@omarmarquez Can you mention which authorization plugin you're using? Also, any steps to reproduce this or relevant screenshots might help [I understand you're saying nothing is happening when you click it, and so screenshots of that might not be useful].
I tried it with the built-in file-based password plugin and it worked fine. As mentioned in the release notes for 19.2, Google OAuth plugin does not support access tokens.
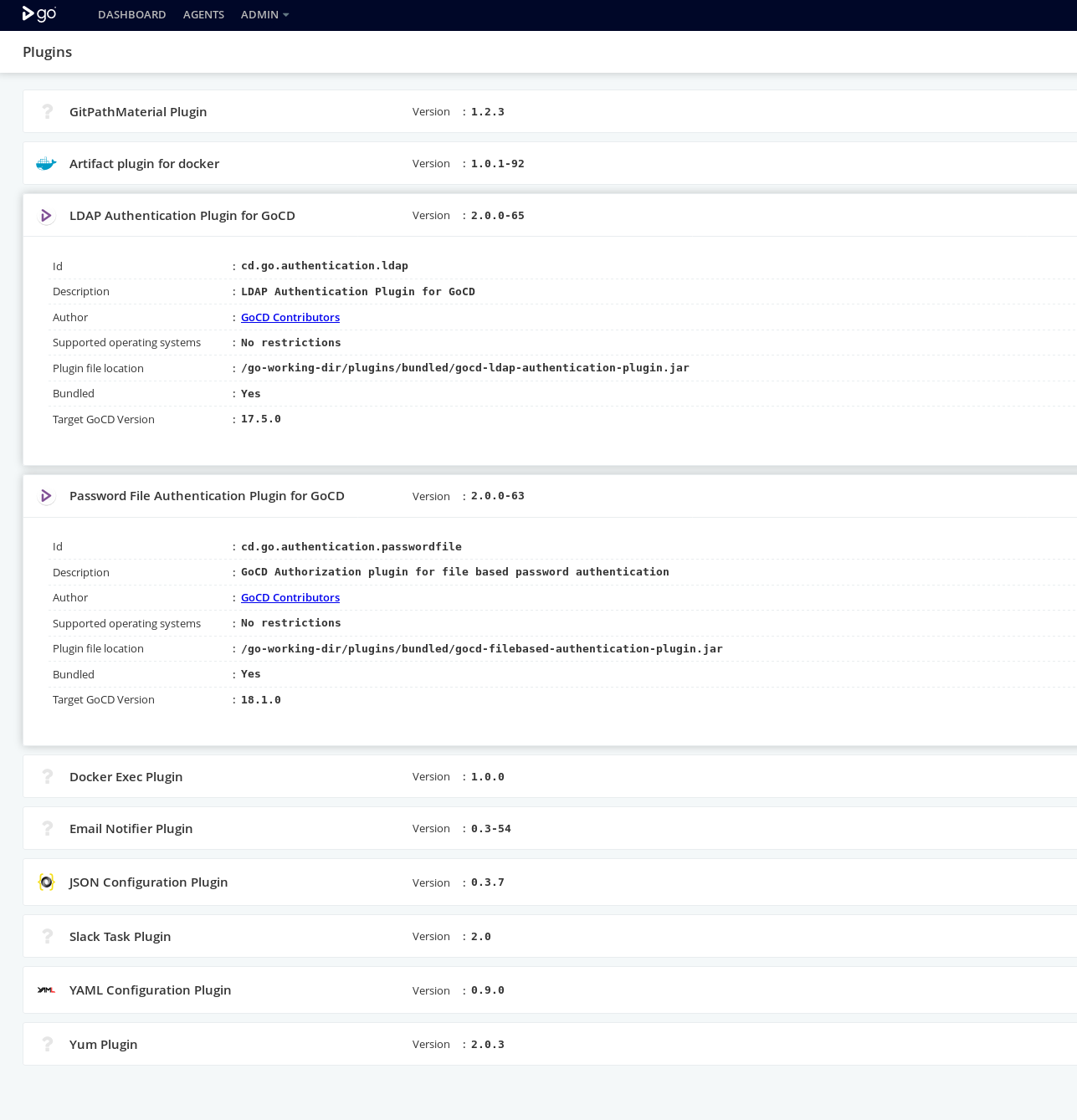
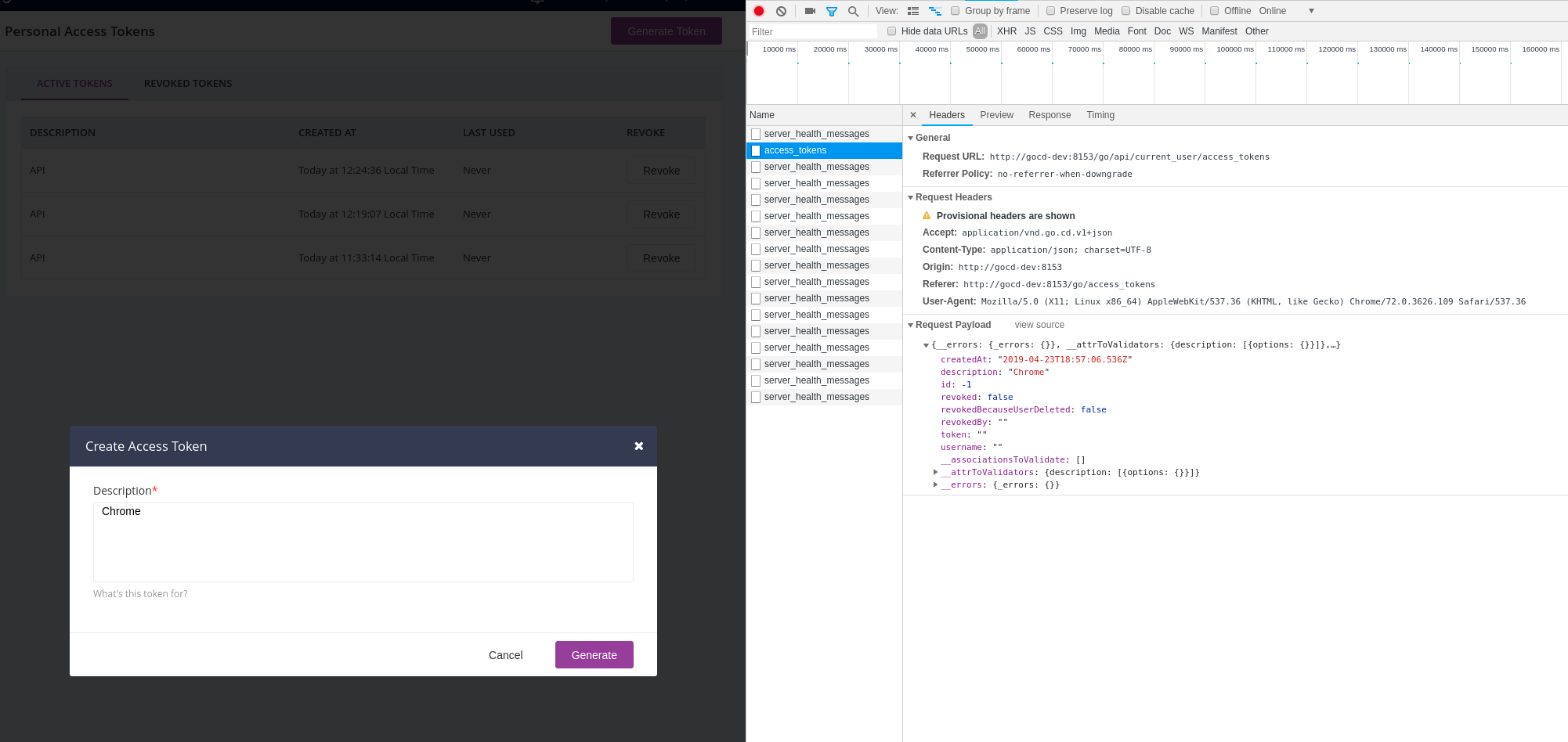






When clicking on the [Generate] button nothing happens, the page stays the same, the javascript console shows no activity associated with the click action...