To track the vulnerability present in indirect dependencies we can use mvn:dependencies output shore here dependencies.txt
Open dineshr93 opened 1 year ago
To track the vulnerability present in indirect dependencies we can use mvn:dependencies output shore here dependencies.txt
SPDX SBOM for sw360 847ebac manifest.spdx.json.txt
@dineshr93 There's something really strange at this report. One of the lines mention kotlin-stdlib, which is not used at all as a direct dependency or used at all in SW360. Can you explain that one until we start to chase ghosts ?
@dineshr93 To answer properly, the only related dependency is http-support that usees ktling on third level after okhttp Please fix this list on direct dependencies. We can't simply fix all transient dependencies
@dineshr93 To answer properly, the only related dependency is http-support that usees ktling on third level after okhttp Please fix this list on direct dependencies. We can't simply fix all transient dependencies

The direct dependencies are marked in star-dotted lines with text "DIRECT" as shown in above screenshot Find the updated text file dependencies_Segregated_with_start_lines.txt
There are still more than you mentioned and most are repeated as well especially spdx tools and its dependencies.
exactly below are the direct dependencies that needs to be udpated
1. org.ektorp:org.ektorp:jar:1.5.0:compile
2. org.spdx:tools-java:jar:1.1.0:compile
2. org.spdx:tools-java:jar:1.1.0:test
3. org.springframework:spring-beans:jar:5.3.19:compile
4. org.springframework:spring-webmvc:jar:5.3.19:compile
5. org.springframework.boot:spring-boot-starter-web:jar:2.6.6:compile
6. org.springframework.security.oauth:spring-security-oauth2:jar:2.5.1.RELEASE:compile
7. org.springframework.security:spring-security-jwt:jar:1.1.1.RELEASE:compile
8. com.squareup.okhttp3:okhttp:jar:4.3.1:compile
9. com.github.tomakehurst:wiremock-jre8:jar:2.26.0:test
Description
I performed the vulnerability scan on sw360 via microsoft sbom and feeding the spdx to Google's osv scanner and we found 16 packages security vulnerabilities
