Hmm - there are some notes in the accompanying blog posts - eg in steps 5 to 8. Maybe post back with details, screenshots etc and I'll see if you error makes any sense to me.
Closed yolepro closed 4 months ago
Hmm - there are some notes in the accompanying blog posts - eg in steps 5 to 8. Maybe post back with details, screenshots etc and I'll see if you error makes any sense to me.
Meant to say: my example is intentionally a little complex. If you want to get integrated with AppAuth libraries then this example that we produced at Curity might be easier to use. Eg you can more easily re-point it to your own authorization server:
Thank you for your feedback, I will have a look on your 2nd exemple. Nevertheless, I did the spa exemple which is working properly with the user credential you provide (guestuser@example.com), but the iOS example is not and I don't really understand why since I don't know exactly how your Authorization Server is configured. You give a link in your Blog on a Cloud Authorization Server Setup Article, but it is unfortunately not refering the appropriate article.
It is a little difficult for me to understand your problem since the only info I have is that you received an Access Denied message. Could you maybe post a screenshot of it, so that I can see whether it is an application error, a deep linking error or an authorization server error?
Also. are you running on a simulator or real device? On a real device you will get failures since deep linking registration will fail due to the way Apple device registration and code signing works. So run on a simulator.
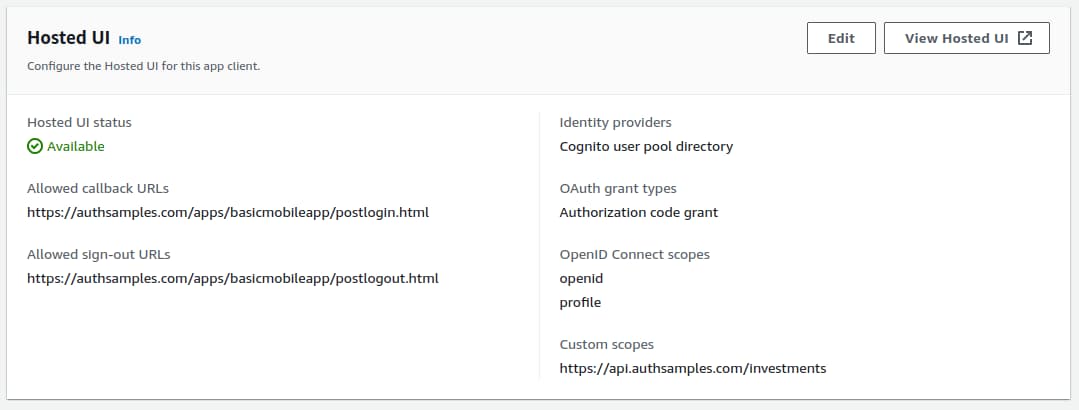
In terms of the OAuth client settings in the authorization server, they look like this and the client ID is 2vshs4gidsbpnjmsprhh607ege. I did some renaming recently so some images are currently a little incorrect and it will take me a little while to update them.
The unusual thing about this example is that redirect URIs return to an interstitial web page, which is an annoyance. When using claimed HTTP schemes you have to do so to receive the login response. Although it is the most secure option, browsers don't support invoking deep links automatically, in a redirect response.
The base URL for the authorization server is https://login.authsamples.com but Cognito is quite poor in some areas. Eg some OAuth endpoints have to use the AWS generated base URL. Here are a few other links that might help you to understand the setup, but if I could see a screenshot I might have a better idea of your problem:
Finally, make sure you read the iOS code sample blog posts. Lots of stuff is explained there.
Thank you again for detailed answer. First I tried the Curity example and they are working quite well (the HAAPI is working great and I would like to have such features with a standard Keycloak but seems to not exist currently). Concerning my problem on this project, it really seems to be on the IDP server side, since the Access Denied is on the Browser page. I go on the IDP login page, enter the user password (either guestuser@example.com or guestadmin@example.com). The user login is accepted and when I click Return to the app I got the Access Denied (here is a capture):
Since it's on the server side, I don't have any log on iOS side (but perhaps I miss something?).
Ah - what is happening there is that associated domain registration has failed on your simulator. When this JavaScript code executes, the deep link is not invoked. Instead, the following URL runs in the browser - you get the same response if you go here in a desktop browser:
https://mobile.authsamples.com/basicmobileapp/oauth/callback
This domain only exists online to host deep linking asset files. It is a small CloudFront distribution, where CloudFront presents an access denied default error when non-existent resources are requested.
To fix your problem, I think you may need to activate Automatically Manage Signing in Xcode. Associated domain registration will hopefully then succeed. I have run the code sample like this on a simulator on a completely new computer in the past, when signed into a different Apple account to my own, so I think it works alright.
Another thing you might try is loading the provisioning profile from the root tolder into Xcode.
I wrote some other notes on failures in this blog post, though how this works. Unfortunately, Apple do not make this stuff easy for us developers.
@yolepro were you able to resolve this issue? I have encountered the same problem.
Hello @wb7212 unfortunately not. But from @gary-archer advice I went on the Curity code example which is working perfectly for me so I could use it as an example for my use cases.
I made a change then, to enable a working app, by switching to a private use URI scheme. To do so, get the latest code and then follow these instructions.
@gary-archer Thanks, I was able to get it to work. @yolepro How did you implement the Curity code example? I am trying to SSO from Mobile App to Web.
SSO is based on cookies issued by identity systems. You should not usually need to write custom code.
ANDROID
If you log into my mobile app on an Android device, then open Chrome and browse to https://www.authsamples.com you will see an SSO event.
iOS
If you log into my mobile app on an iOS device, then open Safari and browse to https://www.authsamples.com you may see an SSO event.
MAINSTREAM BEHAVIOUR
When they do not have a token yet, apps can either redirect automatically or present a login button to the user, to keep them informed. Mine do the latter. SSO occurs when the identity systems do not provide a prompt on the second redirect.
ADVANCED BEHAVIOR
There are some nuances, which are described in the Nonce Authenticator Pattern article. By default though, use the mainstream behaviour.
Out of interest, I did a bit more digging around on your failures, since I am interested in developer setups.\ I added a way to get claimed HTTPS schemes working using a development web server.
I start the application without any change and it's loading correctly, but I have an Access Denied message when I am using the login / password given in the readme file. It seems to be a configuration problem on the Authorization Server side even if I have the login page showing I am correctly connected. Could we have more information on the way you configured your Authorization Server (Root URL, Valid redirect URIs,...) to get such app working?
Thanks