Looks really cool👍🏼 for me an example in the module options would be nice, to know how and what to use it for (query domain admins? Get Domain Controllers?)
Closed Cyb3rC3lt closed 1 year ago
Looks really cool👍🏼 for me an example in the module options would be nice, to know how and what to use it for (query domain admins? Get Domain Controllers?)
Looks really cool👍🏼 for me an example in the module options would be nice, to know how and what to use it for (query domain admins? Get Domain Controllers?)
Just realised what you were suggesting so deleted my other comment😊. I will look into the module options idea, thanks for the feedback 👍🏻
Looks really cool👍🏼 for me an example in the module options would be nice, to know how and what to use it for (query domain admins? Get Domain Controllers?)
Just realised what you were suggesting so deleted my other comment😊. I will look into the module options idea, thanks for the feedback 👍🏻
Actually saw your comment😁 Maybe we can also add his documentation to the gitbook @mpgn, as soon as it gets merged into the private repo.
I've now added the usage on the command line Alex. You can check out a screenshot of what that looks like in the docs now. Code is also checked in.
https://github.com/Cyb3rC3lt/CrackMapExec-Modules
Anything else let me know David
Nice, thanks David👍🏼
Just added a useful change. I noticed on-site today that the 'Domain Admins' group was returning 1 member named Administrator but Bloodhound returned a few more. This was was because there was a nested group called 'Key_Admins' that contained the majority of DA's.
The updated code now returns any members of the 'Domain Admins' and also the name of any nested Groups in the Group so the results in this case returns two members: Administrator and KEY_ADMINS. This nested KEY_ADMINS group can then be further enumerated with the module.
