Ok, I found somethings.. I want to share, maybe we can find the solution together;
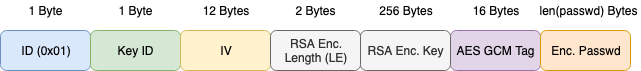
I believe this is rc-40 crypto.. Not sure but it looks like rc-40. Anyway, I have public key but I couldn't decrypt it.. public key returns on header; LS0tLS1CRUdJTiBQVUJMSUMgS0VZLS0tLS0KTUlJQklqQU5CZ2txaGtpRzl3MEJBUUVGQUFPQ0FROEFNSUlCQ2dLQ0FRRUF1enRZOEZvUlRGRU9mK1RkTGlUdAplN3FIQXY1cmdBMmk5RkQ0YjgzZk1GK3hheW14b0xSdU5KTitRanJ3dnBuSm1LQ0QxNGd3K2w3TGQ0RHkvRHVFCkRiZlpKcmRRWkJIT3drS3RqdDdkNWlhZFdOSjdLczlBM0NNbzB5UktyZFBGU1dsS21lQVJsTlFrVXF0YkNmTzcKT2phY3ZYV2dJcGlqTkdJRVk4UkdzRWJWZmdxSmsrZzhuQWZiT0xjNmEwbTMxckJWZUJ6Z0hkYWExeFNKOGJHcQplbG4zbWh4WDU2cmpTOG5LZGk4MzRZSlNaV3VxUHZmWWUrbEV6Nk5laU1FMEo3dE80eWxmeWlPQ05ycnF3SnJnCjBXWTFEeDd4MHlZajdrN1NkUWVLVUVaZ3FjNUFuVitjNUQ2SjJTSTlGMnNoZWxGNWVvZjJOYkl2TmFNakpSRDgKb1FJREFRQUIKLS0tLS1FTkQgUFVCTElDIEtFWS0tLS0tCg==
Question
Hello people, I got a new header value. I just wanna ask, have you ever see that and do you know how can I generate it? That's my value. "enc_password":"#PWD_INSTAGRAM:4:1575910572:Ac09XDpcBE1cB/lOovUAAUfoGhWI59ZQtRLVbpku9bHOJAUNZOszYmzbaV7bWVwrc/AgVoPvn4Sm68625fI4S9CUyqR7PYkSvaXdsD98JmhQFBRjntw/2eR93Wqxzq05AGmcdiXcNaboW2ltmkWFoUL8fZnfbNtoXVVVZ6n7aYFplud2UJ+A/zYFVsTSsoGbvdBIyjttMKcNQNsotAo95pA+v99q39PRZ0ug3B7GrfOayV+t7OTointqxZjoxYtjmqda4n7kBsruEVW7yBfnAU0k9pWScVtjJXEkoGejJtDbd5RUBUPJVJIlVDjCgLZ2hmKYOYO16C5nvFNx3jkc4AwujIZOl6mqlhKs+Xehmr33Nk7euoe8Lj3XPDH1HpiYuSxBI1Lp1Rm8JzM="