MiloTruck marked the issue as not a duplicate
Closed howlbot-integration[bot] closed 2 months ago
MiloTruck marked the issue as not a duplicate
Invalid.
The DSS is assumed to be non-malicious - operators will only register and deploy vaults to a DSS that it trusts.
MiloTruck marked the issue as unsatisfactory: Invalid
MiloTruck marked the issue as unsatisfactory: Invalid
@MiloTruck 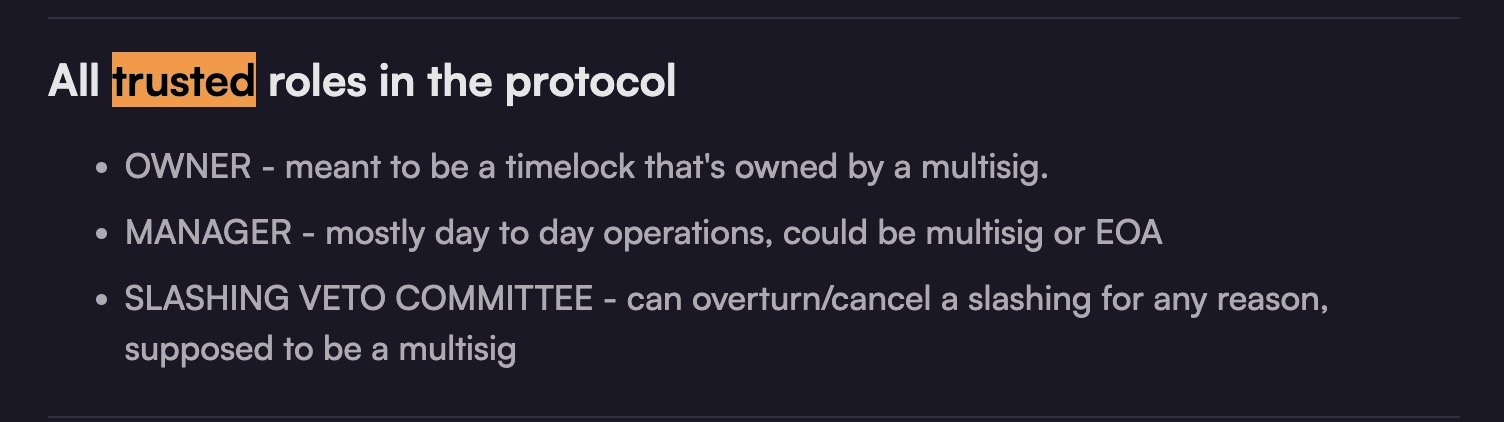
according to audit page we can see DSS is not a trusted role
Sure, here’s the translation:
Moreover, the most important thing is that finishRedeem and finalizeSlashing can be executed within the same transaction. This means that the so-called Slashing Veto Committee has no chance to detect the issue because, before the slash occurs, the DSS shares are still in the vault.
The DSS is not marked as trusted role, but it is an implicit assumption as operators have to manually register themselves to a DSS. They should be doing due diligence to ensure the DSS isn't malicious in the first place.
Also, from the sponsor:
This is kinda farfetched as if a malicious DSS just deposits and queue a withdrawal it's potentially exposing itself to get slashed by other DSSs too.
The DSS is not marked as trusted role, but it is an implicit assumption as operators have to manually register themselves to a DSS. They should be doing due diligence to ensure the DSS isn't malicious in the first place.
You are correct sir but the thing is, a DSS can behave maliciously in future maybe when the operator tries to Unstake from that DSS. Kinda Same thing that is happening in the #55, In that issue it should be DSS responsibility to check the operator's given slashingHandler but it is got accepted, and I totally understand why, because the code allows that to happen. Same is the case here, the code allows the DSS to turn malicious and slash 100% of the assets of an operator.
Also, from the sponsor: This is kinda farfetched as if a malicious DSS just deposits and queue a withdrawal it's potentially exposing itself to get slashed by other DSSs too.
This is correct as well but from my understanding an operator can have only one DSS.
Operators with one DSS will be most open to these attacks.
Lines of code
https://github.com/code-423n4/2024-07-karak/blob/main/src/Core.sol#L220-L231
Vulnerability details
Impact
DSS can deposit assets into the vault by oneself, which can lead to vault users losing more slashed assets.
Proof of Concept
The protocol implements two distinct time windows to manage asset withdrawals and slashing:
These time windows are designed to prevent users from circumventing slashing penalties by withdrawing assets prematurely.
However, a potential vulnerability exists in this mechanism: DSS, having control over the slashing timestamp and the ability to deposit assets into the vault, could exploit this system. The exploit would proceed as follows:
Just before calling finalizeSlashing at the end of the 2-day window, DSS withdraws the previously deposited assets.
test:
From above test we can see dssUser withdraw all assets from vault, and leave all slash to remaining vault user.
Tools Used
Foundry
Recommended Mitigation Steps
I don't have a good solution to mitigate the aforementioned issue. However, I am certain that DSS can cause vault users to lose more assets through the process described above。
Assessed type
Other