This should be expected, otherwise the client can pass any untrusted content.
In your scenario, you can test whether the issue can be resolved by using requestHeaders.set.x-forwarded-proto = "https".
Closed panta82 closed 4 weeks ago
This should be expected, otherwise the client can pass any untrusted content.
In your scenario, you can test whether the issue can be resolved by using requestHeaders.set.x-forwarded-proto = "https".
Understood. I can certainly hack it in.
It might be useful though for frps to have some kind of "behind proxy" mode, where this header is trusted. Because I assume this will be a 99% use case for the tool.
(also, should x-real-ip then be passed through?)
More about the configuration of the 7th layer HTTP will be planned for the future v2 version, and currently, no additional configuration options will be provided.
x-real-ip is not a standard header defined by the RFC. The current code uses the native handling logic of Go and does not perform any additional processing.
Ok, that's fair. Closing the issue.
Bug Description
I'm using setup:
nginx[443] (SSL termination) -> proxy_pass[http] -> frps[http] -> ...tunnel... -> frpc[http] -> local service[http]This works, however on the other side,
X-Forwarded-Protoheader gets changed, which creates problems for cookies (the app thinks it's not behind HTTPS, which is incorrect).Here's the diff: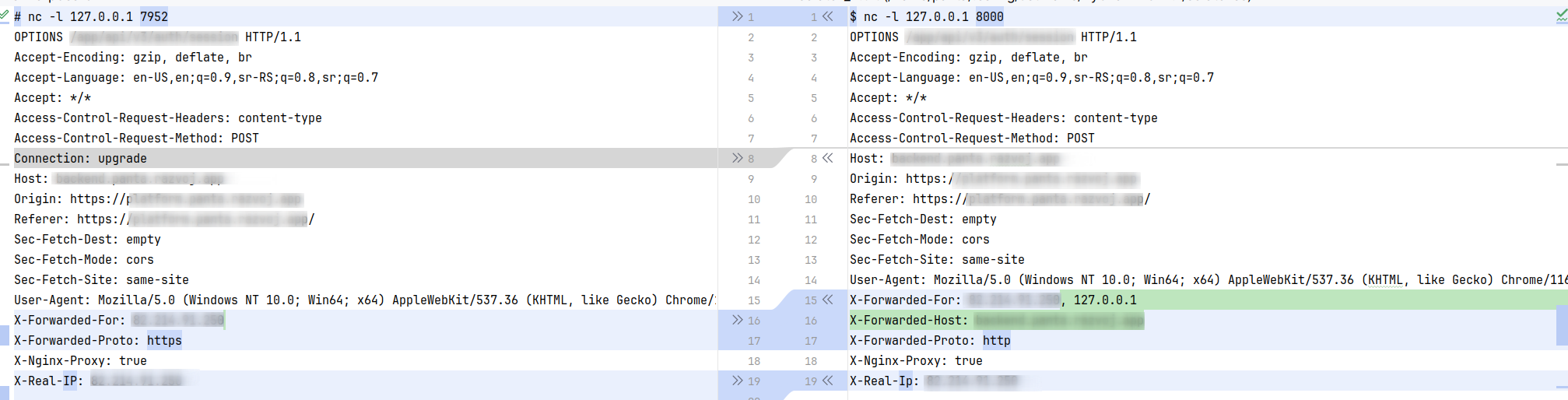
Left side: What is sent from nginx to frps Right side: What is sent from frpc to the client
Frps adds
X-Forwarded-Host(good), but changesX-Forwarded-Protofromhttpstohttp.frpc Version
0.57.0
frps Version
0.57.0
System Architecture
linux/amd64
Configurations
frps.toml:
frpc.toml:
client.example.com.conf (nginx):
Logs
No response
Steps to reproduce
???
Affected area