Attaching full log in form of text file =
Open dg28gadhavi opened 6 years ago
Attaching full log in form of text file =
it looks like the current version did not handle msf correct, i could solve the problem by installing a old version of csploit, install msf and then replace csploit with the latest one.
Yeah still it will be great if it works again out of box with new apk as older version of apk doesn't seem to open it FC's :(
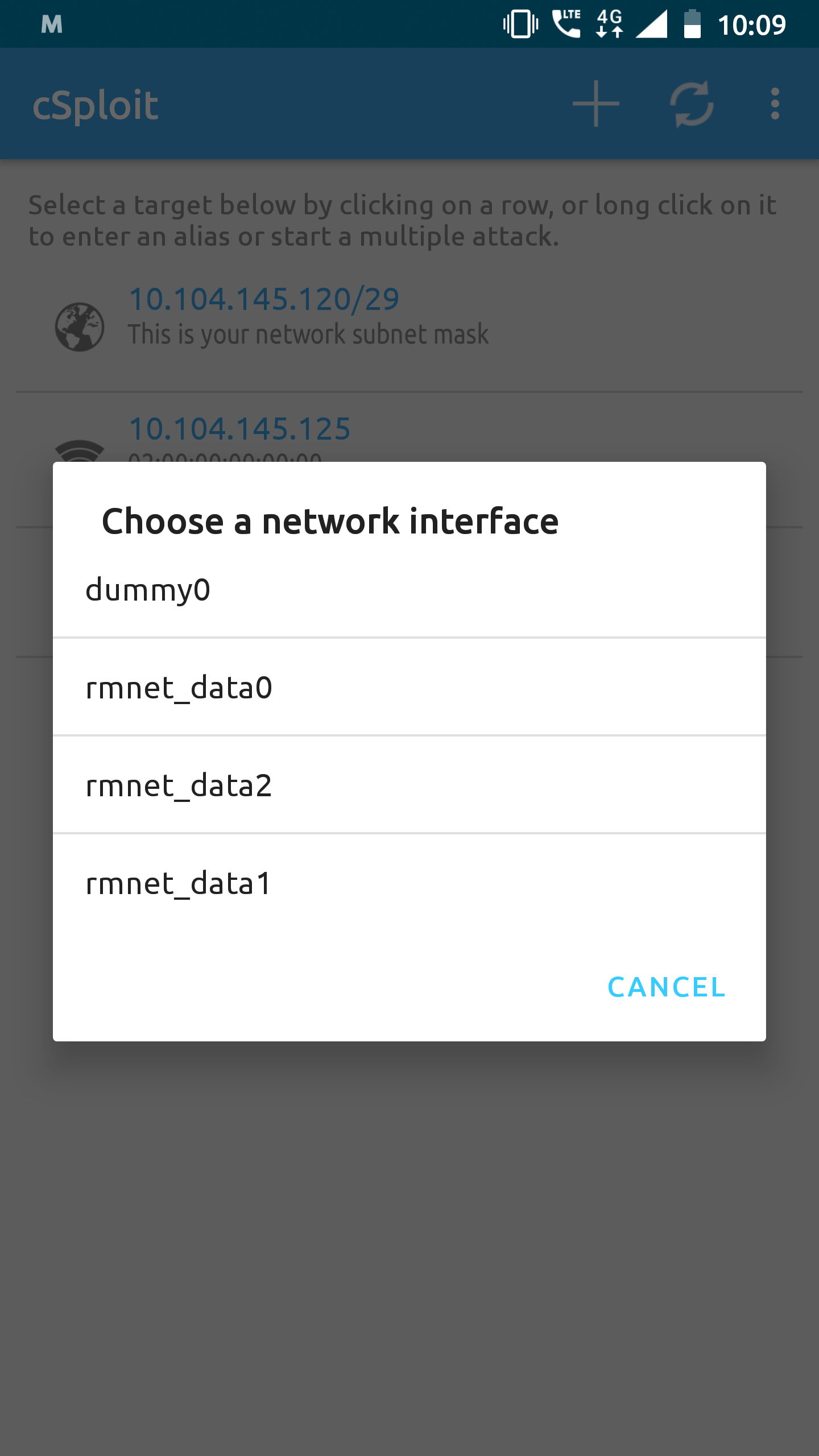
@Sor3nt Somehow managed to run Metasploit on latest nightly . The things that I did was
1) Changed selinux to permissive 2) Chosen rmnet_data1 network interface ( the rest 3 were giving errors ) 3) Restarted Metasploit. Voila it got connected :)
But @fat-tire Now I noticed a new bug Csploit is not able to detect Wifi networks available in WiFi scan :(
Screenshot's Attached :



Hmm. Regarding the first issue (ipv6?) if you're on an ipv4-only network, you still have the problem?
10-16 17:40:36.168 604 604 E SELinux : avc: denied { find } for interface=android.hardware.memtrack::IMemtrack pid=22697 scontext=u:r:untrusted_app:s0:c512,c768 tcontext=u:object_r:hal_memtrack_hwservice:s0 tclass=hwservice_manager permissive=0selinux is not a great idea to have running esp on newer Android versions that may deny things that earlier versions didn't. Definitely turn it off. Probably should have csploit turn it off actually.
Are you getting an actual crash of the app? I didn't notice a crash in the logs, but I looked quickly.
These problems seem to be related to lower level stuff than the java part of the app itself-- @tux-mind any thoughts?
I think i fixed it. I tried the selinux disable with no joy so i started looking for any log i could and i noticed superSU wouldnt always grant root so it ended with access granted but still no joy. I navigated to where it said the script was being executed with "cd /data/user/0/org.csploit.android/files" and after a annoying amount of toying i ran "ls -lah" and noticed the script had androids default user as the owner. So i ran "chown root:root start_daemon.sh" and idk if ilI needed to but "chmod 755 start_daemon.sh" all from SUterminal and everything works. Before it was 1/1000 chance it would connect it seemed very random but now if it doesnt connect by the time i run a scan on one of my devices i reset the app and let it try again but it seems to work now can reboot my device and it still works, before if it connected it wouldnt again after a reboot. I hope this helps people.
DEVICE: Nokia 8 ( msm8998 )
OS version: 8.1.0
cSploit version: v-1.7.0-unstable+70268d9
busybox (installed or not): Yes
Rooted with supersu? Yes ( magisk -17.1 )
Crash :
10-16 17:40:35.643 17050 22711 W CSPLOIT[services.MsfRpcdService.connect]: java.net.ConnectException: Failed to connect to /127.0.0.1:55553
10-16 17:40:35.644 17050 22711 D cSploitClient: parse_cmd: parsing "-P 'msf' -U 'msf' -p '55553' -a 127.0.0.1 -n -S -t Msg -f"
Seems like some "IPv6" issue