Would be better if you can attach the pwn binary, otherwise it just looks like the binary doesn't use any seccomp filters.
And what's the output if you do strace -e ./pwn ?
Closed xiongsp closed 10 months ago
Would be better if you can attach the pwn binary, otherwise it just looks like the binary doesn't use any seccomp filters.
And what's the output if you do strace -e ./pwn ?
@Loora1N Could you provide the output of strace -f ./wenheap?
@david942j I'm sorry. I made a mistake myself. The binary does not use any seccomp filters, and seccomp-tools will work just fine. I'm really sorry to have caused you some trouble :(
@Loora1N it's okay ;)
@xiongsp could you provide the output of strace -f ./pwn?
Sorry for untracking this issue for a long time.Here are outputs when I run the command.
ubuntu@ubuntu2004:~/Desktop/pwn/anwangcup/pwn1$ strace -f ./pwn
execve("./pwn", ["./pwn"], 0x7ffc7dd56488 /* 48 vars */) = 0
brk(NULL) = 0x55e82fbe1000
arch_prctl(0x3001 /* ARCH_??? */, 0x7fff3ff57ea0) = -1 EINVAL (Invalid argument)
access("/etc/ld.so.preload", R_OK) = -1 ENOENT (No such file or directory)
openat(AT_FDCWD, "/etc/ld.so.cache", O_RDONLY|O_CLOEXEC) = 3
fstat(3, {st_mode=S_IFREG|0644, st_size=78997, ...}) = 0
mmap(NULL, 78997, PROT_READ, MAP_PRIVATE, 3, 0) = 0x7fd94b82b000
close(3) = 0
openat(AT_FDCWD, "/lib/x86_64-linux-gnu/libc.so.6", O_RDONLY|O_CLOEXEC) = 3
read(3, "\177ELF\2\1\1\3\0\0\0\0\0\0\0\0\3\0>\0\1\0\0\0\300A\2\0\0\0\0\0"..., 832) = 832
pread64(3, "\6\0\0\0\4\0\0\0@\0\0\0\0\0\0\0@\0\0\0\0\0\0\0@\0\0\0\0\0\0\0"..., 784, 64) = 784
pread64(3, "\4\0\0\0\20\0\0\0\5\0\0\0GNU\0\2\0\0\300\4\0\0\0\3\0\0\0\0\0\0\0", 32, 848) = 32
pread64(3, "\4\0\0\0\24\0\0\0\3\0\0\0GNU\0\30x\346\264ur\f|Q\226\236i\253-'o"..., 68, 880) = 68
fstat(3, {st_mode=S_IFREG|0755, st_size=2029592, ...}) = 0
mmap(NULL, 8192, PROT_READ|PROT_WRITE, MAP_PRIVATE|MAP_ANONYMOUS, -1, 0) = 0x7fd94b829000
pread64(3, "\6\0\0\0\4\0\0\0@\0\0\0\0\0\0\0@\0\0\0\0\0\0\0@\0\0\0\0\0\0\0"..., 784, 64) = 784
pread64(3, "\4\0\0\0\20\0\0\0\5\0\0\0GNU\0\2\0\0\300\4\0\0\0\3\0\0\0\0\0\0\0", 32, 848) = 32
pread64(3, "\4\0\0\0\24\0\0\0\3\0\0\0GNU\0\30x\346\264ur\f|Q\226\236i\253-'o"..., 68, 880) = 68
mmap(NULL, 2037344, PROT_READ, MAP_PRIVATE|MAP_DENYWRITE, 3, 0) = 0x7fd94b637000
mmap(0x7fd94b659000, 1540096, PROT_READ|PROT_EXEC, MAP_PRIVATE|MAP_FIXED|MAP_DENYWRITE, 3, 0x22000) = 0x7fd94b659000
mmap(0x7fd94b7d1000, 319488, PROT_READ, MAP_PRIVATE|MAP_FIXED|MAP_DENYWRITE, 3, 0x19a000) = 0x7fd94b7d1000
mmap(0x7fd94b81f000, 24576, PROT_READ|PROT_WRITE, MAP_PRIVATE|MAP_FIXED|MAP_DENYWRITE, 3, 0x1e7000) = 0x7fd94b81f000
mmap(0x7fd94b825000, 13920, PROT_READ|PROT_WRITE, MAP_PRIVATE|MAP_FIXED|MAP_ANONYMOUS, -1, 0) = 0x7fd94b825000
close(3) = 0
arch_prctl(ARCH_SET_FS, 0x7fd94b82a540) = 0
mprotect(0x7fd94b81f000, 16384, PROT_READ) = 0
mprotect(0x55e82f801000, 4096, PROT_READ) = 0
mprotect(0x7fd94b86c000, 4096, PROT_READ) = 0
munmap(0x7fd94b82b000, 78997) = 0
alarm(10) = 0
fstat(2, {st_mode=S_IFCHR|0620, st_rdev=makedev(0x88, 0), ...}) = 0
brk(NULL) = 0x55e82fbe1000
brk(0x55e82fc02000) = 0x55e82fc02000
write(2, "Wow!\n", 5Wow!
