Unable to reproduce. Your report lacks information and detailed step-to-reproduce, so I went with my own steps:
- Using Linux, Firefox Nightly, uMatrix 1.0.0.
- Added
Mozilla/5.0 (Windows NT 6.1; rv:45.0) Gecko/20100101 Firefox/45.0to the list of user agent strings in the Privacy panel, commented out all other strings. - Set
dom.storage.enabledtofalseinabout:config. - Opened
https://mega.nz/in a new tab. - Ensured that the switch "User agent spoofing" is enabled for that site.
Result, the site thinks I am using Firefox 45 on Windows:

I will reopen if you make a better case that there is an issue. You failed to:
- provide OS/Browser/uMatrix version
- provide which user agent strings you are using for spoofing
- provide assurance that you actually verified that spoofing is enabled
- provide other information as to whether other extensions/browser settings may be interfering
- provide detailed steps to reproduce
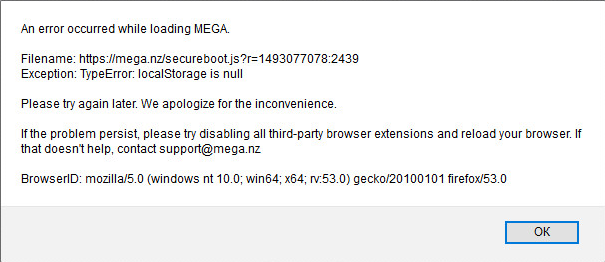
Just accidentally discovered the leak a real user-agent for which spoofing is responsible uMatrix.
In order to reproduce the leak it is necessary:
1: Go to https://mega.nz 2: Open about:config in new tab and change dom.storage.enabled to false 3: Go back to the tab with https://mega.nz and you will see a window with an error and your real user-agent.