Complete repro -
package main
import (
"fmt"
"net/http"
)
func main() {
http.HandleFunc("/foo", func(w http.ResponseWriter, req *http.Request) {
err := req.ParseForm()
if err != nil {
fmt.Println(err)
w.Write([]byte("error"))
return
}
params := req.Form
fmt.Println("params:", params, "count:", len(params))
for key, values := range params {
fmt.Println("param", key, ":", values)
}
w.Write([]byte("OK"))
})
fmt.Println("starting on port 9999")
server := &http.Server{
Addr: ":9999",
}
server.ListenAndServe()
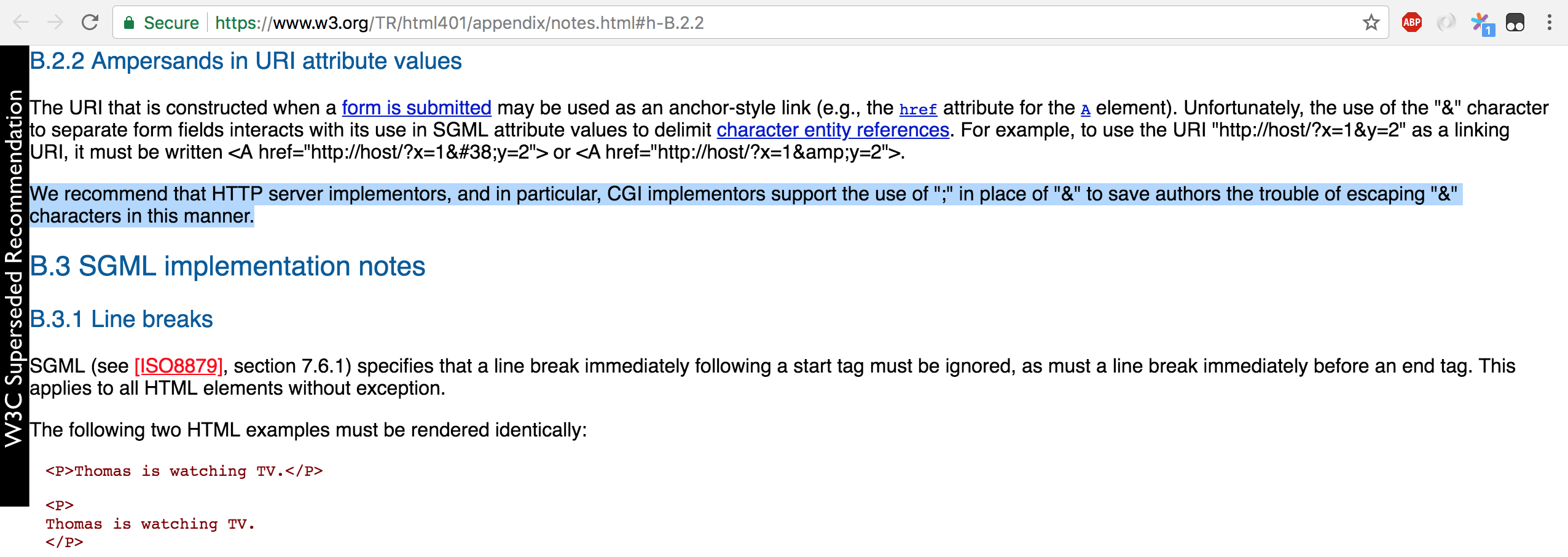
}curl 'http://localhost:9999/foo?id=1%27;--'
@bradfitz - Is this expected ?

Please answer these questions before submitting your issue. Thanks!
What version of Go are you using (
go version)?go1.10.1 linux/amd64
Does this issue reproduce with the latest release?
Yes
What operating system and processor architecture are you using (
go env)?CentOS 7 with kernel 3.10.0-514.10.2.el7.x86_64
What did you do?
I create a program to detect attack such as SQL Injection, when test case is: http://..../testcase?id=1%27;--
and I use: r.ParseForm() params := r.Form fmt.Println("params:", params, "count:", len(params)) for key, values := range params { fmt.Println("param", key, ":", values) }
Got: params: map[--:[] id:[1']] count: 2 param id : [1'] param -- : []
What did you expect to see?
expect only one expression in this case: key: id value: 1';--
What did you see instead?
I got two key:[value] pairs.