) = 5
write(2, "Do u know what's is it?\n", 24Do u know what's is it?
) = 24
read(0, 0x7fff3ff57d10, 57) = ? ERESTARTSYS (To be restarted if SA_RESTART is set)
--- SIGALRM {si_signo=SIGALRM, si_code=SI_KERNEL} ---
+++ killed by SIGALRM +++
Alarm clockThanks a lot.
I think there is no seccomp filter in this binary file.However, when I try to build following C code with command gcc -g 1.c -o simple_syscall_seccomp -lseccomp and run seccomp-tools dump simple_syscall_seccomp ,it still get an error.
//c code
#include <stdio.h>
#include <unisted.h>
#include <seccomp.h>
int main(void){
scmp_filter_ctx ctx;
ctx = seccomp_init(SCMP_ACT_ALLOW);
seccomp_rule_add(ctx, SCMP_ACT_KILL, SCMP_SYS(execve), 0);
seccomp_load(ctx);
char * filename = "/bin/sh";
char * argv[] = {"/bin/sh",NULL};
char * envp[] = {NULL};
write(1,"i will give you a shell\n",24);
syscall(59,filename,argv,envp);//execve
return 0;
}Error:
ubuntu@ubuntu2004:~/Desktop/tt$ seccomp-tools dump simple_syscall_seccomp
/bin/sh: 1: simple_syscall_seccomp: not found
ubuntu@ubuntu2004:~/Desktop/tt$ ls
1.c simple_syscall_seccompYou should do seccomp-tools dump ./simple_syscall_seccomp
You should do
seccomp-tools dump ./simple_syscall_seccomp
Here are what I tried:
ubuntu@ubuntu2004:~/Desktop/tt$ seccomp-tools dump ./simple_syscall_seccomp
i will give you a shell
ptrace syscall: No such process
Bad system call (core dumped)
ubuntu@ubuntu2004:~/Desktop/tt$ ./simple_syscall_seccomp
i will give you a shell
Bad system call (core dumped)It still runs the ELF file instead of showing the info.
Could you paste the output of strace -f ./simple_syscall_seccomp?
This is the output in a new VM.
