It looks like it is considered a feature by STC that this isn't supported. If there is no (official) way to read back the memory in the bootloader, that's the best readout protection. Some Chinese developers are quite paranoid, apparently. :)
Why do you need this for your project? You can add code to read out the data yourself. It's not very convenient, but not hard to do either.
I'll still leave this open if I can manage to find out a way.
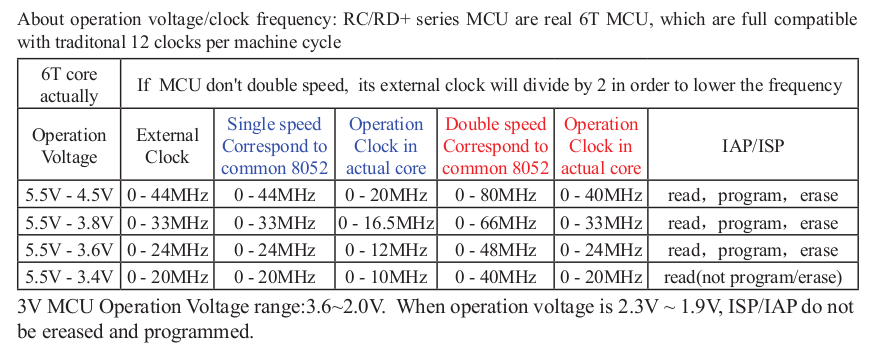
Hi! It seems like currently there is no way to read flash from the device (this feature is not available even in their own tool).
However, I really need this feature for one of the projects I'm working on.
Perhaps there is a way to implement it? E.g. maybe the verify sequence can be abused to get the data?