@ScriptTiger I have setup a central repo for controlling whitelisting, false positives, dead domains and use this data to strip out relevant entries from my other repos. Instead of re inventing the wheel why not just contribute to the central repo and use this one source for controlling removal of dead / inactive domains, false positives and whitelisted domains?
https://github.com/mitchellkrogza/CENTRAL-REPO.Dead.Inactive.Whitelisted.Domains.For.Hosts.Projects
My Ultimate Hosts repo at https://github.com/mitchellkrogza/Ultimate.Hosts.Blacklist already used this central repo to do list cleaning during builds and the same with Badd Boyz Hosts too https://github.com/mitchellkrogza/Badd-Boyz-Hosts
Efforts might best be spent sending in PR’s and Issues on the Central Repo as I have found that this is truly going to be the best way going forward
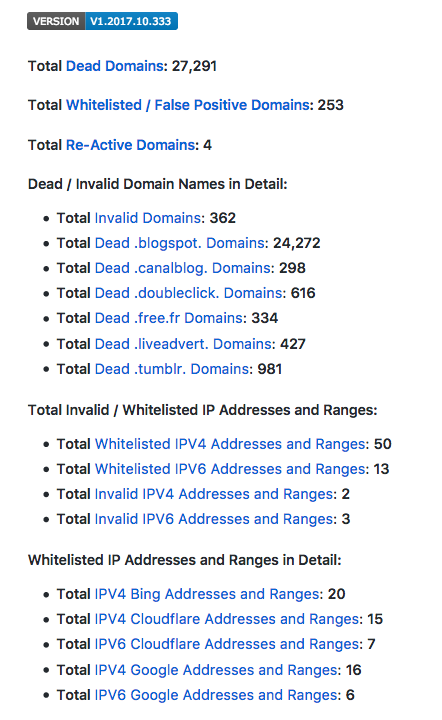
I don't know if @funilrys is just being cautious or shy or what, but I will just raise this topic for him. Would it make sense to integrate funceble into this repo and cleanse the aggregate as part of the hosts generation every time? PR needed/wanted? It seems like the resultant files would just get an added layer of curation, but I think maybe @mitchellkrogza and @funilrys are best suited to answer this. Obviously it would be redundant in the case of the entries taken from @mitchellkrogza, as he already uses it, but it may be useful as an add layer of curation, as I said, on top of the other sources that don't use it.
Of course the time it takes to generate the files would be impacted, so that would be entirely up to @StevenBlack. But I know @funilrys and @mitchellkrogza have been tweaking a bunch, so I'm not sure how much they can vary the generation times, or any other specs that @StevenBlack might be interested in tweaking to be in keeping with the project's core purposes.
Could anyone that has experience with this provide estimates for the efficacy of this if run on this repo? Like generation times, diff percentage of cleansed to original, etc.?