@xmow49 jffs2 is a file system, and the extracted contents are likely correct. Since it didn't extract anything else, chances are you're dealing with a non-linux firmware (i.e. RTOS) where the OS+main application are combined into a single 'chunk' of memory that is loaded/executed. If you know the load address you may be able to use ghidra to decompile the code and see what functions are available in the code and perhaps enable some of it but you'll need to flash the changes back for any attempts and your options will be very limited. If the device was running linux, binwalk should have extracted boot scripts and the main application for the device. It is also possible for the main chunk to be compressed with some custom tool which would make it very difficult to make changes to it.
It is highly unlikely that anything you place/change in the jffs2 will make any difference in behavior of the device (perhaps the two sounds, but that's it).
Hi, First thanks for your work in this repo. It's very helpful. I have an IP camera that works on the Cloudege app too. I followed your readme, and I successfully read the flash of the camera: firm.bin I tested binwalk:
But he found only one jffs2 partition that contains cameras sound (parring) :
I used https://binvis.io/ to see the bin: So, there is a partition at 0x70000. With an hex dump, i can see:
So, there is a partition at 0x70000. With an hex dump, i can see: 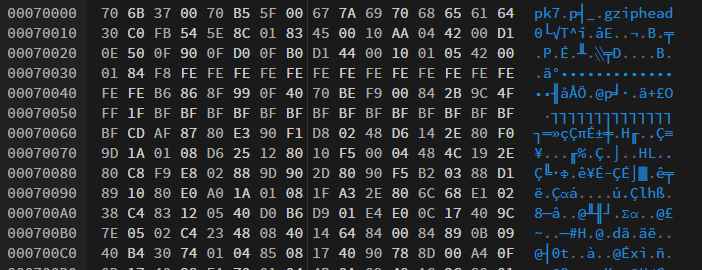
gzipheadSo I tested to create a .bin file with only this partition, and dezip:
But no result. Now I am stuck with this. Do you have any idea of what is this partition, and how to decode it?
Thanks for your time.