@BearHanded, can you help us understand what you're looking for here and more context on why you'd want both api-key and Authorization header? This does appear to be a version-parity issue between v5 and v6, and we are digging into it on our side as well.
Before opening, please confirm:
JavaScript Framework
React
Amplify APIs
Authentication, REST API
Amplify Version
v6
Amplify Categories
auth, api
Backend
None
Environment information
Describe the bug
I'm currently migrating amplify versions to v6. I have a use case where my API gateway looks for the Authentication header provided by default and lambdas (REST API) assess other headers on the request. Providing a modified header with x-api-key like so now removes the default signed Authorization headers from the request:
Looking through the amplify package to see where this is signed, I see in
@aws-amplify/api-rest/dist/esm/apis/common/handler.mjs:This appears to be a change from past versions. We were previously able to have an api key and the Authorization header passed through via amplify.
Some of this may be an anti-pattern of the system I am attempting to upgrade, however I don't see anything saying these two headers should be mutually exclusive. I'm attempting to upgrade the package without rearchitecting the application's auth.
Am I missing some configuration option or do I need to roll my own header signing pattern here? Alternatively is there a Signer object in the lib that isn't deprecated? I don't see one in the docs.
Expected behavior
Amplify provides an option to still sign a request given custom headers, or removes the mutual exclusiveness of the headers.
Reproduction steps
Configure Amplify for Auth and API > REST
Setup API Gateway with IAM Auth expecting the Authorization Header
Lambdas as API handlers expect x-api-token
API post with "x-api-key" is missing Authorization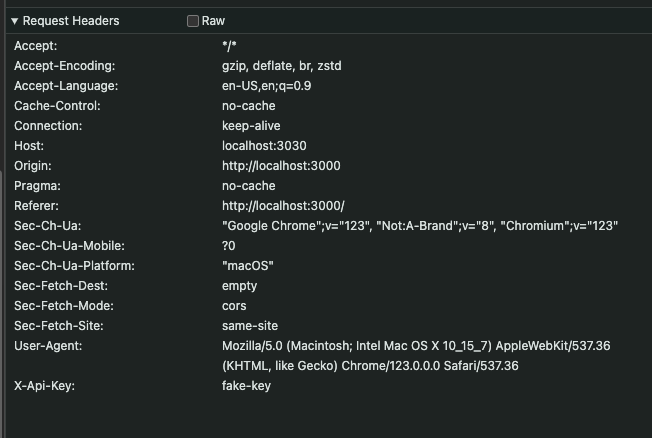
API post without "x-api-key" header has Authorization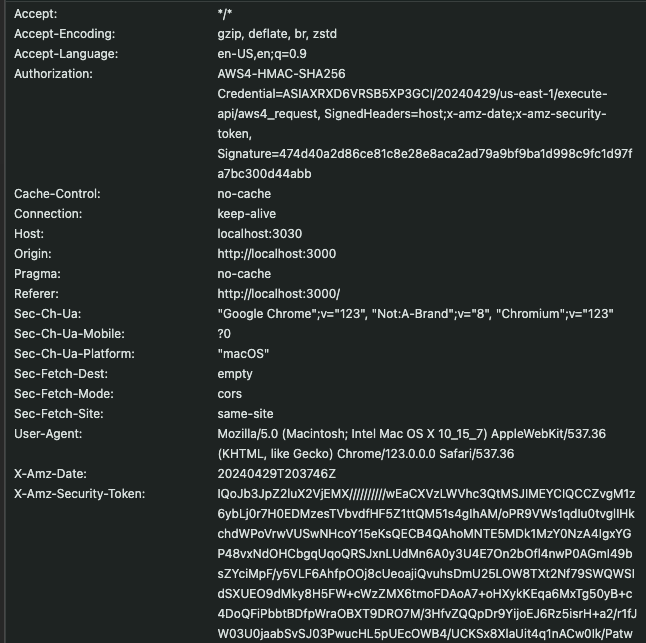
Code Snippet
Log output
aws-exports.js
No response
Manual configuration
No response
Additional configuration
No response
Mobile Device
No response
Mobile Operating System
No response
Mobile Browser
No response
Mobile Browser Version
No response
Additional information and screenshots
No response