parallels@parallels-Parallels-Virtual-Platform:~/Desktop/tst$ strace -f ./simple_syscall_seccomp
execve("./simple_syscall_seccomp", ["./simple_syscall_seccomp"], 0x7fff57751178 /* 62 vars */) = 0
brk(NULL) = 0x55fb5e67b000
arch_prctl(0x3001 /* ARCH_??? */, 0x7ffdf6659220) = -1 EINVAL (无效的参数)
access("/etc/ld.so.preload", R_OK) = -1 ENOENT (没有那个文件或目录)
openat(AT_FDCWD, "/etc/ld.so.cache", O_RDONLY|O_CLOEXEC) = 3
fstat(3, {st_mode=S_IFREG|0644, st_size=71879, ...}) = 0
mmap(NULL, 71879, PROT_READ, MAP_PRIVATE, 3, 0) = 0x7f04cd5c3000
close(3) = 0
openat(AT_FDCWD, "/lib/x86_64-linux-gnu/libseccomp.so.2", O_RDONLY|O_CLOEXEC) = 3
read(3, "\177ELF\2\1\1\0\0\0\0\0\0\0\0\0\3\0>\0\1\0\0\0 #\0\0\0\0\0\0"..., 832) = 832
fstat(3, {st_mode=S_IFREG|0644, st_size=133568, ...}) = 0
mmap(NULL, 8192, PROT_READ|PROT_WRITE, MAP_PRIVATE|MAP_ANONYMOUS, -1, 0) = 0x7f04cd5c1000
mmap(NULL, 135520, PROT_READ, MAP_PRIVATE|MAP_DENYWRITE, 3, 0) = 0x7f04cd59f000
mprotect(0x7f04cd5a1000, 122880, PROT_NONE) = 0
mmap(0x7f04cd5a1000, 61440, PROT_READ|PROT_EXEC, MAP_PRIVATE|MAP_FIXED|MAP_DENYWRITE, 3, 0x2000) = 0x7f04cd5a1000
mmap(0x7f04cd5b0000, 57344, PROT_READ, MAP_PRIVATE|MAP_FIXED|MAP_DENYWRITE, 3, 0x11000) = 0x7f04cd5b0000
mmap(0x7f04cd5bf000, 8192, PROT_READ|PROT_WRITE, MAP_PRIVATE|MAP_FIXED|MAP_DENYWRITE, 3, 0x1f000) = 0x7f04cd5bf000
close(3) = 0
openat(AT_FDCWD, "/lib/x86_64-linux-gnu/libc.so.6", O_RDONLY|O_CLOEXEC) = 3
read(3, "\177ELF\2\1\1\3\0\0\0\0\0\0\0\0\3\0>\0\1\0\0\0\300A\2\0\0\0\0\0"..., 832) = 832
pread64(3, "\6\0\0\0\4\0\0\0@\0\0\0\0\0\0\0@\0\0\0\0\0\0\0@\0\0\0\0\0\0\0"..., 784, 64) = 784
pread64(3, "\4\0\0\0\20\0\0\0\5\0\0\0GNU\0\2\0\0\300\4\0\0\0\3\0\0\0\0\0\0\0", 32, 848) = 32
pread64(3, "\4\0\0\0\24\0\0\0\3\0\0\0GNU\0\30x\346\264ur\f|Q\226\236i\253-'o"..., 68, 880) = 68
fstat(3, {st_mode=S_IFREG|0755, st_size=2029592, ...}) = 0
pread64(3, "\6\0\0\0\4\0\0\0@\0\0\0\0\0\0\0@\0\0\0\0\0\0\0@\0\0\0\0\0\0\0"..., 784, 64) = 784
pread64(3, "\4\0\0\0\20\0\0\0\5\0\0\0GNU\0\2\0\0\300\4\0\0\0\3\0\0\0\0\0\0\0", 32, 848) = 32
pread64(3, "\4\0\0\0\24\0\0\0\3\0\0\0GNU\0\30x\346\264ur\f|Q\226\236i\253-'o"..., 68, 880) = 68
mmap(NULL, 2037344, PROT_READ, MAP_PRIVATE|MAP_DENYWRITE, 3, 0) = 0x7f04cd3ad000
mmap(0x7f04cd3cf000, 1540096, PROT_READ|PROT_EXEC, MAP_PRIVATE|MAP_FIXED|MAP_DENYWRITE, 3, 0x22000) = 0x7f04cd3cf000
mmap(0x7f04cd547000, 319488, PROT_READ, MAP_PRIVATE|MAP_FIXED|MAP_DENYWRITE, 3, 0x19a000) = 0x7f04cd547000
mmap(0x7f04cd595000, 24576, PROT_READ|PROT_WRITE, MAP_PRIVATE|MAP_FIXED|MAP_DENYWRITE, 3, 0x1e7000) = 0x7f04cd595000
mmap(0x7f04cd59b000, 13920, PROT_READ|PROT_WRITE, MAP_PRIVATE|MAP_FIXED|MAP_ANONYMOUS, -1, 0) = 0x7f04cd59b000
close(3) = 0
mmap(NULL, 12288, PROT_READ|PROT_WRITE, MAP_PRIVATE|MAP_ANONYMOUS, -1, 0) = 0x7f04cd3aa000
