I have used the current master of Sirius Web and moved the Authorization header to the frontend. See https://github.com/Gelio/sirius-web/commit/27d862c1796546ca64dc2adeb577991e26a114ec
GraphQL queries and mutations now correctly expect the header to be sent via the frontend and result in 401 errors if the header is not present. GraphQL subscriptions seem to work without any headers. This is not what I observed on https://github.com/Gelio/CAL-web/pull/97 where I was getting connection_error responses via WebSocket:
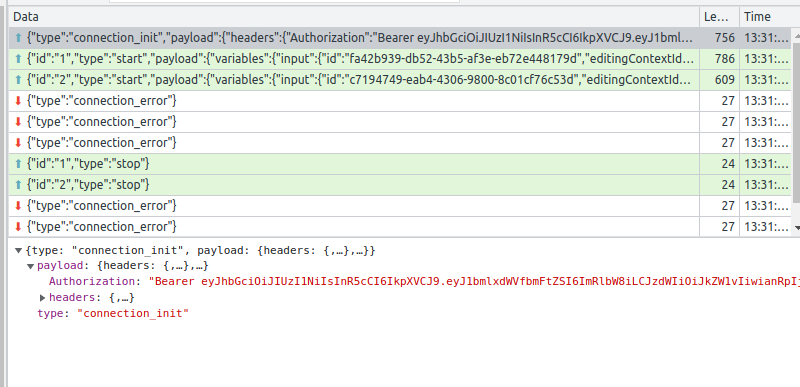
Presumably this is because on my branch with JWT authentication I removed https://github.com/eclipse-sirius/sirius-web/blob/0866885f5ed3c3f4ee758c756d4c25c2d7f8fb94/backend/sirius-web-sample-application/src/main/java/org/eclipse/sirius/web/sample/configuration/SpringWebSecurityConfiguration.java#L52
and thus, there is likely no principal set in https://github.com/eclipse-sirius/sirius-components/blob/ab8097c6c3593f10fdd16f9212762624a3639ccc/backend/sirius-web-spring-graphql/src/main/java/org/eclipse/sirius/web/spring/graphql/ws/GraphQLWebSocketHandler.java#L244-L245 which results in the errors I am seeing on my branch.
This does not solve the problem, because I want to use JWT-based authentication.
I am using Sirius Web to build a diagram editor (see my fork: https://github.com/Gelio/CAL-web). I have gotten to a point that I want to enable authentication and authorize users so they only see projects they own. I am using JWT-based authentication, but I don't think that should matter.
I have successfully added authentication to regular REST endpoints, as well as the GraphQL query/mutation endpoint (
/api/graphql). I have trouble adding authentication to WebSocket connections (GraphQL subscriptions using the/subscriptions) endpoint.So far I found that the
Authorizationheader (or any other custom header, for that matter) is not passed when using WebSockets (source). WebSocket authorization has to be done in other ways, usually through sending the authentication information in one of the initial messages.This leads me to believe that authenticating WebSocket connections is at the moment not possible without modifications to
sirius-components. To be concrete, from what I found I would either need to:Register a
HandshakeInterceptorfor theWebSocketHandlerRegistrationin https://github.com/eclipse-sirius/sirius-components/blob/ab8097c6c3593f10fdd16f9212762624a3639ccc/backend/sirius-web-spring-graphql/src/main/java/org/eclipse/sirius/web/spring/graphql/configuration/WebSocketConfiguration.java#L63-L64 and somehow set thePrincipalthere. Some related StackOverflow questions on thisThe problem here is that custom headers are not sent by browsers in WebSocket connections, so the HTTP connection itself will be void of any authentication data, so the interceptor won't be able to set anything. The authentication data would come in a subsequent WebSocket message, but that's already past the interceptor's job.
Extract the
Authorizationtoken from the payload sent in theconnection_initinitial WebSocket message, but that happens inGraphQLWebSocketHandler, which I believe I cannot modify from Sirius Web: https://github.com/eclipse-sirius/sirius-components/blob/ab8097c6c3593f10fdd16f9212762624a3639ccc/backend/sirius-web-spring-graphql/src/main/java/org/eclipse/sirius/web/spring/graphql/ws/GraphQLWebSocketHandler.java#L243-L256This would seem like the most correct solution.
From what I could tell, in Sirius Web the WebSocket connections work fine due to the
SiriusWebAuthenticationFilter, which appendsAuthorizationheaders to all requests (both regular HTTP API requests and WebSocket connections). This seems like a hack that hides the fact that WebSocket requests cannot have such headers because browsers just don't send them (source). I expect that if we removedSiriusWebAuthenticationFilterand instead attached theAuthorizationheader to all API requests, the problem with WebSocket connections missing authentication information would be surfaced.If it is possible at the moment to authenticate WebSocket connections and I have missed something, let me know. If not, I would appreciate making the changes to allow passing authentication data to those connections
My authentication-related work is generally described https://github.com/Gelio/CAL-web/issues/96 (see https://github.com/Gelio/CAL-web/issues/96#issuecomment-980572837 for a description of the problem) and implemented so far in https://github.com/Gelio/CAL-web/pull/97. You can use the JAR built in CI (https://github.com/Gelio/CAL-web/actions/runs/1510579015) if you want to test it yourselves.