That sounds useful! It's flexible enough that we could probably add that in, yes.
Nothing in the current build touches the FL1 files, so I think it would end up being a second build output.
Do you have a sample set of FL1 changes? I could look and see if anything suggests itself
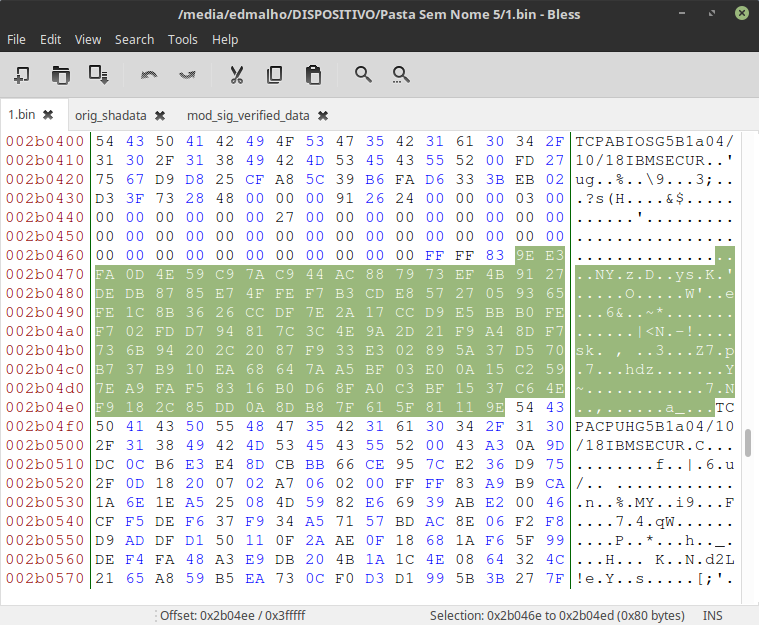
 In TCPABIOS we find a list of sha1 hashs of every file inside the 1st(?) volume called EfiFirmwareFileSystemGuid(and with a GUID 7A9354D9-0468-444A-81CE-0BF617D890DF).
In my case i have only one, FvMainCompact:
In TCPABIOS we find a list of sha1 hashs of every file inside the 1st(?) volume called EfiFirmwareFileSystemGuid(and with a GUID 7A9354D9-0468-444A-81CE-0BF617D890DF).
In my case i have only one, FvMainCompact:
 after IBMSECUR the entries starts in hex like this: 00 FD 27 (20 Bytes hash) (16 bytes header), 01 FD 27 (20 Bytes hash) (16 bytes header), 03 FD 27 (20 Bytes hash) (16 bytes header)... and so on.
after IBMSECUR the entries starts in hex like this: 00 FD 27 (20 Bytes hash) (16 bytes header), 01 FD 27 (20 Bytes hash) (16 bytes header), 03 FD 27 (20 Bytes hash) (16 bytes header)... and so on.
 the first byte increases by 1 for every hash/file
FD identifies the type file?
27 identifies the start of the hash
The header:
the 1st 4 bytes is the offset of the file (the bytes order is inverted)
after that is the size of the file, 6 bytes (also inverted)
them comes 03 00 00 00 00 00 (I didn't found what this is...)
The list terminates with 00 00 27 and 36 bytes of 00's
After all the mods, correct the hashs, sizes and offsets of the files that were changed
the first byte increases by 1 for every hash/file
FD identifies the type file?
27 identifies the start of the hash
The header:
the 1st 4 bytes is the offset of the file (the bytes order is inverted)
after that is the size of the file, 6 bytes (also inverted)
them comes 03 00 00 00 00 00 (I didn't found what this is...)
The list terminates with 00 00 27 and 36 bytes of 00's
After all the mods, correct the hashs, sizes and offsets of the files that were changed

 Run:
Run:

Can this project be expanded to whitelist cards, or even unlock overclock? I can provide the changes needed on the FL1 file.