0xRobocop marked the issue as duplicate of #297
Open c4-bot-3 opened 6 months ago
0xRobocop marked the issue as duplicate of #297
3docSec changed the severity to 3 (High Risk)
3docSec marked the issue as satisfactory
3docSec marked the issue as selected for report
Upgraded as High because there is risk of value extraction from the protocol under conditions that can be monitored by an attacker.
Ondo has the ability to convert USDC to USD at a 1:1 rate and USD to BUIDL at a 1:1 rate, and this ability can be assumed. Should these abilities be removed this contract will be immediately paused. If someone is able to purchase USDC at a lower price to their benefit that should not negatively affect the protocol.
For the above reasons we do not believe this is a high severity issue.
cameronclifton marked the issue as disagree with severity
Hey @3docSec
This is a really really rare event. For proof, let's look at the USDC price chart.
Over the past 1 year, the price of USDC has moved the most by $0.001 (the difference between the highest and lowest value) and the price has been consistently maintained at $1 over the past year.
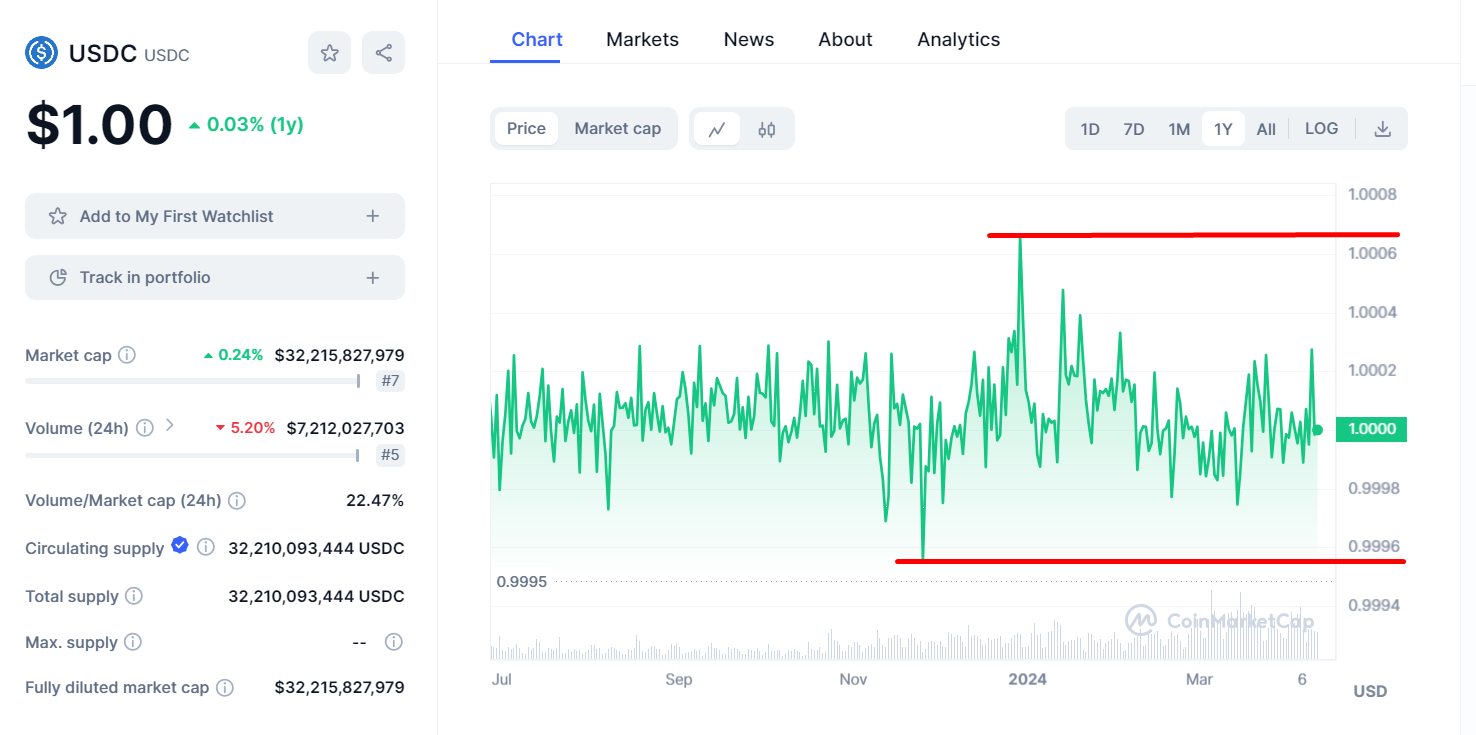
For the all time chart, the USDC low is $0.97 and the high is $1.034 (only $0.064 movement all time!).
