Thanks for reporting and the work to put RoboSats App together for EmbassyOS.
HTTPS access from not whitelisted domains are blocked by the backend, unfortunately white-listening all origins is not a good idea.
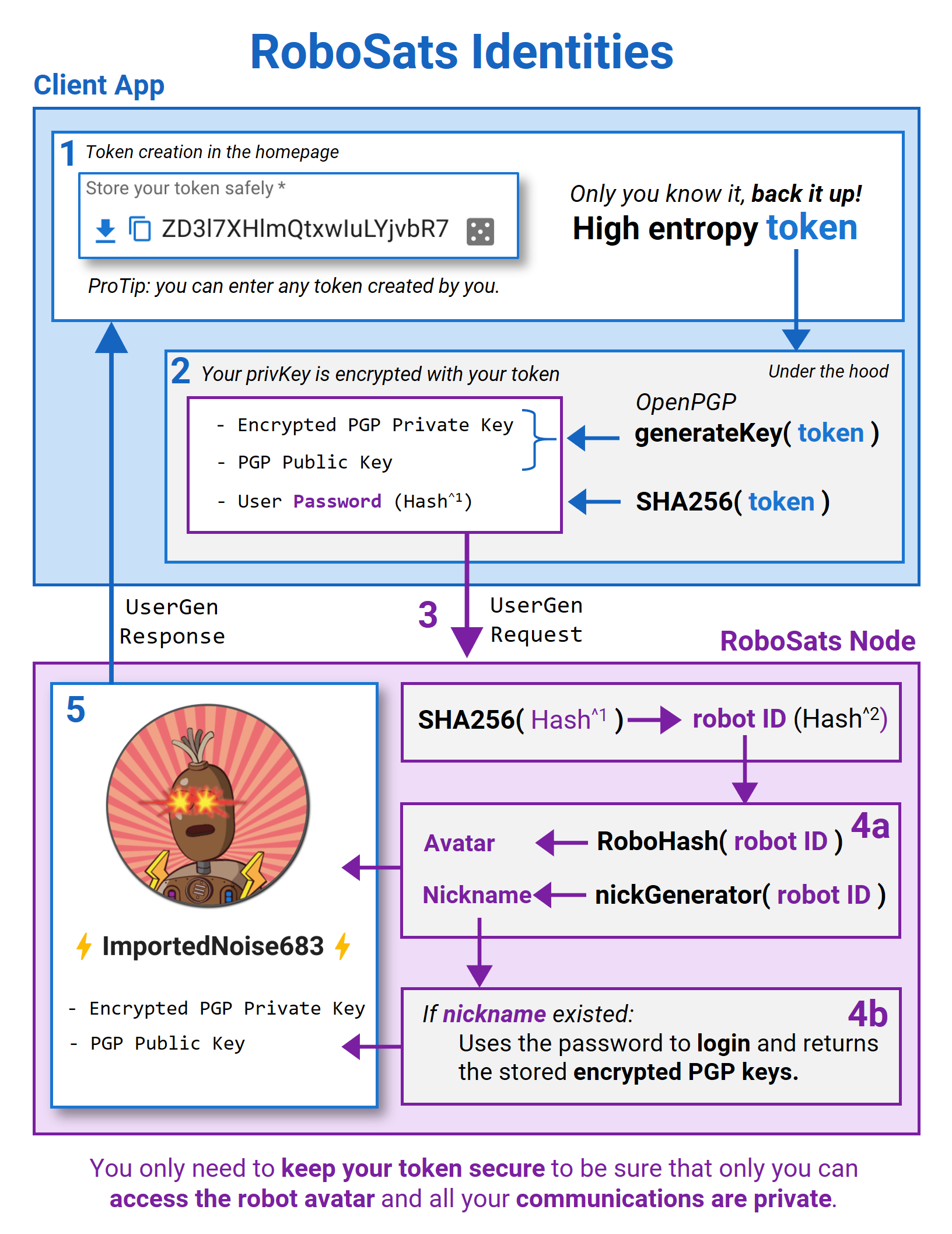
Given that we are storing the Robot Token in cookies, we might want to rethink authentification all together. I am not sure what would it take and whether this is safe, but maybe sending the token hash with very request (as a sort of token authentication) might work. In addition, this would make authentication for API users much easier. Needs more research.
This is unfortunately required for LAN access on Robosats for Embassy