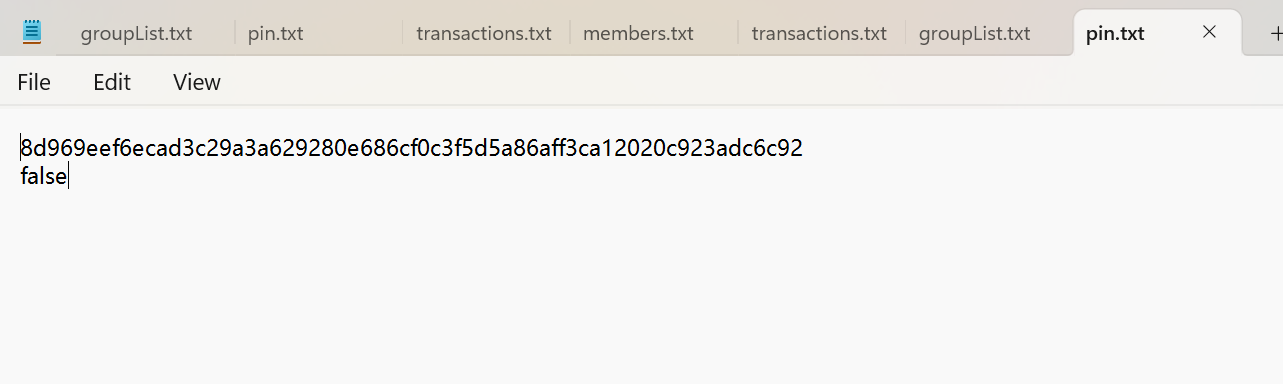
 Password enable can be manually set in the txt file so that any user can enter the app without knowing the password.
Moreover, the encrypted password can be manually edited (either by malicious intention of a non-user, or by the user by accident), such that the user will not be able to know the correct password.
Password enable can be manually set in the txt file so that any user can enter the app without knowing the password.
Moreover, the encrypted password can be manually edited (either by malicious intention of a non-user, or by the user by accident), such that the user will not be able to know the correct password.