Hi, that's a good idea! I think Tor uses a built-in HTTPS Everywhere, which I also consider trustworthy. Smart-HTTPS, on the other hand, doesn't look so well maintained at first glance. But is there even an integrated solution from WebKit? That would be wonderful!
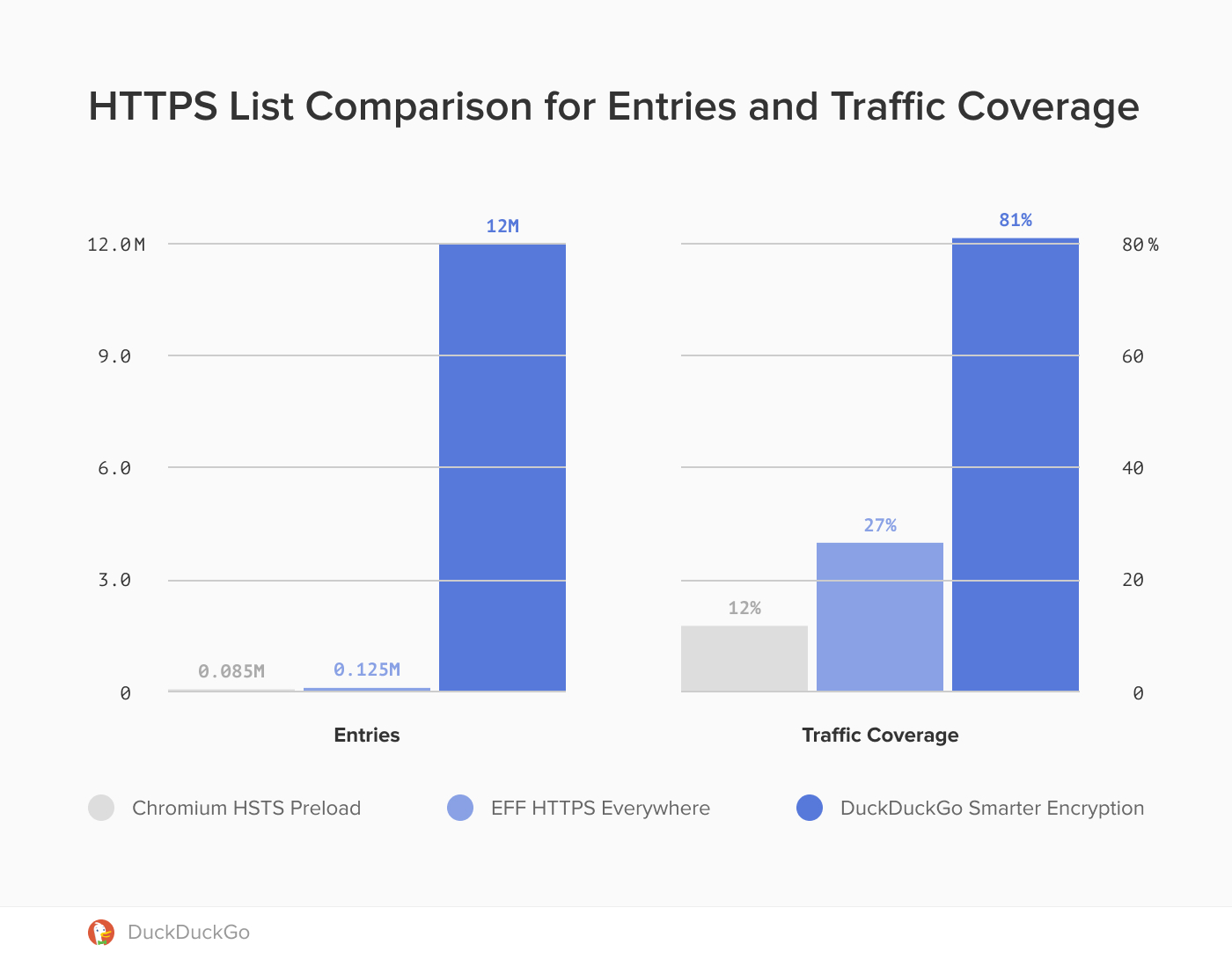
It would be best if it is done with a off switch for the session. Smart HTTPS extension for Firefox is a great example.