Create a Fuzzing Snapshot
Create a VM overlay in a dedicated overlays folder: (Use the absolute path of windows.qcow2!) ./hAFL2/qemu-6.0.0/build/qemu-img create -f qcow2 -b windows.qcow2 overlay_0.qcow2 Run the VM overlay: ./hAFL2/qemu-6.0.0/build/x86_64-softmmu/qemu-system-x86_64 -enable-kvm -cpu host,hv_relaxed,hv_spinlocks=0x1fff,hv_vapic,hv_time,+intel-pt,-hypervisor,+vmx -usbdevice tablet -m 16384 -bios /root/hAFL2/OVMF_CODE-pure-efi.fd -drive file=overlay_0.qcow2 -machine q35
1. Retrieving VMSwitch.sys address range (Root Partition VM)
- Open a command prompt as an Administrator from within the root partition VM.
- Execute C:\info.exe as an Administrator.
- Check that hAFL2 server now has the /tmp/kAFL_info.txt file, and that it contains a loaded modules list of the root partition VM, with loaded address range for each modules. (Copy this file, you'll use it soon.)

2. Installing Crash Monitoring Driver (Root Partition VM)
- Install the Crash Monitoring Driver on the Root Partition VM:
- Execute OSRLoader.exe
- Change the Driver Path to C:\CrashMonitoringDriver.sys
- Click on "Register Service"
- Click on "Start Service"
- You may close the window now.

3. Installing Child Partition Harness Driver (Child Partition VM)
- Within the Child Partition VM, open dbgview64.exe as an Administrator.
Click on the Capture Menu, then click on Capture Kernel.
- Open a command prompt as an Administrator and install the CPHarness driver on the Child Partition VM by using devcon.exe (Approve the pop-up.)
C:\devcon.exe install CPHarness.inf root\CPHarness
- Check DbgView window, and look for the following log lines:
PoolVNC is OK + Channel is OK: [ADDRESS]
-
Note
If you don't see these log lines, you need to make sure you modified the ourName variable within the CPHarness driver according to the NDIS.sys offset of the Child Partition VM as stated before (explained in the one of the previous section.)
Occured issue
- Can not Find Miniport Channel

- Trouble shooting
~- Settings DEBUGPORT using
bcdedit.exefordebugging to kernel~~bcdedit /dbgsettings serial DEBUGPORT:2 BAUDRATE:115200~ ~bcdedit /debug on~
- Just Update Windows least Versin, and should modify miniportChannel offset at CPHarness sourcecode (and build)

- Just Update Windows least Versin, and should modify miniportChannel offset at CPHarness sourcecode (and build)
- Can not Find Miniport Channel
4. Creating the snapshot (Final Step)
Within the Child Partition VM, open a command prompt as an Administrator and execute C:\loader.exe
This will create a snapshot to which the fuzzer will return after crashes.
- Execute
C:loader.exewhithin Child Partition VM
- And than turn off QEMU automatically.

- Optional: Duplicating VM overlays
Make sure all of the overlays files are within the same overlays folder and execute the following command:
for f in overlay_{1..X}.qcow2; do cp overlay_0.qcow2 $f; done




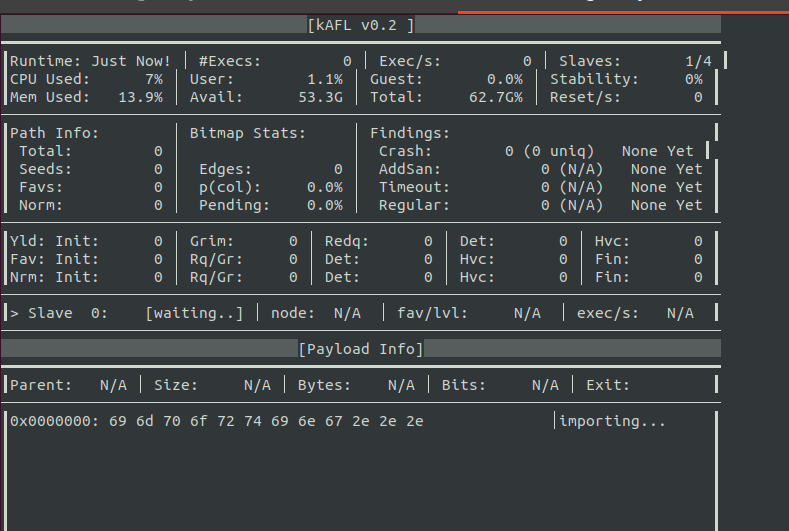










1. install kernel as hAFL2
2. install qemu6.0.0
3. install WindowsOS as level0 on QEMU
4. Setup Level2 VM within Level1
Turn off Level2 and Execute command using powershell within Level1
Run the following command from within PowerShell:
Turn on Level1 and Configuring
bcdedit.exewhtin Level25. Compile Necessary Binaries
Compile hAFL2’s fuzzing binaries by executing the following within bash:
Use Visual Studio to compile both drivers from within the hAFL2\drivers folder.
Within VS:
6. Optimizing the Crash Monitoring and Disabling DSE for Root Partition VM
Execute the Root Partition VM:~
In order to make the crash monitoring functionality operate faster, open PowerShell (within the root partition VM) as an Administrator and execute the following command:
Disable Driver Signature Enforcement from within an elevated command prompt (Restart the root partition VM once you're done):
7. Preparing the Root and Child Partition VMs for Fuzzing