arch_prctl(ARCH_SET_FS, 0x7f04cd3aa740) = 0
mprotect(0x7f04cd595000, 16384, PROT_READ) = 0
mprotect(0x7f04cd5bf000, 4096, PROT_READ) = 0
mprotect(0x55fb5e0a1000, 4096, PROT_READ) = 0
mprotect(0x7f04cd602000, 4096, PROT_READ) = 0
munmap(0x7f04cd5c3000, 71879) = 0
seccomp(SECCOMP_SET_MODE_STRICT, 1, NULL) = -1 EINVAL (无效的参数)
seccomp(SECCOMP_SET_MODE_FILTER, SECCOMP_FILTER_FLAG_TSYNC, NULL) = -1 EFAULT (错误的地址)
seccomp(SECCOMP_SET_MODE_FILTER, SECCOMP_FILTER_FLAG_LOG, NULL) = -1 EFAULT (错误的地址)
seccomp(SECCOMP_GET_ACTION_AVAIL, 0, [SECCOMP_RET_LOG]) = 0
seccomp(SECCOMP_GET_ACTION_AVAIL, 0, [SECCOMP_RET_KILL_PROCESS]) = 0
seccomp(SECCOMP_SET_MODE_FILTER, SECCOMP_FILTER_FLAG_SPEC_ALLOW, NULL) = -1 EFAULT (错误的地址)
seccomp(SECCOMP_SET_MODE_FILTER, SECCOMP_FILTER_FLAG_NEW_LISTENER, NULL) = -1 EFAULT (错误的地址)
seccomp(SECCOMP_GET_NOTIF_SIZES, 0, 0x7ffdf6659182) = 0
seccomp(SECCOMP_SET_MODE_FILTER, 0x10 /* SECCOMP_FILTER_FLAG_??? */, NULL) = -1 EFAULT (错误的地址)
brk(NULL) = 0x55fb5e67b000
brk(0x55fb5e69c000) = 0x55fb5e69c000
prctl(PR_SET_NO_NEW_PRIVS, 1, 0, 0, 0) = 0
seccomp(SECCOMP_SET_MODE_FILTER, 0, {len=8, filter=0x55fb5e67bf60}) = 0
write(1, "i will give you a shell\n", 24i will give you a shell
) = 24
execve("/bin/sh", ["/bin/sh"], 0x7ffdf66591d8 /* 0 vars */) = 59
+++ killed by SIGSYS (core dumped) +++
错误的系统调用 (核心已转储)And it shows what I expect!
Now I am home and I cant access the old VM. So I am not sure whether it works on that VM. But I will check the old one when I go back. Maybe in Feb.
Weird it works perfectly on my side
$ cat a.c
#include <stdio.h>
#include <unistd.h>
#include <seccomp.h>
int main(void){
scmp_filter_ctx ctx;
ctx = seccomp_init(SCMP_ACT_ALLOW);
seccomp_rule_add(ctx, SCMP_ACT_KILL, SCMP_SYS(execve), 0);
seccomp_load(ctx);
char * filename = "/bin/sh";
char * argv[] = {"/bin/sh",NULL};
char * envp[] = {NULL};
write(1,"i will give you a shell\n",24);
syscall(59,filename,argv,envp);//execve
return 0;
}$ gcc a.c -o a -lseccomp
$ ./a
i will give you a shell
[1] 565736 invalid system call (core dumped) ./a
$ seccomp-tools dump ./a
line CODE JT JF K
=================================
0000: 0x20 0x00 0x00 0x00000004 A = arch
0001: 0x15 0x00 0x05 0xc000003e if (A != ARCH_X86_64) goto 0007
0002: 0x20 0x00 0x00 0x00000000 A = sys_number
0003: 0x35 0x00 0x01 0x40000000 if (A < 0x40000000) goto 0005
0004: 0x15 0x00 0x02 0xffffffff if (A != 0xffffffff) goto 0007
0005: 0x15 0x01 0x00 0x0000003b if (A == execve) goto 0007
0006: 0x06 0x00 0x00 0x7fff0000 return ALLOW
0007: 0x06 0x00 0x00 0x00000000 return KILLmeet same issue too , like this
i cant get any sec info , and tested on Kali-Linux and Ubuntu 18.04
the binary file is : https://drive.google.com/file/d/1mN8iv1V2oxoIulstGEquJ60t03VVzqBU/view?usp=sharing
for the strace -f , its stuck at the read.
