Yep, that's a pretty clear logic error. Will fix.
Closed zztytu closed 5 years ago
Yep, that's a pretty clear logic error. Will fix.
Ok, I think I see where things might be going wrong. It seems like this problem is specific to libnyociextra's nyoci_node_list_request_handler(). I don't see any logic errors in the code you pasted until you get to nyoci_node_list_request_handler().
If a Uri-path has a length of zero (totally valid), then I would expect nyoci_inbound_option_strequal_const(COAP_OPTION_URI_PATH,"") to return true when it reaches that option. Empty Uri-path options are totally normal.
If value_len is 0, the subsequent loop is not executed (line 163), and if the second argument cstr is an empty string, the return value is true (normal logic will return false in the loop)
I'm not sure what you mean. Why would "normal logic" return false in the loop? If our Uri-path option is empty, what else would value_len be?
In any case, fixing the handling of the prefix variable in nyoci_node_list_request_handler seems like what is needed.
I'm not immediately able to reproduce the issue. Could you send me a dump of a packet that reproduces the issue?
Or at least show me a larger amount of information about the CoAP packet from wireshark.
Ah, I figured out why I can't reproduce it. This issue was fixed by #12 (specifically d96723feaf24c260832ad44bb82d9947a9797424) last year. It was discovered by Bruno Menlo. The changes haven't yet made it into an official release.
src/libnyoci/coap.c lines 58-116:
If the data packet is processed as shown below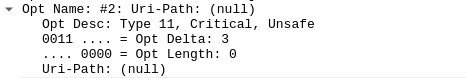 Then the function coap_decode_option will set the length parameter to 0,and the value_len in the function nyoci_inbound_option_strequal in src/libnyoci/nyoci-inbound.c is 0(lines 157-168)
Then the function coap_decode_option will set the length parameter to 0,and the value_len in the function nyoci_inbound_option_strequal in src/libnyoci/nyoci-inbound.c is 0(lines 157-168)
If value_len is 0, the subsequent loop is not executed (line 163), and if the second argument cstr is an empty string, the return value is true (normal logic will return false in the loop) The function nyoci_node_list_request_handler in src/libnyociextra/nyoci-list.c for handling requests calls nyoci_inbound_option_strequal_const, and the second argument passed in is an empty string(lines 85-89).
Therefore, the special data packet will pass the judgment, the program will enter the assignment to the variable prefix (the variable prefix is empty at this time), and the program eventually crashes.