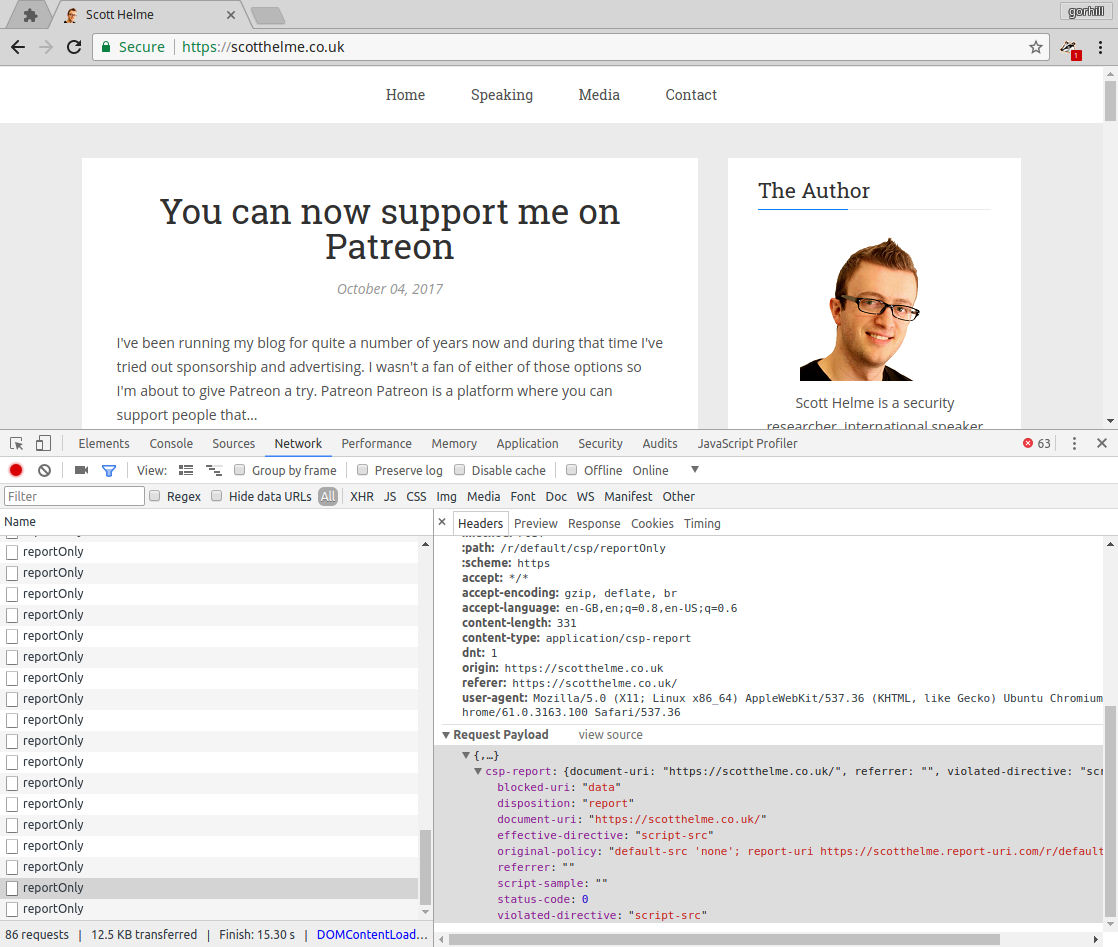
By design. uBO will block CSP reports if it injects at least one neutered script in a page. This is what is happening on https://scotthelme.co.uk/, uBO is injecting a neutered Google Analytics script. In such case, uBO conservately assumes that the injected script is what is causing the CSP reports and blocks them. If you create an allow rule for Google Analytics for that site, the CSP reports are not blocked.

Describe the issue
uBO is blocking the sending of legitimate CSP reports.
One or more specific URLs where the issue occurs
I have a policy setup on https://scotthelme.co.uk which fires multiple reports that are all blocked.
Screenshot in which the issue can be seen
Steps for anyone to reproduce the issue
Visit https://scotthelme.co.uk which attempts to send multiple CSP reports to a reporting endpoint, check the console/network tabs in dev tools.
Your settings
Your filter lists
Default settings.
Your custom filters (if any)
None.