└─# strace -f ./shellcode
execve("./shellcode", ["./shellcode"], 0x7ffd550b7e58 /* 55 vars */) = 0
brk(NULL) = 0x56240151f000
mmap(NULL, 8192, PROT_READ|PROT_WRITE, MAP_PRIVATE|MAP_ANONYMOUS, -1, 0) = 0x7f196fc85000
access("/etc/ld.so.preload", R_OK) = -1 ENOENT (No such file or directory)
openat(AT_FDCWD, "/etc/ld.so.cache", O_RDONLY|O_CLOEXEC) = 3
newfstatat(3, "", {st_mode=S_IFREG|0644, st_size=78394, ...}, AT_EMPTY_PATH) = 0
mmap(NULL, 78394, PROT_READ, MAP_PRIVATE, 3, 0) = 0x7f196fc71000
close(3) = 0
openat(AT_FDCWD, "/lib/x86_64-linux-gnu/libc.so.6", O_RDONLY|O_CLOEXEC) = 3
read(3, "\177ELF\2\1\1\3\0\0\0\0\0\0\0\0\3\0>\0\1\0\0\0\300\223\2\0\0\0\0\0"..., 832) = 832
pread64(3, "\6\0\0\0\4\0\0\0@\0\0\0\0\0\0\0@\0\0\0\0\0\0\0@\0\0\0\0\0\0\0"..., 784, 64) = 784
pread64(3, "\4\0\0\0\20\0\0\0\5\0\0\0GNU\0\2\200\0\300\4\0\0\0\1\0\0\0\0\0\0\0", 32, 848) = 32
pread64(3, "\4\0\0\0\24\0\0\0\3\0\0\0GNU\0q\247\307\271{\300\263\343I\243\330d\2ReU"..., 68, 880) = 68
newfstatat(3, "", {st_mode=S_IFREG|0755, st_size=2061320, ...}, AT_EMPTY_PATH) = 0
pread64(3, "\6\0\0\0\4\0\0\0@\0\0\0\0\0\0\0@\0\0\0\0\0\0\0@\0\0\0\0\0\0\0"..., 784, 64) = 784
mmap(NULL, 2109328, PROT_READ, MAP_PRIVATE|MAP_DENYWRITE, 3, 0) = 0x7f196fa00000
mmap(0x7f196fa28000, 1507328, PROT_READ|PROT_EXEC, MAP_PRIVATE|MAP_FIXED|MAP_DENYWRITE, 3, 0x28000) = 0x7f196fa28000
mmap(0x7f196fb98000, 360448, PROT_READ, MAP_PRIVATE|MAP_FIXED|MAP_DENYWRITE, 3, 0x198000) = 0x7f196fb98000
mmap(0x7f196fbf0000, 24576, PROT_READ|PROT_WRITE, MAP_PRIVATE|MAP_FIXED|MAP_DENYWRITE, 3, 0x1f0000) = 0x7f196fbf0000
mmap(0x7f196fbf6000, 53136, PROT_READ|PROT_WRITE, MAP_PRIVATE|MAP_FIXED|MAP_ANONYMOUS, -1, 0) = 0x7f196fbf6000
close(3) = 0
mmap(NULL, 12288, PROT_READ|PROT_WRITE, MAP_PRIVATE|MAP_ANONYMOUS, -1, 0) = 0x7f196fc6e000
arch_prctl(ARCH_SET_FS, 0x7f196fc6e740) = 0
set_tid_address(0x7f196fc6ea10) = 294146
set_robust_list(0x7f196fc6ea20, 24) = 0
rseq(0x7f196fc6f0e0, 0x20, 0, 0x53053053) = 0
mprotect(0x7f196fbf0000, 16384, PROT_READ) = 0
mprotect(0x562400fda000, 4096, PROT_READ) = 0
mprotect(0x7f196fcba000, 8192, PROT_READ) = 0
prlimit64(0, RLIMIT_STACK, NULL, {rlim_cur=8192*1024, rlim_max=RLIM64_INFINITY}) = 0
munmap(0x7f196fc71000, 78394) = 0
prctl(PR_SET_NO_NEW_PRIVS, 1, 0, 0, 0) = 0
prctl(PR_SET_SECCOMP, SECCOMP_MODE_FILTER, {len=4, filter=0x7fff9be2b540}) = -1 EINVAL (Invalid argument)