I may look at traversing down this tree of groups and returning the nested group members if this is a common occurrence and it doesn't get too complicated quickly......Although if someone specify's Domain Admins it may not be entirely accurate to display members who happen to be in it via inheritance and it is better to keep it as-is with the nested group name. Hard to know what's best really.
I would argue, that this module is especially useful to quickly enumerate a group. Also displaying users in nested groups and so on would hide information, or even show a misleading picture.
If I would want to dive deep into the nested groups and its relations I can still fire up bloodhound imo. For my part, I like it as it is now
Edit: same for computers imo
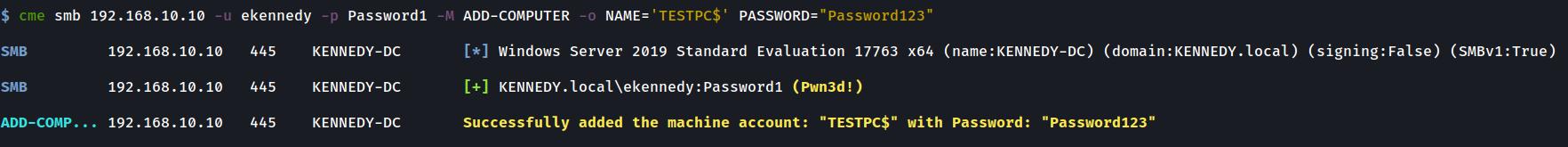
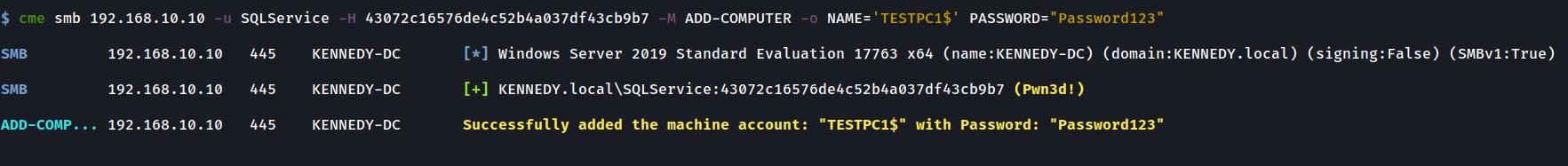
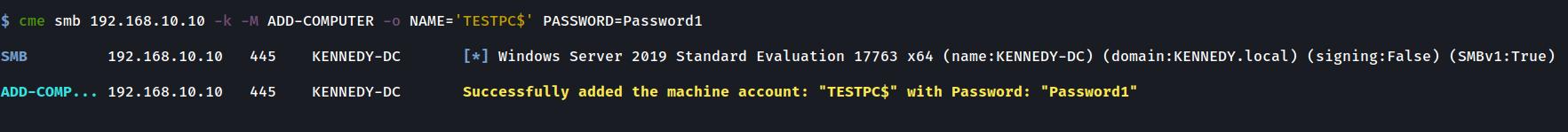
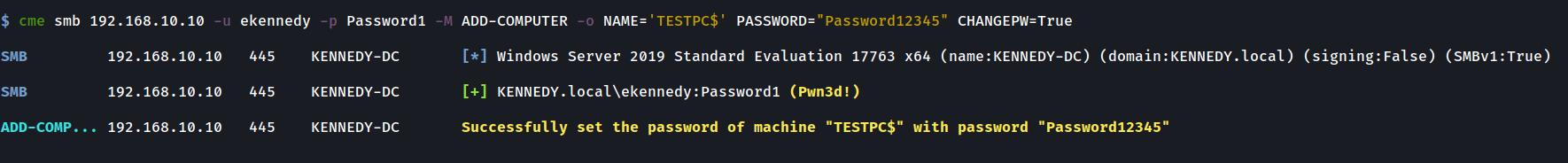
@mpgn I have just added a 3rd module which may be of use to you guys. It is a port of impackets Add Computer tool to CME. I have tested it well in my home lab and it seems to be working well. I will rename this pull request to reflect this too. Some images of it in action below:
Adding a Computer with credentials, hashes or using Kerberos
Changing a Computer password
Deleting a Computer
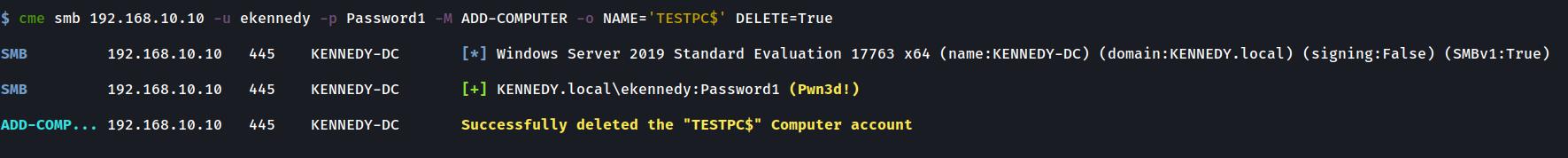
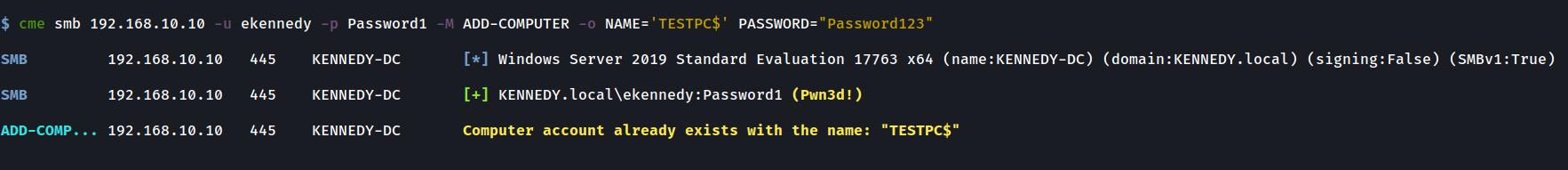
Error handling if a Computer already exists with that name
Hello @Cyb3rC3lt , can you make the PR on https://github.com/mpgn/CrackMapExec ?
Absolutely @mpgn I will move it across 👍🏻
thanks <3
Some really useful LDAP modules to enumerate the descriptions on computer objects and another module to enumerate all the members of the domain user and machine groups. Tested on a client site today with good effect.
Outputs with screenshots can be found here:
https://github.com/Cyb3rC3lt/CrackMapExec-Modules