I think it's useful, but the draft version is obsolete. As of 1.1.0, chacha20 supports the rfc version, not the draft version.
1.0.2 and 1.1.1 have a lot of differences, which makes it difficult to patch.
I will try, but I do not know if it is possible.
P.S. Google(google.com, etc.) has already removed OLD CHACHA from SSL Cipher.
Sorry my poor english.
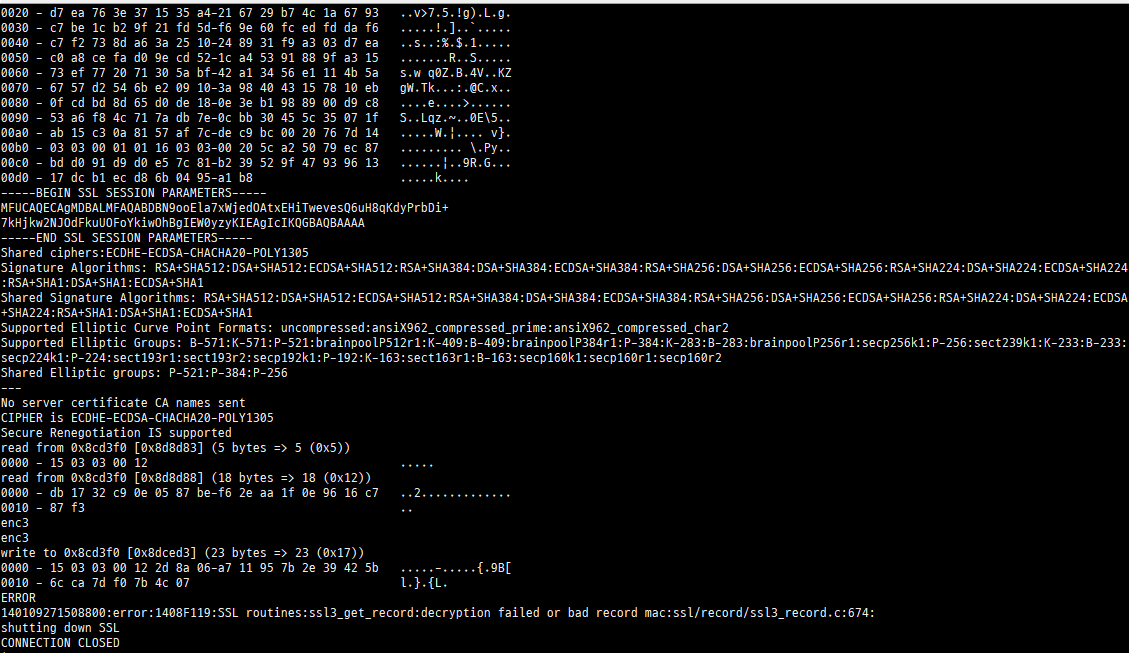
The Cloudflare patch can enable Both CHACHA20-RFC(0xcca8-0xccaa) ciphers and CHACH20-Draft(0xcc13-0xcc15) ciphers in Openssl 1.0.2f-j I tried to make the Cloudflare patch compatible with Openssl-1.1.1-pre9 by myself, by adding the CHACHA-Draft back to it, but I met a lot of difficulties and caused many errors. Can you please make such a patch that enable both the RFC and Draft CHACHA20 ciphers in Openssl 1.1.0 I think it would be very useful for everyone