Please refer to the more detailed logs below: I (733475) MQTT: ########## ########### ########### I (733515) mbedtls: ssl_tls.c:3919 => handshake
I (733515) mbedtls: ssl_msg.c:2358 => flush output
I (733515) mbedtls: ssl_msg.c:2367 <= flush output
I (733525) mbedtls: ssl_tls.c:3838 client state: MBEDTLS_SSL_HELLO_REQUEST
I (733525) mbedtls: ssl_msg.c:2358 => flush output
I (733535) mbedtls: ssl_msg.c:2367 <= flush output
I (733535) mbedtls: ssl_tls.c:3838 client state: MBEDTLS_SSL_CLIENT_HELLO
I (733545) mbedtls: ssl_client.c:924 => write client hello
I (733555) mbedtls: ssl_msg.c:2788 => write handshake message
I (733565) mbedtls: ssl_msg.c:2948 => write record
I (733565) mbedtls: ssl_msg.c:3085 <= write record
I (733575) mbedtls: ssl_msg.c:2909 <= write handshake message
I (733575) mbedtls: ssl_client.c:1012 <= write client hello
I (733585) mbedtls: ssl_msg.c:2358 => flush output
I (733585) mbedtls: ssl_msg.c:2372 message length: 141, out_left: 141
I (733595) mbedtls: ssl_msg.c:2379 ssl->f_send() returned 141 (-0xffffff73)
I (733605) mbedtls: ssl_msg.c:2406 <= flush output
I (733615) mbedtls: ssl_tls.c:3838 client state: MBEDTLS_SSL_SERVER_HELLO
I (733615) mbedtls: ssl_tls12_client.c:1193 => parse server hello
I (733625) mbedtls: ssl_msg.c:4122 => read record
I (733635) mbedtls: ssl_msg.c:2160 => fetch input
I (733635) mbedtls: ssl_msg.c:2300 in_left: 0, nb_want: 5
I (733645) mbedtls: ssl_msg.c:2320 in_left: 0, nb_want: 5
I (733645) mbedtls: ssl_msg.c:2323 ssl->f_recv(_timeout)() returned 5 (-0xfffffffb)
I (733655) mbedtls: ssl_msg.c:2345 <= fetch input
I (733665) mbedtls: ssl_msg.c:2160 => fetch input
I (733665) mbedtls: ssl_msg.c:2300 in_left: 5, nb_want: 7
I (733675) mbedtls: ssl_msg.c:2320 in_left: 5, nb_want: 7
I (733685) mbedtls: ssl_msg.c:2323 ssl->f_recv(_timeout)() returned 2 (-0xfffffffe)
I (733685) mbedtls: ssl_msg.c:2345 <= fetch input
I (733695) mbedtls: ssl_msg.c:5027 got an alert message, type: [2:40]
W (733705) mbedtls: ssl_msg.c:5034 is a fatal alert message (msg 40)
W (733705) mbedtls: ssl_msg.c:4177 mbedtls_ssl_handle_message_type() returned -30592 (-0x7780)
W (733715) mbedtls: ssl_tls12_client.c:1197 mbedtls_ssl_read_record() returned -30592 (-0x7780)
I (733725) mbedtls: ssl_tls.c:3930 <= handshake
E (733735) esp-tls-mbedtls: mbedtls_ssl_handshake returned -0x7780 I (733745) esp-tls-mbedtls: Certificate verified. E (733745) esp-tls: Failed to open new connection E (733755) transport_base: Failed to open a new connection E (733765) HTTP_CLIENT: Connection failed, sock < 0 I (733765) MQTT: HTTP_EVENT_ERROR E (733765) MQTT: HTTP POST request failed: ESP_ERR_HTTP_CONNECT I (733775) MQTT: Last esp error code: 0x801a I (733775) MQTT: Last mbedtls failure: 0x7780 No response from server after POST request!
Answers checklist.
General issue report
Hi, the https post request is refusing the connection with the above error code. This function worked perfectly well before, but after adding some mqtt bits (no relation to http), the connection is refused with the error code shown in the image.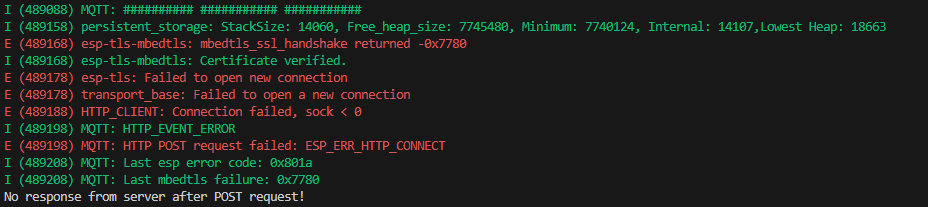 As you can see, the certificate is verified, yet the connection is refused. Please advise on this matter.
As you can see, the certificate is verified, yet the connection is refused. Please advise on this matter.