The pre-release does not have the email option, but the full release, planned for later this month, will. I've reopened #740 - it was mistakenly closed.
The coding will attempt to email the reset password. If the server that hosts the installation does not support php mail(), the email will not be sent. However, messaging will say something to the effect of "A new password has been generated and emailed to the address you have on file. If you do not receive an email with your new password, contact a competition official."
The password will not be displayed on screen at any point.
Again, in the future, a token system is planned to be put into place.
Edit: version 2.1.10 will utilize a token system for password reset. Additionally, password strength will be checked using Dropbox's zxcvbn password strength estimator in conjunction with the jQuery Password Strength Meter for Twitter Bootstrap plugin.
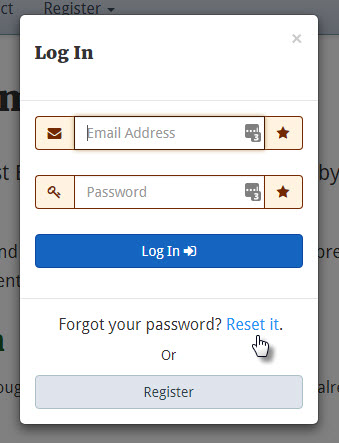

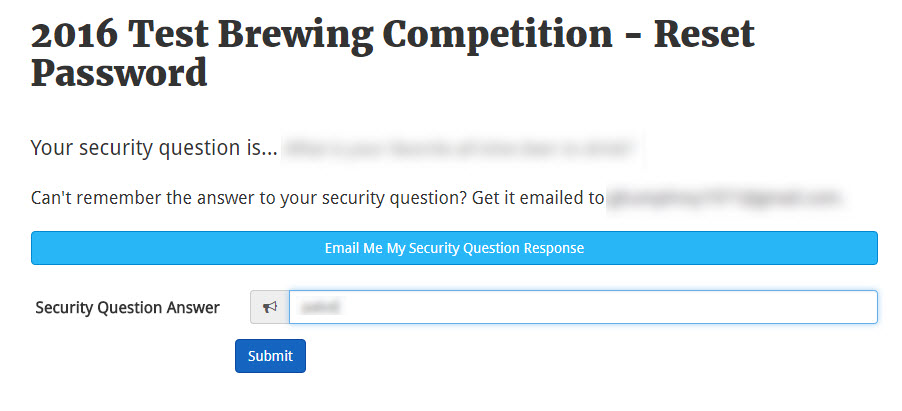
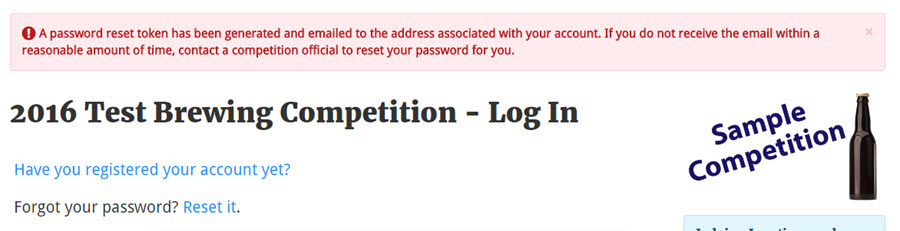





A significant vulnerability in the authentication system of BCOE&M was reported in #740
@geoffhumphrey and I emailed when it was reported and came up with what sounded like a good solution to the problem which involved
I indicated "I think this would be a good interim tradeoff as it protects the installations and the users and introduces pain for folks hosting it on systems that can't send email. I think that would be a good security/convenience trade off."
He agreed that he'd put the change in for "the next release. Based upon the current codebase, it will be a pretty easy fix."
A few weeks back @geoffhumphrey indicated that instead the release would have "22 newer and "stronger" questions".
Increasing the number of security questions does little to mitigate this risk as it doesn't prevent users from choosing weaker security questions with brute forceable answers. In any normal website, having a weak security question (e.g. What is your high school mascot?) is not a big deal because the attacker must gain control of the victims email account in addition to guessing the answer to their security question. The security vulnerability originally reported in #740 however calls out that BCOE&M works fundamentally differently and does not enjoy this added protection.
Please complete and release either version 2.1.10 or a security point release in advance of 2.1.10 in the next 30 days (before August 17, 2017) with the proposed change of emailing users their newly reset password (in addition to or instead of an increased number of security questions) so that it's no longer possible for a users new password to be displayed on the site. If this doesn't happen I have an obligation in the interest of responsible disclosure to publish this vulnerability in order to protect the users of BCOE&M.