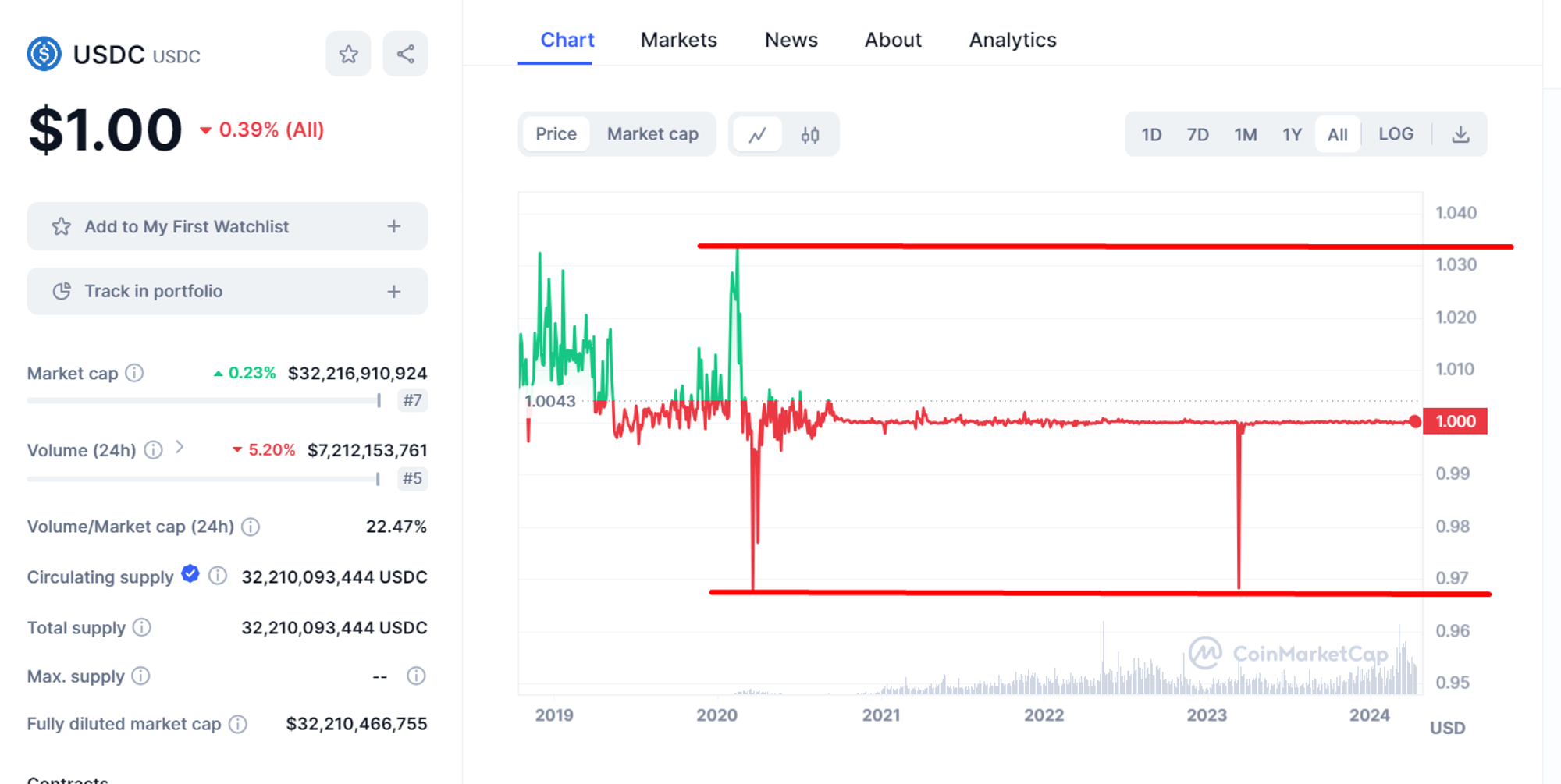
Source: coinmarketcap
Also, as the sponsor says above:
Should these abilities be removed this contract will be immediately paused. If someone is able to purchase USDC at a lower price to their benefit that should not negatively affect the protocol.
That being said, this issue should be considered as medium severity.
Noted, I'll think about it.
After further review, we will be mitigating this by adding a Chainlink USDC/USD oracle to the OUSGInsatntManager contract. If the price is lower than what we are comfortable with, all mints and redemptions will be blocked. While we think it is unlikely that we won't be able to convert USDC->USD 1:1 in our backend systems, we decided to do this out of extreme caution.
cameronclifton (sponsor) confirmed
Lines of code
https://github.com/code-423n4/2024-03-ondo-finance/blob/main/contracts/ousg/ousgInstantManager.sol#L307-L308
Vulnerability details
Proof of Concept
Any User can use
mintfunction inousgInstantManagercontract to mintOUSGtokens by providingUSDCtoken.It calls internal function
_mintwhere the main logic resides.2 important Points to understand here:
1. OUSG Price Stability:
The contract depends on the OUSG price obtained from an oracle, which is heavily constrained (As per Readme) to ensure stability.
As per
RWAOracleRateCheckOracle, Constraints includes:23 hours.1%.These constraints ensure relative stability of the OUSG price.
2. Calculation Assumptions:
The calculation of the amount of OUSG tokens to mint assumes a fixed conversion rate of
1 USDC = 1 USD.Key point:
_getMintAmountfunction calculates the OUSG amount based on the provided USDC amount and the OUSG price obtained from the oracle (By just upscaling and dividing).Here, There are No validation checks implemented regarding the current USDC price.
Scenario of Issue
Consider Alice's attempt to mint OUSG tokens by providing 100,000 USDC, assuming no minting fees and OUSG price of
105e18USD. The calculation yields:100_000e36 / 105e18which is approximately95_000e18or95_000OUSG tokens for the100_000USDC provided.However, in the event of a USDC depeg, where USDC's value deviates from 1 USD:
This scenario leads to Alice getting close to
95_000OUSG tokens again for100_000 USDCprovided But this time100_000 USDCcan be worth as low as87_000USD if we take recent depeg event in March 2023, where USDC price went as low as 87 cents (Reference).This way, contract will allow Users to mint excessive OUSG tokens during Depeg event.
Impact
Minting of Excessive Token in case of USDC Depeg.
Tools Used
VS Code
Recommended Mitigation Steps
Ideally, there needs to be an additional oracle to check current Price of USDC and take it's price into the consideration when calculation OUSG tokens to mint.
Assessed type
Context