I have narrowed this down to the fact that the container stack does not respond to arp requests. ARP seems to be disabled on the IPVLAN interface in the container. This cannot be an issue with the IPVLAN kernel driver as it works correctly in the name space example I posted. There is something with docker and IPVLAN that is not setup correctly.
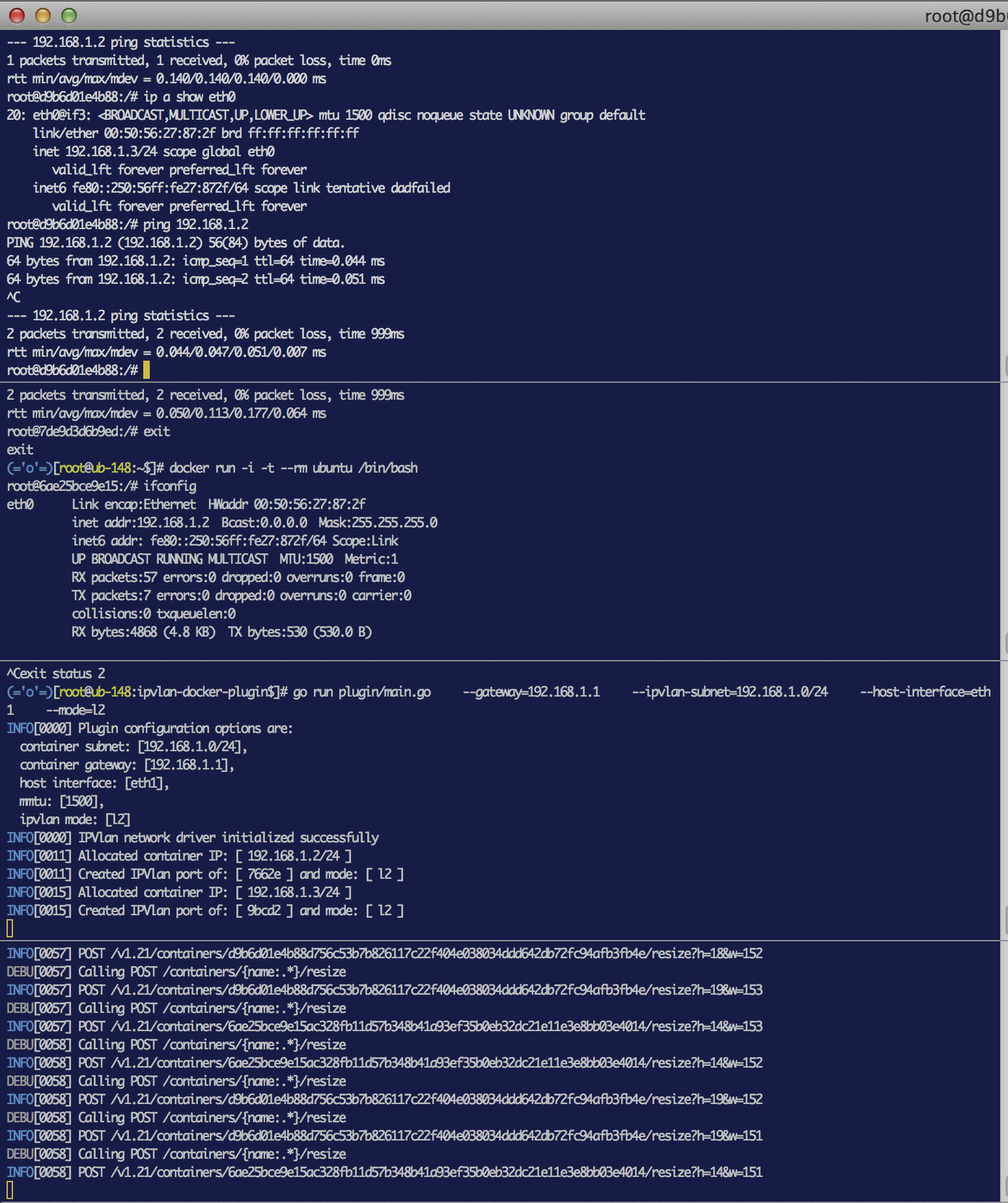
I have experimental docker (Version : 1.9.0-dev) installed and I deployed ip-vlan-docker-plugin driver on my host after building it myself.
I start my driver as follows
./main --gateway=172.200.0.1 --ipvlan-subnet=172.200.0.0/22 --host-interface=em1 --mode=l2
it starts up fine. Then I launch 2 containers on this host both running busybox. It starts up fine and gets IP addresses assigned and I can see the routes are added to the route table in the container. I am pasting the output of "route -n" below from one of the containers. Both look same.
route -n
Kernel IP routing table Destination Gateway Genmask Flags Metric Ref Use Iface 0.0.0.0 172.200.0.1 0.0.0.0 UG 0 0 0 eth0 172.200.0.0 0.0.0.0 255.255.252.0 U 0 0 0 eth0
What I am finding is that I am unable to ping one container from the other container on the same host. However if I start another container on a remote host in another subnet, I am able to reach it without any issues. I know from a container I cannot reach host interface. However I expected that containers within the same host should be able to communicate with each other.
I decided to test this outside the docker ecosystem as follows
// create first name space and provision it
ip netns add ns0 ip link add link em1 ipvl0 type ipvlan mode l2 ip link set dev ipvl0 netns ns0 ip netns exec ns0 bash ip link set dev ipvl0 up ip -4 addr add 172.200.0.24/22 dev ipvl0 ip -4 route add default via 172.200.0.1 dev ipvl0
root@ubuntu:~# route -n Kernel IP routing table Destination Gateway Genmask Flags Metric Ref Use Iface 0.0.0.0 172.200.0.1 0.0.0.0 UG 0 0 0 ipvl0 172.200.0.0 0.0.0.0 255.255.252.0 U 0 0 0 ipvl0
// create a second name space ip netns add ns1 ip link add link em1 ipvl1 type ipvlan mode l2 ip link set dev ipvl1 netns ns1 ip netns exec ns1 bash ip link set dev ipvl1 up ip -4 addr add 172.200.0.35/22 dev ipvl1 ip -4 route add default via 172.200.0.1 dev ipvl1
Both these namespaces are on the same host and I have no problem pinging the interfaces in each of these namespaces from the bash shell in the other namespace.
Problem seems to be with only the docker container. Has anybody else experienced similar problems?