write(1, "test NSS sandbox", 16test NSS sandbox) = 16
write(1, "\n", 1
) = 1
mmap(0x50000, 4096, PROT_READ|PROT_WRITE|PROT_EXEC, MAP_PRIVATE|MAP_FIXED|MAP_ANONYMOUS, -1, 0) = 0x50000
read(0, ^Cstrace: Process 294146 detached
<detached...>```
by the way , any binary file for me is same issue. no sec-info.Hi @XKaguya, thanks for your report!
However in your logs,
prctl(PR_SET_SECCOMP, SECCOMP_MODE_FILTER, {len=4, filter=0x7fff9be2b540}) = -1 EINVAL (Invalid argument) the seccomp call registration failed. So having no seccomp info sounds like an expected behavior to me.
Hi @XKaguya, thanks for your report! However in your logs,
prctl(PR_SET_SECCOMP, SECCOMP_MODE_FILTER, {len=4, filter=0x7fff9be2b540}) = -1 EINVAL (Invalid argument)the seccomp call registration failed. So having no seccomp info sounds like an expected behavior to me.
actually not only this binary file
└─# strace -f ./vuln
execve("./vuln", ["./vuln"], 0x7ffd7ff21d38 /* 54 vars */) = 0
brk(NULL) = 0x55ce9ddf8000
mmap(NULL, 8192, PROT_READ|PROT_WRITE, MAP_PRIVATE|MAP_ANONYMOUS, -1, 0) = 0x7fcbffc5b000
access("/etc/ld.so.preload", R_OK) = -1 ENOENT (No such file or directory)
openat(AT_FDCWD, "/etc/ld.so.cache", O_RDONLY|O_CLOEXEC) = 3
newfstatat(3, "", {st_mode=S_IFREG|0644, st_size=78394, ...}, AT_EMPTY_PATH) = 0
mmap(NULL, 78394, PROT_READ, MAP_PRIVATE, 3, 0) = 0x7fcbffc47000
close(3) = 0
openat(AT_FDCWD, "/lib/x86_64-linux-gnu/libc.so.6", O_RDONLY|O_CLOEXEC) = 3
read(3, "\177ELF\2\1\1\3\0\0\0\0\0\0\0\0\3\0>\0\1\0\0\0\300\223\2\0\0\0\0\0"..., 832) = 832
pread64(3, "\6\0\0\0\4\0\0\0@\0\0\0\0\0\0\0@\0\0\0\0\0\0\0@\0\0\0\0\0\0\0"..., 784, 64) = 784
pread64(3, "\4\0\0\0\20\0\0\0\5\0\0\0GNU\0\2\200\0\300\4\0\0\0\1\0\0\0\0\0\0\0", 32, 848) = 32
pread64(3, "\4\0\0\0\24\0\0\0\3\0\0\0GNU\0q\247\307\271{\300\263\343I\243\330d\2ReU"..., 68, 880) = 68
newfstatat(3, "", {st_mode=S_IFREG|0755, st_size=2061320, ...}, AT_EMPTY_PATH) = 0
pread64(3, "\6\0\0\0\4\0\0\0@\0\0\0\0\0\0\0@\0\0\0\0\0\0\0@\0\0\0\0\0\0\0"..., 784, 64) = 784
mmap(NULL, 2109328, PROT_READ, MAP_PRIVATE|MAP_DENYWRITE, 3, 0) = 0x7fcbffa00000
mmap(0x7fcbffa28000, 1507328, PROT_READ|PROT_EXEC, MAP_PRIVATE|MAP_FIXED|MAP_DENYWRITE, 3, 0x28000) = 0x7fcbffa28000
mmap(0x7fcbffb98000, 360448, PROT_READ, MAP_PRIVATE|MAP_FIXED|MAP_DENYWRITE, 3, 0x198000) = 0x7fcbffb98000
