Hey folks, I think this change needs to be done on the user side.
According to Microsoft's blog post, section "Phase I: User Opt-in", people will have to generate new private/public key pairs and update both, Azure configuration and Argo CD repository config with this new key.
Have you tried generating a new key pair, with a supported algorithm?
I have generated new keypair for argocd:
sergei@Macbook ~ ssh-keygen -l -f /tmp/1
3072 SHA256:ZjVTR8zK9UEmQaQmc8tuPqjszaee1yHIq8KAzJDQUJ8 sergei@Macbook.local (RSA)have updated the argocd repo-creds secret, restarted repo-server and argocd-server pods but still getting this error from time to time:
time="2024-04-26T13:09:14Z" level=warning msg="finished unary call with code FailedPrecondition" error="rpc error: code = FailedPrecondition desc = error resolving repo revision: rpc error: code = Unknown desc = unknown error: remote: Command git-upload-pack: You’re using ssh-rsa that is about to be deprecated and your request has been blocked intentionally. Any SSH session using SSH-RSA is subject to brown out (failure during random time periods). Please use rsa-sha2-256 or rsa-sha2-512 instead. For more details see https://aka.ms/ado-ssh-rsa-deprecation." grpc.code=FailedPrecondition grpc.method=Sync grpc.service=application.ApplicationService grpc.start_time="2024-04-26T13:09:14Z" grpc.time_ms=234.662 span.kind=server system=grpc

Hi all, Microsoft published a blogpost Feb 15th 2024 to sunset the ssh-rsa support and wants to migrate to rsa-sha2-256/512. Blog Post: https://devblogs.microsoft.com/devops/ssh-rsa-deprecation/
Based on their schedule everyone that still uses their service should be in Phase 2 where an throttling/delay is in place and an error is shown with following message.
“ssh-rsa is about to be deprecated and your request has been throttled. Please use rsa-sha2-256 or rsa-sha2-512 instead. Your session will continue automatically. For more details see https://devblogs.microsoft.com/devops/ssh-rsa-deprecation.”
This error is also shown within argo.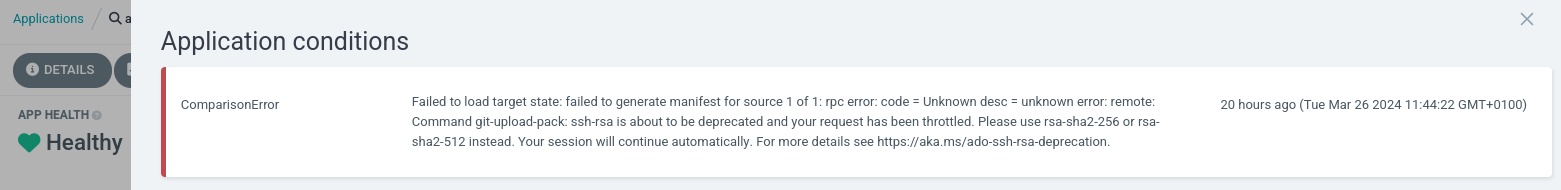
After searching a bit - it seems like that golang/crypto already support rsa-sha2-256/512 but sadly starting from v0.21.0. (https://github.com/golang/crypto/commit/6fad3dfc)
Argo seems to use v0.19.0 https://github.com/argoproj/argo-cd/blob/1bddee2e5dfff35613847eef9a2c0e6818976dc3/go.mod#L85
Also found a relevant issue in this regard: https://github.com/argoproj/argo-cd/issues/7600
Checklist:
argocd version.Describe the bug Argo is currently unable to pull git repositories provided by azure devops repos and stops after receives the delay error.
To Reproduce Pull a repository from their service with a ssh key.
Expected behavior Argo pulls changes or state from git repository.
Version
Logs
Logs from repo-server: