I don't understand the connection of this to the proposal we made in the Excel sheet for the new tab with the (so called) "Template Overlay". What we're trying to do is move away from device specific issues (screen resolutions, presentation layer technologies) and simply have the OCA Creator say "here are some parameters you can use when displaying this data". That leaves the party that is actually displaying the data to use the parameters (logo, background image, etc.) anyway they want. That means the OCA bundle has less layout information -- vs. the suggestion here, which I interpret as much, much more layout information.
That said -- I'm not against an OCA way of doing layout as you describe above, if others think it is useful. However, we would not be using it, and we still would like an OCA way to do the "Layout Parameters" approach that we have proposed.




Introduction
OCA presentation layer is one of the third fundamental features of OCA. The two remaining are data harmonization (including any third party process to achieve harmonization, ie. transformation) and context preserving data capture. This triple enables everyone to preserve capturing context of the data, have the consistent data and finally present it on the screen if needed. Not every data requires presentation on the screen and usually only this that was captured from humans. In other words if one party fulfilled the form, the other party may want to see it on the screen. When data doesn't need presentation in most cases will be captured by machine, ie. an IoT sensor that measures environmental data. Data captured in such manner will require unified form for further processing/data mining/predictive maintenance, therefore harmonized data is they key to achieve it.
Issues with presentation layer
OCA presentation layer enables to visually see the captured data in the most human friendly way. Either this is mimicking real world cases to digital world (ie. any type of credential) or just a nice way of presenting data on the screen, it is always dependent upon device and the underlying technology used for actual presentation. Being device and technology agnostic in terms of presentation is very difficult to achieve. Many devices and technologies exist for information presentation while none actually enables a unified way of doing so. The presentation problem is known since decades and many tried to unify it in the past. However, the fact is the industry never reached even a standard of how to define information presentation on the screen, not mentioning cross device or cross technology portability. Is this a gap that the industry didn't notice? No, this is a difficult problem to solve.
Any presentation is device and technology dependent. Devices come in various resolutions and screen sizes, usually biased to some particular technology that can be used for presentation. Therefore any approach that would address agnostic-ism to device and technology must be merely about layout, so about spatial orientation or how various pieces are located on the screen (or part of it). A good example of how to think about it is this tree: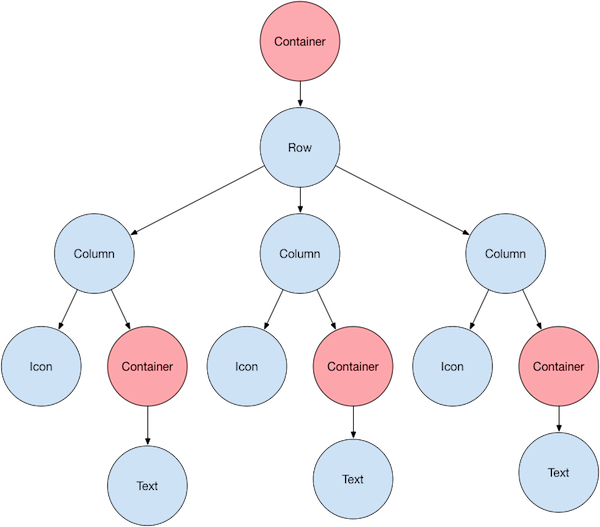 Linked from https://docs.flutter.dev/development/ui/layout
Linked from https://docs.flutter.dev/development/ui/layout
Any layout is inherently a tree based structure that consists of elements, that are displaced upon the parent element. A syntactic sugar, so the rows and columns concept enables better spatial orientation. The current layout overlay is implementing this concept as follows:
Layout overlay shall provide only spatial orientation of the elements on given area and at the same time stay technology agnostic. The current layout overlay requires
cssattribute and therefore is not technology agnostic.Determinism in OCA
Worth to recap the fundamental assumption that all the overlays implement: they are deterministic, actually the whole OCA bundle is. Deterministic OCA bundle is in other words self-encapsulated and nothing can be injected in runtime. In this sense all the overlays are inherently made in stone. Deterministic OCA is crucial characteristic for proper governance.
Presentation layer that is device and technology agnostic
To achieve such kind of agnostic-ism, current layout overlay must remove any technology specific behavior and become template overlay. Where there's a need of technology specific behavior, new type of overlay has to be defined: layout overlay. Assuming ZIP as OCA bundle, the following would be a part of the meta file:
A dependency tree among overlays would look like:
Layout/template overlay metadata consists of:
credential) [required],react-native) [required],<1024) and driver name (ie. flutter -- only layout) [optional -- if not defined, applied for all cases].This is a proposal and can be discussed further. What's important is the clear distinction per device and technology. In all cases YAML is preferred as it is the simplest descriptive language for defining behavior.
Layout overlays merely inherit from template overlays the spatial arrangement and add technology specific flavor that is required to render them properly, using given technology.
These assumptions guarantee flexibility while preserving the determinism. There can be any number of
template.xyz.ymlas well aslayout.xyz.yml, each serving desired purpose or spatial arrangement, including proper logo, background color and so on. This is always finite number of cases(overlays), even across various jurisdictions or countries. Since there are multiple of them, it is up to the client to decide which one to use in given use case (according to device resolution or the underlying technology).The drivers that are responsible for proper rendering can be implemented externally for given technology. Whether this is Flutter, React Native, PDF or WEB, it is up to the driver to present the layout properly. Presentation, so the driver, is optional to the OCA core and therefore all the rendering drivers are optional.
Update as of 28th of Sep 2022
Template and layout overlay distinction
Template overlay
The template overlay defined above provides only a spatial arrangement. Neither components nor styling are defined on this level. This is only an agreement how assets provided via layout overlay must be arranged within given area.
Layout overlay
Layout overlay adds proper look and feel to the template overlay.
Whether layout overlay is part of OCA bundle is governance dependent. In cases where issuer didn't impose any particular rules of how to present his data, but merely provided minimum amount of assets that shall be used, ie. this case, layout overlay is outside OCA Bundle.