The github security may not be flagging this becuase it may not be build aware (tracking direct and indirect dependencies via pom.xml files). I used micrsoft sbom to produce build aware sboms which pulls out indirect dependencies as well and from that these new vulnerabilities are flagged.
So my suggestion is we need to configure build aware tools -> like microsoft sboms and use googles osv in the CT pipeline. Let me know if you need help on this
How to reproduce
screenshot
vulnerablity list
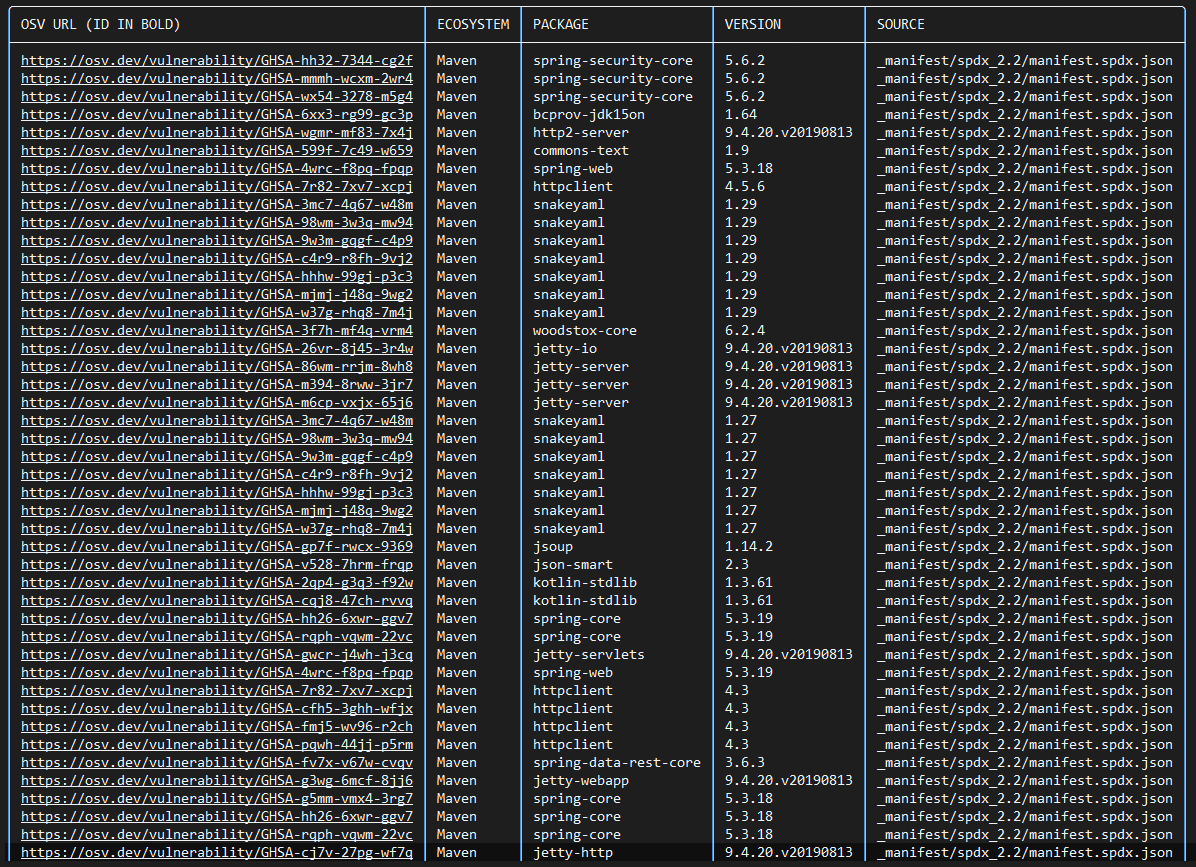vuln_resolution_list.json
File vuln_resolution_list.json
```js [ "bcprov-jdk15on", "1.64", [ "GHSA-6xx3-rg99-gc3p" ], [ { "introduced": "0" }, { "fixed": "1.0.2.1" }, { "introduced": "0" }, { "fixed": "1.66" }, { "introduced": "0" }, { "fixed": "1.66" }, { "introduced": "0" }, { "fixed": "1.66" }, { "introduced": "0" }, { "fixed": "1.66" }, { "introduced": "0" }, { "fixed": "1.66" }, { "introduced": "0" }, { "fixed": "1.66" }, { "introduced": "0" }, { "fixed": "1.66" } ] ] [ "snakeyaml", "1.27", [ "GHSA-3mc7-4q67-w48m", "GHSA-98wm-3w3q-mw94", "GHSA-9w3m-gqgf-c4p9", "GHSA-c4r9-r8fh-9vj2", "GHSA-hhhw-99gj-p3c3", "GHSA-mjmj-j48q-9wg2", "GHSA-w37g-rhq8-7m4j" ], [ { "introduced": "0" }, { "fixed": "1.31" }, { "introduced": "0" }, { "fixed": "1.31" }, { "introduced": "0" }, { "fixed": "1.32" }, { "introduced": "0" }, { "fixed": "1.31" }, { "introduced": "0" }, { "fixed": "1.31" }, { "introduced": "0" }, { "last_affected": "1.30" }, { "introduced": "0" }, { "fixed": "1.32" } ] ] [ "jetty-http", "9.4.20.v20190813", [ "GHSA-cj7v-27pg-wf7q" ], [ { "introduced": "0" }, { "fixed": "9.4.47" }, { "introduced": "10.0.0" }, { "fixed": "10.0.10" }, { "introduced": "11.0.0" }, { "fixed": "11.0.10" } ] ] [ "jetty-io", "9.4.20.v20190813", [ "GHSA-26vr-8j45-3r4w" ], [ { "introduced": "7.2.2" }, { "fixed": "9.4.39" }, { "introduced": "10.0.0" }, { "fixed": "10.0.2" }, { "introduced": "11.0.0" }, { "fixed": "11.0.2" } ] ] [ "jsoup", "1.14.2", [ "GHSA-gp7f-rwcx-9369" ], [ { "introduced": "0" }, { "fixed": "1.15.3" } ] ] [ "spring-core", "5.3.18", [ "GHSA-g5mm-vmx4-3rg7", "GHSA-hh26-6xwr-ggv7", "GHSA-rqph-vqwm-22vc" ], [ { "introduced": "5.3.0" }, { "fixed": "5.3.19" }, { "introduced": "0" }, { "fixed": "5.2.21" }, { "introduced": "0" }, { "fixed": "5.2.22.RELEASE" }, { "introduced": "5.3.0" }, { "fixed": "5.3.20" }, { "introduced": "5.3.0" }, { "fixed": "5.3.20" }, { "introduced": "0" }, { "fixed": "5.2.22.RELEASE" } ] ] [ "json-smart", "2.3", [ "GHSA-v528-7hrm-frqp" ], [ { "introduced": "0" }, { "fixed": "1.3.2" }, { "introduced": "2.4.0" }, { "fixed": "2.4.1" }, { "introduced": "0" }, { "fixed": "1.3.2" }, { "introduced": "2.0.0" }, { "fixed": "2.3.1" } ] ] [ "jetty-webapp", "9.4.20.v20190813", [ "GHSA-g3wg-6mcf-8jj6" ], [ { "introduced": "0" }, { "fixed": "9.4.33" }, { "introduced": "0" }, { "fixed": "9.4.33" }, { "introduced": "10.0.0.beta1" }, { "fixed": "10.0.0.beta3" }, { "introduced": "10.0.0.beta1" }, { "fixed": "10.0.0.beta3" }, { "introduced": "11.0.0.beta1" }, { "fixed": "11.0.0.beta3" }, { "introduced": "11.0.0.beta1" }, { "fixed": "11.0.0.beta3" } ] ] [ "http2-server", "9.4.20.v20190813", [ "GHSA-wgmr-mf83-7x4j" ], [ { "introduced": "0" }, { "fixed": "9.4.47" }, { "introduced": "10.0.0" }, { "fixed": "10.0.10" }, { "introduced": "11.0.0" }, { "fixed": "11.0.10" } ] ] [ "spring-web", "5.3.18", [ "GHSA-4wrc-f8pq-fpqp" ], [ { "introduced": "0" }, { "fixed": "6.0.0" } ] ] [ "jetty-server", "9.4.20.v20190813", [ "GHSA-86wm-rrjm-8wh8", "GHSA-m394-8rww-3jr7", "GHSA-m6cp-vxjx-65j6" ], [ { "introduced": "9.4.0" }, { "fixed": "9.4.35.v20201120" }, { "introduced": "9.4.6" }, { "fixed": "9.4.37" }, { "introduced": "10.0.0" }, { "fixed": "10.0.1" }, { "introduced": "11.0.0" }, { "fixed": "11.0.1" }, { "introduced": "0" }, { "fixed": "9.4.41" }, { "introduced": "10.0.0" }, { "fixed": "10.0.3" }, { "introduced": "11.0.0" }, { "fixed": "11.0.3" } ] ] [ "httpclient", "4.5.6", [ "GHSA-7r82-7xv7-xcpj" ], [ { "introduced": "0" }, { "fixed": "4.5.13" }, { "introduced": "5.0.0" }, { "fixed": "5.0.3" } ] ] [ "commons-text", "1.9", [ "GHSA-599f-7c49-w659" ], [ { "introduced": "1.5" }, { "fixed": "1.10.0" } ] ] [ "kotlin-stdlib", "1.3.61", [ "GHSA-2qp4-g3q3-f92w", "GHSA-cqj8-47ch-rvvq" ], [ { "introduced": "0" }, { "fixed": "1.6.0" }, { "introduced": "0" }, { "fixed": "1.4.21" } ] ] [ "httpclient", "4.3", [ "GHSA-7r82-7xv7-xcpj", "GHSA-cfh5-3ghh-wfjx", "GHSA-fmj5-wv96-r2ch", "GHSA-pqwh-44jj-p5rm" ], [ { "introduced": "0" }, { "fixed": "4.5.13" }, { "introduced": "5.0.0" }, { "fixed": "5.0.3" }, { "introduced": "0" }, { "fixed": "4.3.5" }, { "introduced": "0" }, { "fixed": "4.3.6" }, { "introduced": "4.3" }, { "fixed": "4.3.1" } ] ] [ "spring-data-rest-core", "3.6.3", [ "GHSA-fv7x-v67w-cvqv" ], [ { "introduced": "3.6.0" }, { "fixed": "3.6.7" }, { "introduced": "3.7.0" }, { "fixed": "3.7.3" } ] ] [ "snakeyaml", "1.29", [ "GHSA-3mc7-4q67-w48m", "GHSA-98wm-3w3q-mw94", "GHSA-9w3m-gqgf-c4p9", "GHSA-c4r9-r8fh-9vj2", "GHSA-hhhw-99gj-p3c3", "GHSA-mjmj-j48q-9wg2", "GHSA-w37g-rhq8-7m4j" ], [ { "introduced": "0" }, { "fixed": "1.31" }, { "introduced": "0" }, { "fixed": "1.31" }, { "introduced": "0" }, { "fixed": "1.32" }, { "introduced": "0" }, { "fixed": "1.31" }, { "introduced": "0" }, { "fixed": "1.31" }, { "introduced": "0" }, { "last_affected": "1.30" }, { "introduced": "0" }, { "fixed": "1.32" } ] ] [ "woodstox-core", "6.2.4", [ "GHSA-3f7h-mf4q-vrm4" ], [ { "introduced": "6.0.0" }, { "fixed": "6.4.0" }, { "introduced": "0" }, { "fixed": "5.4.0" } ] ] [ "spring-core", "5.3.19", [ "GHSA-hh26-6xwr-ggv7", "GHSA-rqph-vqwm-22vc" ], [ { "introduced": "0" }, { "fixed": "5.2.22.RELEASE" }, { "introduced": "5.3.0" }, { "fixed": "5.3.20" }, { "introduced": "5.3.0" }, { "fixed": "5.3.20" }, { "introduced": "0" }, { "fixed": "5.2.22.RELEASE" } ] ] [ "spring-security-core", "5.6.2", [ "GHSA-hh32-7344-cg2f", "GHSA-mmmh-wcxm-2wr4", "GHSA-wx54-3278-m5g4" ], [ { "introduced": "0" }, { "fixed": "5.5.7" }, { "introduced": "5.6.0" }, { "fixed": "5.6.4" }, { "introduced": "5.7.0" }, { "fixed": "5.7.5" }, { "introduced": "5.6.0" }, { "fixed": "5.6.9" }, { "introduced": "0" }, { "fixed": "5.5.7" }, { "introduced": "5.6.0" }, { "fixed": "5.6.4" } ] ] [ "spring-web", "5.3.19", [ "GHSA-4wrc-f8pq-fpqp" ], [ { "introduced": "0" }, { "fixed": "6.0.0" } ] ] [ "jetty-servlets", "9.4.20.v20190813", [ "GHSA-gwcr-j4wh-j3cq" ], [ { "introduced": "0" }, { "fixed": "9.4.41" }, { "introduced": "10.0.0" }, { "fixed": "10.0.3" }, { "introduced": "11.0.0" }, { "fixed": "11.0.3" } ] ] ```Versions