mmap(0x7fcbffbf0000, 24576, PROT_READ|PROT_WRITE, MAP_PRIVATE|MAP_FIXED|MAP_DENYWRITE, 3, 0x1f0000) = 0x7fcbffbf0000
mmap(0x7fcbffbf6000, 53136, PROT_READ|PROT_WRITE, MAP_PRIVATE|MAP_FIXED|MAP_ANONYMOUS, -1, 0) = 0x7fcbffbf6000
close(3) = 0
mmap(NULL, 12288, PROT_READ|PROT_WRITE, MAP_PRIVATE|MAP_ANONYMOUS, -1, 0) = 0x7fcbffc44000
arch_prctl(ARCH_SET_FS, 0x7fcbffc44740) = 0
set_tid_address(0x7fcbffc44a10) = 1497
set_robust_list(0x7fcbffc44a20, 24) = 0
rseq(0x7fcbffc450e0, 0x20, 0, 0x53053053) = 0
mprotect(0x7fcbffbf0000, 16384, PROT_READ) = 0
mprotect(0x55ce9db1a000, 4096, PROT_READ) = 0
mprotect(0x7fcbffc90000, 8192, PROT_READ) = 0
prlimit64(0, RLIMIT_STACK, NULL, {rlim_cur=8192*1024, rlim_max=RLIM64_INFINITY}) = 0
munmap(0x7fcbffc47000, 78394) = 0
mmap(0xcafe0000, 4096, PROT_READ|PROT_WRITE|PROT_EXEC, MAP_SHARED|MAP_ANONYMOUS, -1, 0) = 0xcafe0000
write(1, "Please input your shellcode:", 28Please input your shellcode:) = 28
write(1, "\n", 1
) = 1
read(0, ^C0xcafe0000, 16) = ? ERESTARTSYS (To be restarted if SA_RESTART is set)
strace: Process 1497 detached... wait a sec , seems some file works fine , but some doesn't work , just like this.
so this still a expected behavior too ? if then should manually check lol
In your strace logs of ./vuln, the binary didn't register seccomp filter. So yes it's expected.
Maybe I found the solution.You can try installing libseccomp-dev
sudo apt-get install libseccomp-devand then, using seccomp-tools dump ./a, you can see the result
seccomp-tools dump ./a
line CODE JT JF K
=================================
0000: 0x20 0x00 0x00 0x00000004 A = arch
0001: 0x15 0x00 0x05 0xc000003e if (A != ARCH_X86_64) goto 0007
0002: 0x20 0x00 0x00 0x00000000 A = sys_number
0003: 0x35 0x00 0x01 0x40000000 if (A < 0x40000000) goto 0005
0004: 0x15 0x00 0x02 0xffffffff if (A != 0xffffffff) goto 0007
0005: 0x15 0x01 0x00 0x0000003b if (A == execve) goto 0007
0006: 0x06 0x00 0x00 0x7fff0000 return ALLOW
0007: 0x06 0x00 0x00 0x00000000 return KILLThanks! I am closing this issue then.
Some basic infomation: System:
Files in the workdir:
I want to get the sec-info by using following command line:
As expects, it should demostrate some info like these: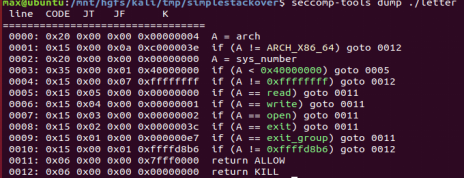
However, it just run my ELF file instead of showing them:
The following command lines have been tested with no work:
Is this a bug, or I didn't run it as a correct way?