows mechanics and the wizard based approach can break threat modeling by forcing you into choices that don't apply. This is why I've moved away from that tool.
Describe what problem your feature request solves: Currently the tool does a good job for decomposing the architecture and applying threats according to the STRIDE framework. This still leaves some gaps to determine the cybersecurity requirements that the process needs to adhere to remediate identified threats.
Describe the solution you'd like: The solution I am proposing is that we can create an additional layer of taxonomy of threats under STRIDE to identify the attackers tactics and techniques which might be used to identify the right defenses. These can become the cybersecurity requirements for the process that we are threat modelling.
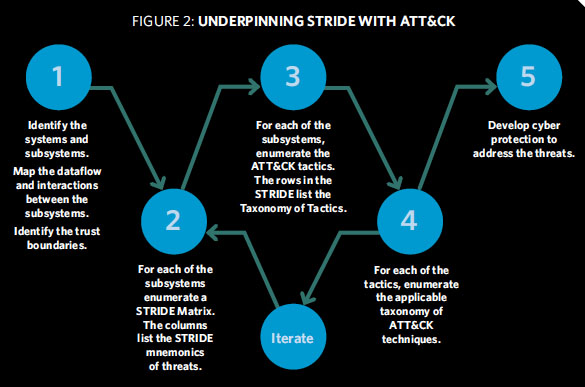
This combined process for threat modeling can be like: The first step is to identify the process, map out the dataflows and interactions between them and the trust boundaries.[Threat dragon is capable of this]
Second, for each of the subsystems, enumerate a STRIDE matrix listing the mnemonics. Third, the 12 ATT&CK tactics are tallied. Enumerated tactics are: • Initial Access • Execution • Persistence • Privilege Escalation • Defense Evasion • Credential Access • Discovery • Lateral Movement • Collection • Command and Control • Exfiltration • Impact
In Step 4, for each of the tactics within each of the STRIDE mnemonics, the applicable techniques are evaluated. For instance, for the STRIDE mnemonic of spoofing, the 12 tactics are evaluated for ATT&CK threat techniques that could result in spoofing against authenticity. In other words, Steps 2 through 4 are a process of elimination.
Advantages:
References: https://blog.isc2.org/isc2_blog/2020/02/under-attack-how-mitres-methodology-to-find-threats-and-embed-counter-measures-might-work-in-your-or.html