I have a sneaking suspicion that this is actually not a Gutenberg fault, but a deeper one with the REST api. Do you have the basic permalinks set? If so, try swapping to a custom permalink and give it another go. I wrote up some details (with links to tracs etc) when I ran into this symtom.


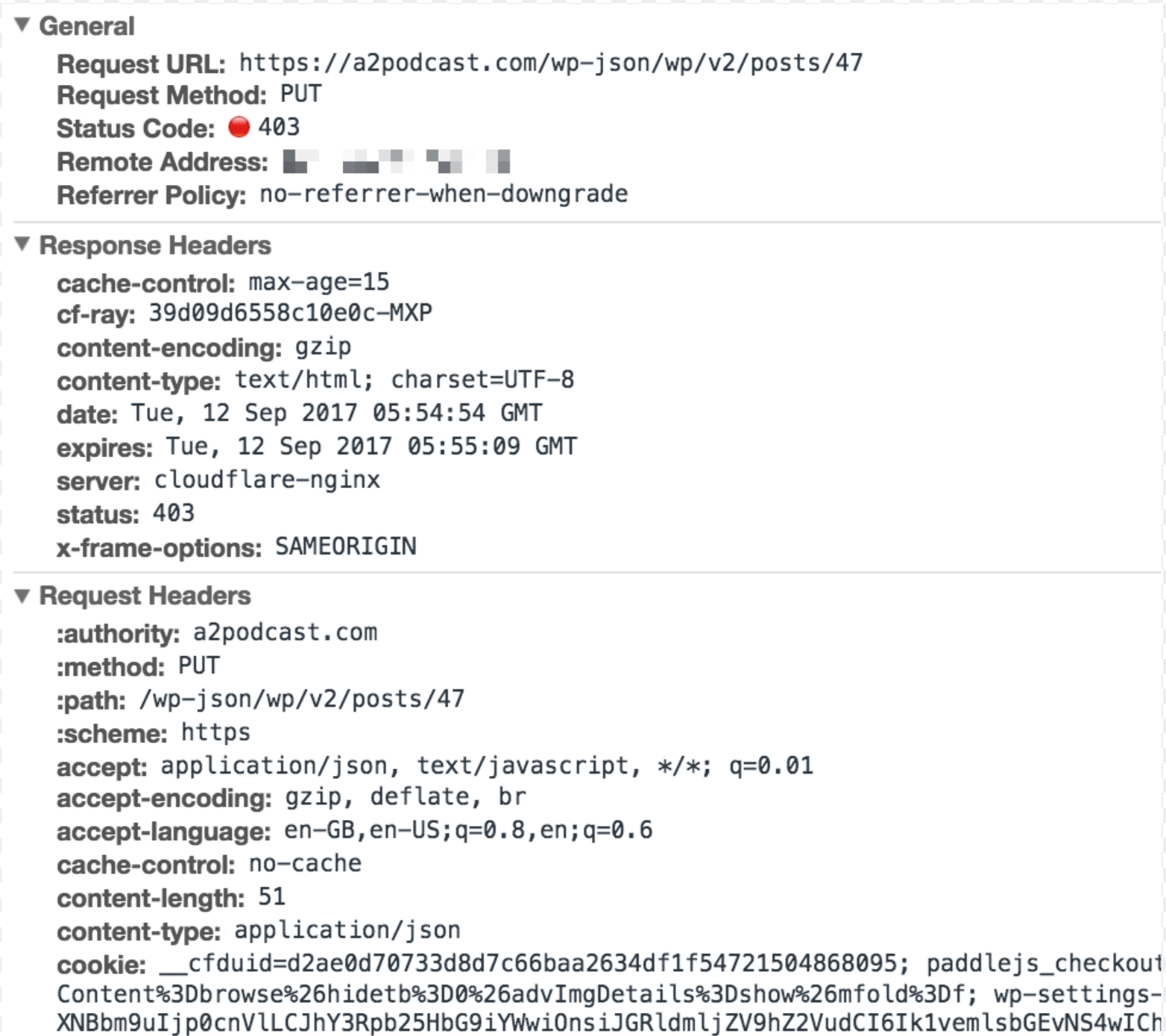


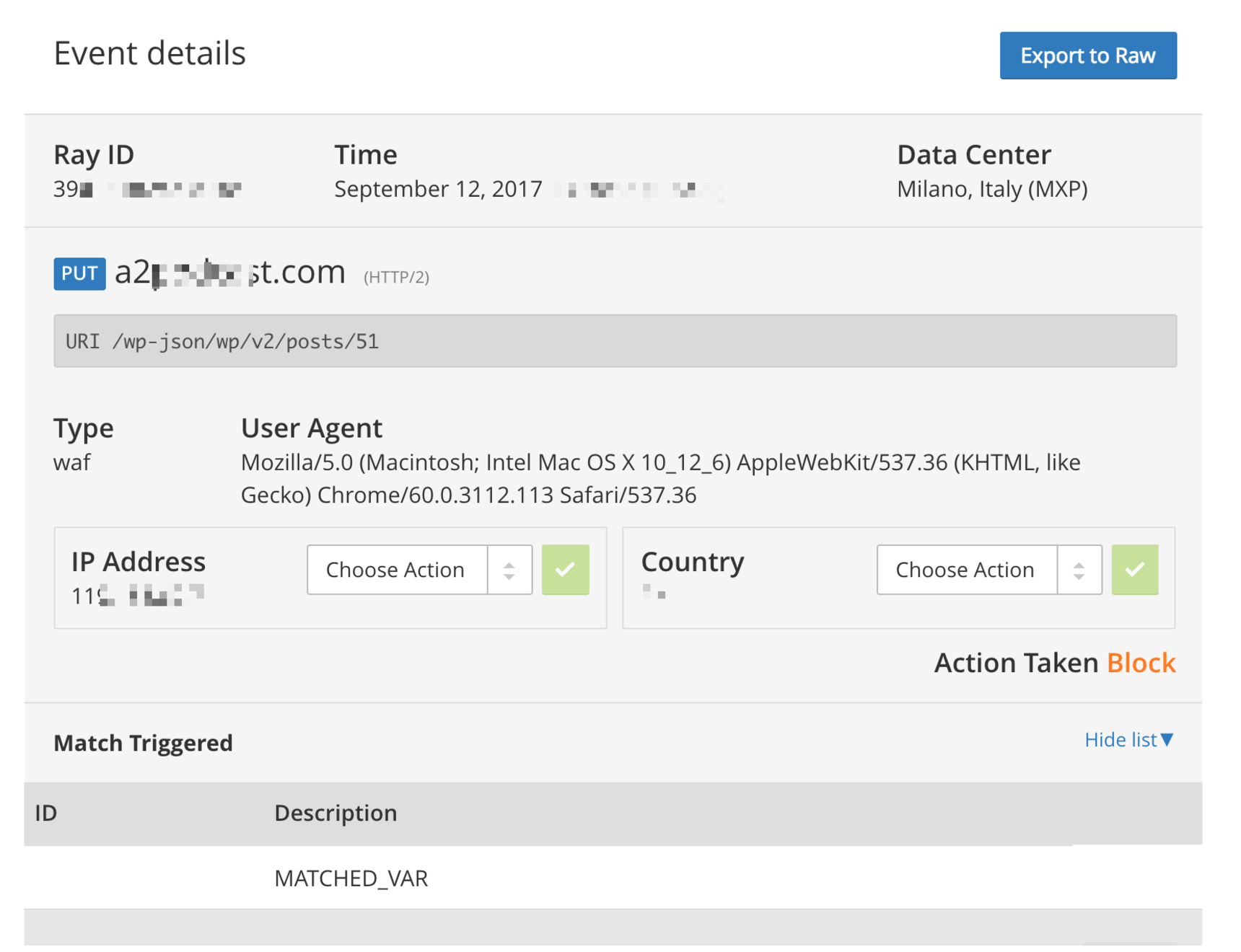






[UPDATE: Cloudflare rolled out a fix for problems with the
WP0025Brule 8-Aug-2018, please update.]I have started to try Gutenberg on a production site and it is not working. The site is new and has no other plugin installed. Looks like the
PUTrequest is not working.I am using the latest version of Gutenberg
1.1.0available in the WP Repo. I have also tried this on two other sites and same error. I thought I should report it here?